The current digital economy is leading the development of the new economy globally, and data, as a core production factor, has become a fundamental strategic resource. The digital economy is highly integrated with various industries and plays an important role in social governance, such as smart cities, smart healthcare, and smart transportation. Digital transformation is the main way for social and economic entities to develop the digital economy and has become the core driving force for promoting social and economic development. While the circulation and integration of data resources across different fields, regions, and organizations have generated huge value, external attacks on data resources and internal data abuse phenomena are not uncommon. Correspondingly, there are deficiencies in enterprises' data compliance and risk protection capabilities, and enterprise data security has become a core issue concerning national stability, social security, and public safety.
01 Current status of data security construction of domestic enterprises
With the improvement of domestic data security laws and regulatory policies, enterprises must comply with a series of compliance requirements. At the same time, facing increasingly complex cyber space threats and personal information protection, under the dual pressures of data security and data compliance, higher requirements are put forward for the systematic construction of enterprise data security. In the China Communications Standardization Association's "2021 Data Security Industry Research Report", through questionnaire surveys of data security demand parties in various industries, the current status of data security construction of domestic enterprises is demonstrated.
1.1 Analysis of data security construction needs
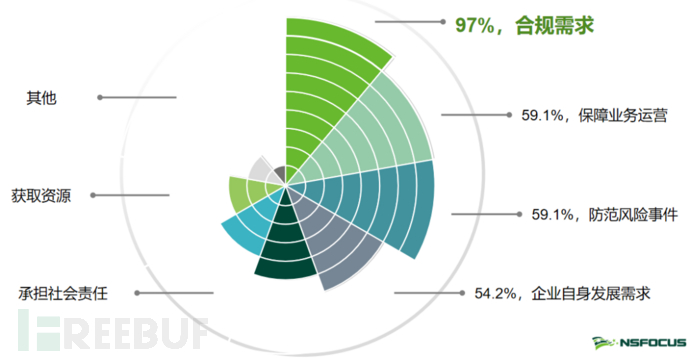
The questionnaire investigates the reasons for domestic enterprises to carry out data security capability construction, with 97% of the surveyed enterprises believing that "compliance requirements" are the main driving force for the implementation of data security capability construction. It can be seen that in recent years, the country has continuously improved its data security laws, regulations, and industry norms, and the construction of data security compliance has become an important task for most enterprises. A comprehensive data security compliance construction should start from the top-level design, define supporting definitions from the top down through strategic and corporate high-level responsibilities, and implement it from the four aspects of personnel, organization, process, and technology.
1.2 Analysis of Data Security Organizational Structure
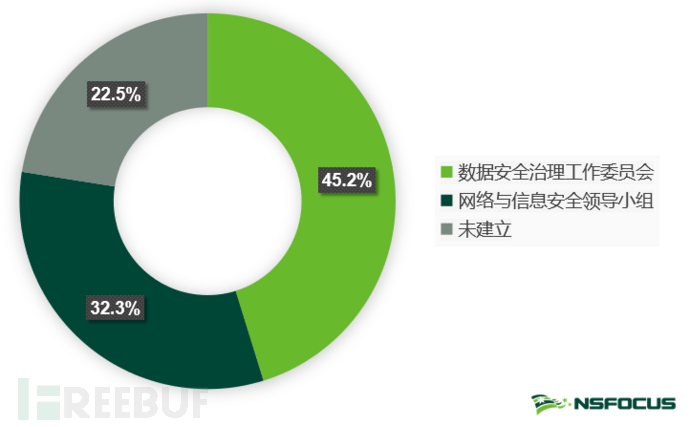
A sound organizational structure is the cornerstone for enterprises to carry out data security construction. By building a cross-level, cross-departmental, and cross-regional data security organizational structure throughout the enterprise, it can effectively break through the communication barriers between management, technology, and business departments, achieve unified data security consensus, and maximize the enthusiasm and initiative of enterprises in carrying out data security compliance construction. According to the research results, 77.5% of the surveyed enterprises have established data security governance organizations. Among them, 32.3% of enterprises have established a special data security governance work committee to lead the overall planning and construction of data security; 45.2% of enterprises choose to continue using the network and information security leading group as the leading organization for data security work, and establish a data security management team to ensure the effective implementation of related work; in addition, there are still 22.5% of enterprises that have not established a clear data security organizational structure. In the absence of such an organization, it is easy to lead to overlapping rights and responsibilities, unclear boundaries, and obstacles in promoting data security construction, increasing data security risks.
