Identification and recognition as the first link in the key protection standard requirements, requires the identification and sorting of the organization's business, assets, risks, etc. Similar to the identification stage of risk assessment (assets, threats, vulnerabilities), here the 'Requirements' also recommends referring to the analytical methods of GB/T 20984. For the process and methods of risk assessment, there are detailed interpretation articles in the forum, and it will not be repeated here.
Key Protection Notes Series
Key Protection Notes (Part Two): Identification and Recognition
Business identification requirements
a) Identify the key business and the external business dependent on the key business of this organization, and recognize the importance of the external business to the key business of this organization.
b) When the key business provides services to external businesses, identify the importance of the key business of this organization to external businesses.
c) Sort out the key business chain, and clarify the distribution and operation of key information infrastructure supporting the key business of this organization.
Security protection is no longer just concerned about an organization's key business system, but needs to consider various external businesses related to the business, and consider the impact of these external factors on key business, similar to BIA.
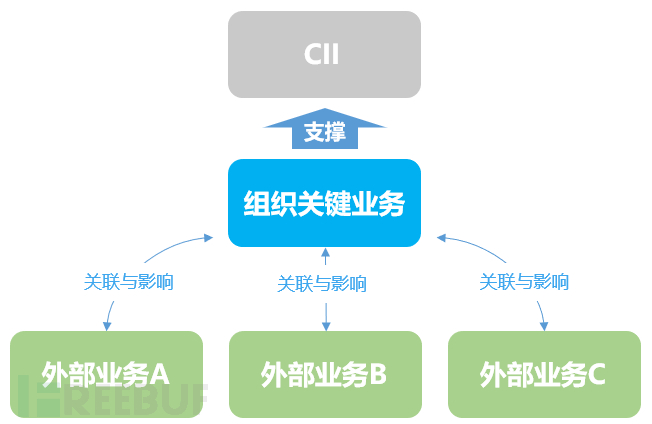
Figure 1 Organizational key business, external business, and CII impact relationship
Asset identification requirements
a) Identify the assets dependent on the key business chain, and establish a list of networks, systems, services, and other assets related to the key business chain.
b) Prioritize assets based on asset category, asset importance, and the importance of supporting business, and determine the priority of asset protection.
c) Implement automated management of related assets of key information infrastructure, and update in real-time and dynamically according to the actual situation of assets dependent on the key business chain.
The security protection emphasizes the sorting of assets dependent on CII, and classification and classification management are required, and it is required to be able to carry out automated management of assets, including identification, monitoring, early warning, and updates. Given the scale of CII's assets, the 50/50 method of tool +人工 is difficult to manage, and this proportion needs to move towards 99/1 through automated management platforms, that is, 99 automated management with 1 manual supervision.
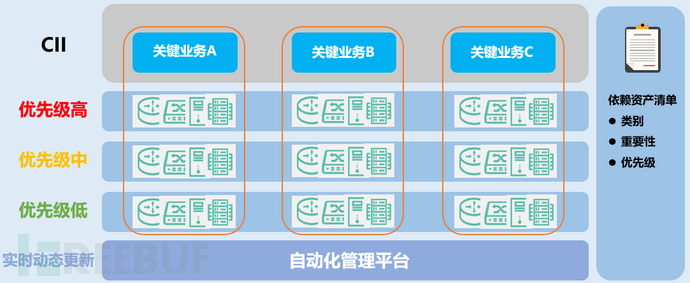
Figure 2 Automatic sorting and management of CII-dependent assets
Risk identification requirements
The operator should carry out security risk and impact analysis based on the key business chain, identify the threats, vulnerabilities, existing security control measures, and main security risk points of each link of the key business chain, determine the priority of risk disposal, and form a security risk report.
Regarding the part of risk identification, everyone should be quite familiar with it. It is basically the same set of methods as risk assessment. However, this time the scope of definition will be very large. In addition to the business chain of CII itself, it includes systems, networks, equipment, personnel, supply chain, data security and other aspects involved in external business, which is the whole business chain rather than the traditional single business. Of course, it also includes the existing control measures and control effects of each organization involved in this chain. Imagine the huge workload. <Requirements> notes that GB/T 20984 can be referred to.
Major change requirements
The operator should carry out identification work again and update the asset list in case of major changes that may affect the identification results, such as changes in network topology and business chain, and report the relevant situation to the protection department in a timely manner, and re-identify according to regulations.
This part is basically consistent with the requirements of the security protection standard, but more factors need to be considered, such as changes in the business chain. After major changes, re-identification and re-recognition should be carried out. RegardingIdentification and recognitionThe content required is not much, but the scope involved is relatively wide. However, the methodology still follows the mode of risk assessment.
The original author of this article is Yu Chen. This article is an original work of FreeBuf and is subject to the FreeBuf Original Reward Plan. Unauthorized reproduction is prohibited.
评论已关闭