1.3 Analysis of Data Security Technology Application
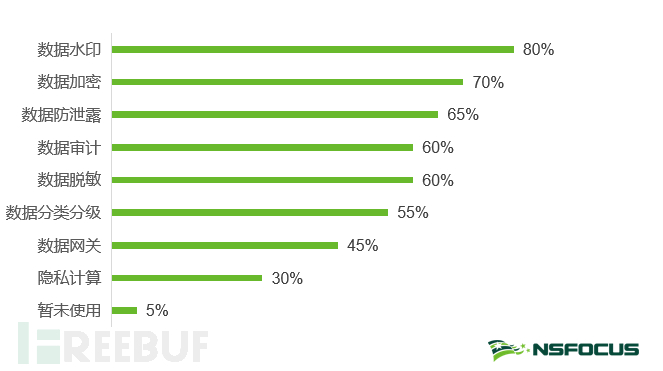
Technical tools are an effective means to implement data security management requirements and the foundation of enterprise data security capability construction. According to the statistics of enterprise application of data security technology, 95% of enterprises have at least applied one data security key technology, indicating that enterprises have a high maturity in the application of data security single-point technology. Among them, 'data watermarking', 'data encryption', and 'data leakage prevention' are widely used in enterprises.
1.4 Analysis of Data Security Pain Points
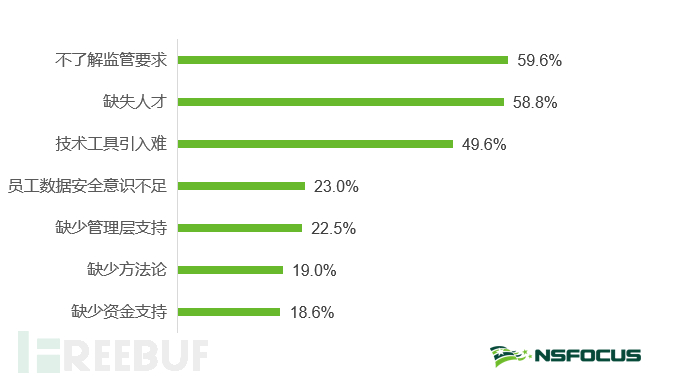
Enterprises face many pain points in the process of carrying out data security construction. According to the research results, 59.6% of enterprises believe that 'not understanding regulatory requirements' is the biggest problem, indicating that the detailed interpretation of various regulations and regulatory policies and industry guidance are urgently needed to be promoted. In addition, enterprises need to combine their business characteristics and effectively transform compliance documents into their own management systems, including strategic guidelines, security strategies, and control processes, so that data security can be better implemented and implemented.
1.5 Analysis of Data Security Service Methods
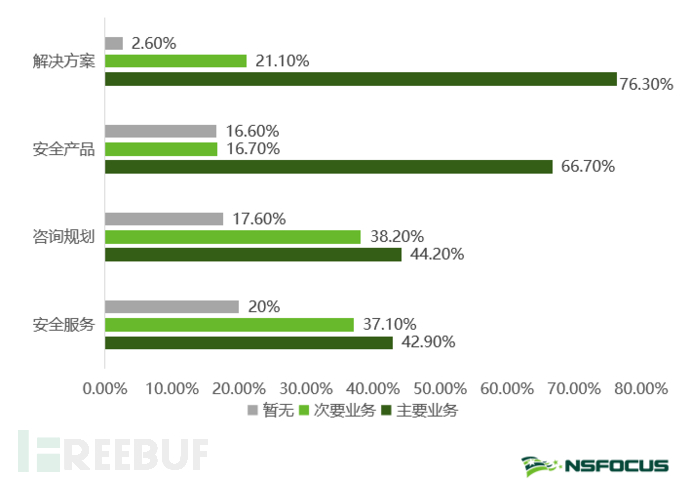
Data security solutions, security products, and consulting planning are the three main business forms provided by security suppliers. According to the research results, 76.3% of enterprises have implemented solutions in their main business, compared to security products (accounting for 66.7%), the overall solution has become a new field for suppliers to compete in, reflecting that enterprises have begun to gradually attach importance to the perfect match between data security and business development, and lay out the development trend of systematic data security construction. In addition, the proportions of consulting planning and security services are 44.2% and 42.9% respectively, reflecting the increased attention of enterprises to security consulting planning and security services.
02 Domestic data security legislation and regulatory situation
In recent years, the country has carried out systematic top-level design for data security and personal information protection, constructing the legal framework for cyberspace security, data security, and personal information protection in parallel with the Cybersecurity Law, the Data Security Law, and the Personal Information Protection Law, as well as the intensive issuance of data security policies and standards by various ministries and local governments. Based on fully protecting the rights and interests of various government agencies, enterprises, and citizens, it has put forward higher requirements for enterprises' data compliance work, and it is imperative to build a corresponding data compliance system.
At the same time, various industry authorities or regulators such as the Cyberspace Administration of China, the Ministry of Industry and Information Technology, the Ministry of Public Security, the China Banking and Insurance Regulatory Commission, and the National Health Commission have released strong regulatory signals, and have shown a trend of normalization in law enforcement. They are accelerating the deployment of data security management pilot projects in various fields, enhancing the law enforcement capacity of administrative law enforcement, strengthening the training of administrative law enforcement personnel and enterprises on data security, and enhancing technical capabilities in data security monitoring, risk reporting, and emergency event disposal, so as to comprehensively improve the comprehensive regulatory capabilities of data security, and guide enterprises to carry out data security management in compliance.
03 Data security compliance construction
Data security compliance can generally be divided into the following types:
Laws and regulations: such as the Cybersecurity Law, the Data Security Law, and the Personal Information Protection Law;
Certification/Testing: such as the Data Security Maturity Model (DSMM) certification;
Audit requirements: such as the SOX audit of U.S.-listed companies;
Regulatory requirements: such as inspection documents issued by industry authorities or regulators such as the Cyberspace Administration of China and the Ministry of Industry and Information Technology.
Note: If the business of the enterprise involves cross-border data scenarios, it must strictly comply with the local national laws and regulations. For example, if a company develops an APP to provide services to users in the European Union, and collects personal information of EU users, it must strictly comply with the terms of the GDPR.
What specific compliance requirements should enterprises compare with? It needs to be judged according to their own business actual needs. Non-compliance may face penalties from regulatory authorities, so non-compliance is also a risk. We can combine data security compliance with risk management to better support policy guidelines and principles in data security governance, and effectively implement these guidelines and principles in the business process of the entire data lifecycle.
The 'One Center, Four Steps' method refers to improving and continuously enhancing the enterprise's data security compliance capabilities in a cyclic manner, with a focus on data security policy, through four steps: policy risk assessment, integration of process risk improvement, external certification risk measurement, and policy improvement risk summary.
Establish policies, risk assessment: By referring to laws and regulations, regulatory requirements, and industry standards, external compliance requirements are transformed into the internal data security management system of the enterprise, forming a four-level document system architecture (first level: policy and guidelines; second level: standards and specifications; third level: operation guidelines/processes; fourth level: template lists), and it is used as the basis for internal risk compliance evaluation.
Integrate into the process, risk improvement: Integrating the data security management system with all stages of the data life cycle, and implementing it in the business process, is the best means to control risks.
External certification, risk measurement: Through external compliance certification or risk evaluation, objectively make the enterprise aware of its own security status and compliance gap. Strengthen the means of routine risk audit, timely find out the risks faced by the data in the business activities of the enterprise, take corresponding risk control measures according to the risk value and priority, control the risk within an acceptable range, and improve the overall data security protection capability.
Policy improvement, risk summary: Summarize the effectiveness of risk assessment to promote the continuous improvement of data security compliance policies.
04 Example for reference of data security compliance evaluation
Data security compliance evaluation mainly uses various methods such as document verification, advisor interviews, system demonstrations, and evaluation and verification to assess the compliance of the safeguard measures of enterprises in various data processing activities and data-bearing system platforms. Starting from the aspects of general management and full life cycle management, the important management measures, key technical measures, and judgment criteria involved in the evaluation of each indicator item are clarified, the compliance baseline of the evaluated items is clarified, in order to improve the level of enterprise data security management and related technical support measures.
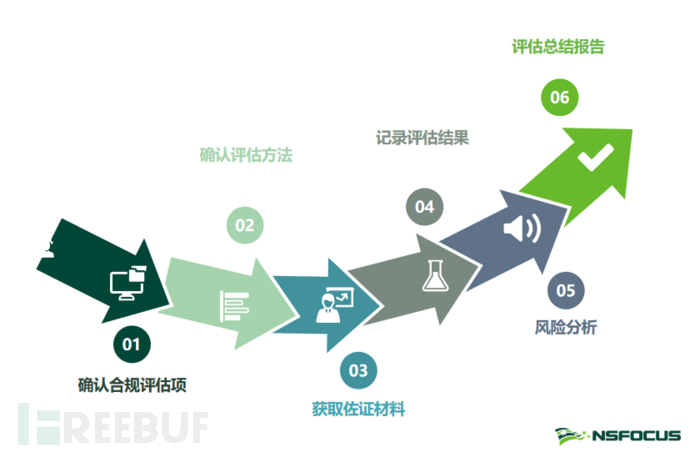
Determine the compliance evaluation items: Before the implementation of the evaluation work, the evaluators will define the scope of the evaluation object based on laws and regulations, reference regulatory requirements, and the actual situation of the enterprise, determine the life cycle stages involved in the data, and the scope of applications, systems, and platforms involved in each stage. At the same time, the 'Data Security Compliance Evaluation Table' is formulated, focusing on organizing the data security compliance evaluation items required by the enterprise, ensuring the completeness and consistency of the overall compliance evaluation plan.
Confirm the evaluation method: Based on the guidance of the best practices in the industry and rich compliance evaluation implementation experience, combined with the actual situation of the enterprise, the optimal inspection method for each evaluation item is determined, and the evaluation work is carried out according to the evaluation method. For example, by using tool scanning, document verification, personnel interviews, and functional demonstrations, the evaluation items in the 'Data Security Compliance Evaluation Table' are inspected and evaluated item by item.
Gather evidence materials: For each evaluation item, the evaluator will record and retain the evidence required for the evaluation item, including but not limited to document files, photo records, tool scanning records, system screenshots, manual inspection results, and interview records. The original files of the evidence materials are all marked with specific corresponding evaluation item numbers, evaluation objects, evaluation time, and acquisition methods, etc.
Recording Evaluation Results: After completing the evaluation work for each evaluation item based on the 'Data Security Compliance Evaluation Table', the evaluation personnel will check the evidence for each evaluation item, determine the compliance status of each evaluation item based on the evidence, and record it in the 'Data Security Compliance Evaluation Table'.
Risk Analysis: After completing the inspection work, the evaluation team will, based on the records of the inspection items and evidence, as well as the 'Data Security Compliance Evaluation Table' that indicates the compliance status, comprehensively analyze and organize the compliance status of the evaluation object and the data security risks they face. By analyzing the harmfulness and possibility of the existing data security risks, a data security risk matrix is generated. In response to the existing security issues of the evaluation object, the evaluation team will consider the factors for the implementation of security improvements to facilitate the smallest unit of improvement for the enterprise, analyze the potential safety hazards in each unit, and combine with the data security risk matrix to select appropriate control measures, following a reasonable priority to propose security improvement suggestions.
Evaluation Summary Report: Based on the organization and summarization of the evaluation results, combined with data security risk analysis and security improvement suggestions, the evaluation team will compile a 'Data Security Compliance Evaluation Report' that meets regulatory requirements, including but not limited to the introduction of the basic situation of data security of the evaluation object, the introduction of the data security compliance evaluation process, the data security evaluation matrix, the analysis of the security issues of the evaluation object, improvement suggestions, implementation of improvement, review situation, and signature, etc.
05 Future Outlook
Compliance with legal and industry regulations is the bottom line for protecting enterprise data security. Frequent incidents such as the abuse of personal privacy, leakage of important corporate information, and illegal cross-border data, both at home and abroad, not only damage the economic interests and public reputation of enterprises, but also may face legal charges such as lawsuits. It is believed that most corporate executives have gradually realized the severe risks behind digital transformation, and enterprises need to strengthen data security compliance awareness and continue to invest in relevant resources (such as funds, technology, and personnel), through data security compliance assessment, can effectively help enterprises establish and improve the data security compliance system, and has a tremendous driving force for protecting enterprise data rights and improving data security risk protection capabilities.
评论已关闭