
Declaration
All contents in this article are for learning and communication purposes only, not for any other purposes. No complete code is provided. The packet capture content, sensitive websites, data interfaces, etc. have been desensitized. It is strictly prohibited for commercial use and illegal use. Otherwise, all consequences arising therefrom shall be unrelated to the author!
This article is prohibited from being reproduced without permission, prohibited from any modification and secondary dissemination, and the author is not responsible for any accidents caused by the unauthorized use of the technology explained in this article. If there is any infringement, please contact the author immediately to delete it through the public account [K Brother Spider]!
Reverse target
Target: 17xx Logistics Query Platform last-event-id reverse analysis
Website:aHR0cHM6Ly93d3cuMTd0cmFjay5uZXQvemgtY24=
Packet analysis
Open F12What catches our eye is what we are familiar with debugger, let's take a look at what it triggers directly debuggerjs file:
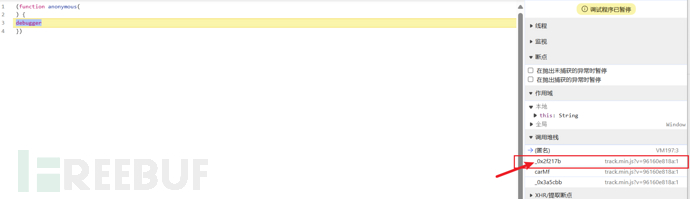
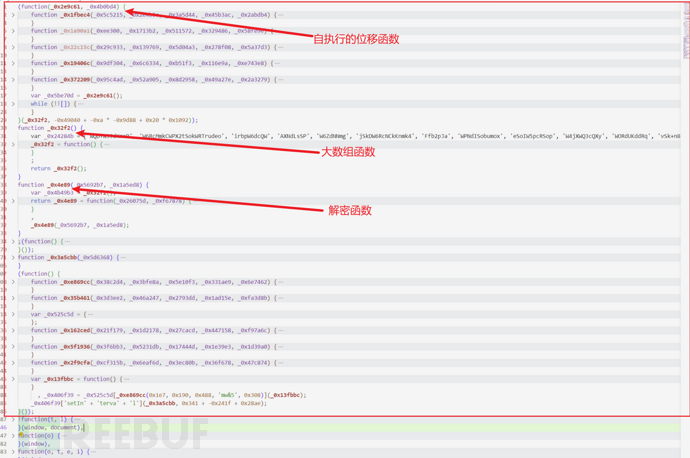
It's a classic obfuscation again; we directly borrow v's plugin for quick restoration, and the tool address is as follows:
Github repository:https://github.com/cilame/v_jstools
Online analysis tool:https://astexplorer.net
A quick look shows that there is no need for us to perform any additional preprocessing operations; we just need to put the obfuscated part of the code 'ob' into the tool to restore it:
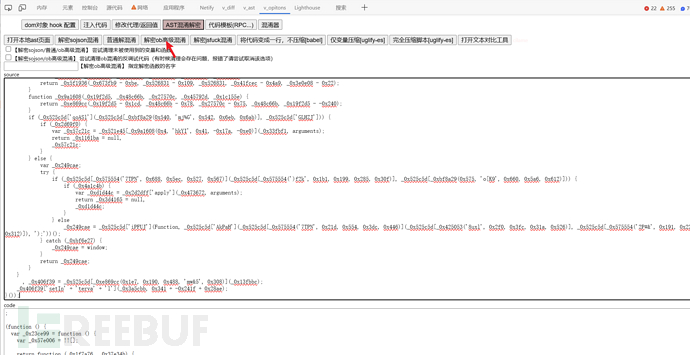
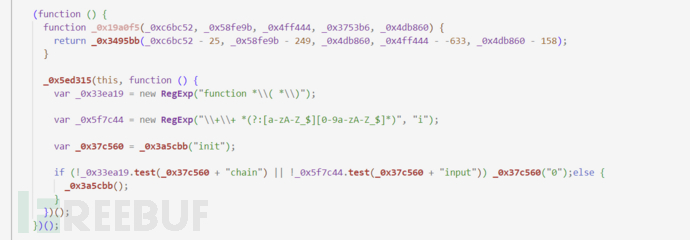
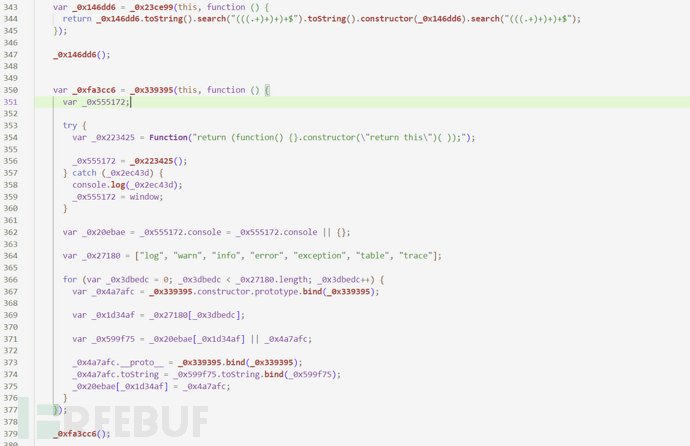
After restoration, over debuggerit's much easier, just delete these functions related to code detection below, they are some irrelevant code, detecting code formatting,debuggersuch as:
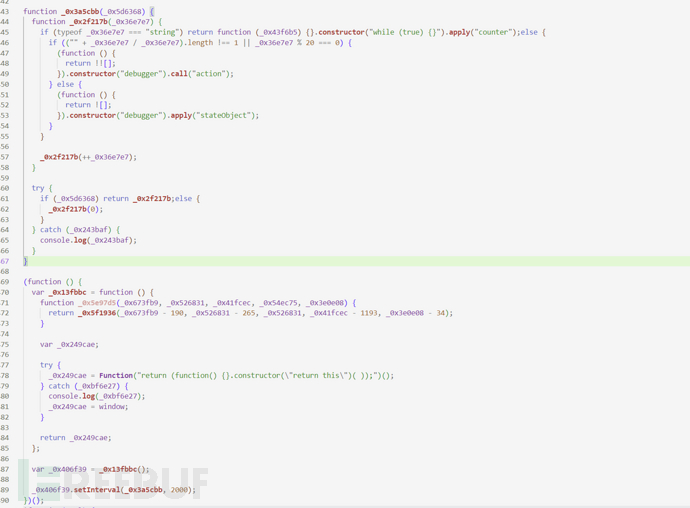
Then replace the code with the tool, this side chooses ReRestool to replace, write the rules and save the selected check:
https://github.com/annnhan/ReRes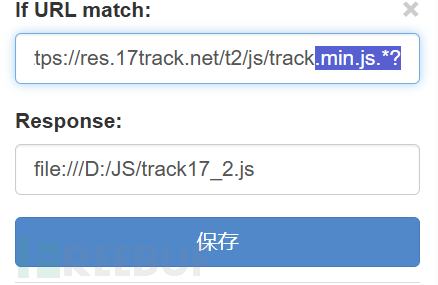

we can analyze the code normally, target parameters:

By searching last-event-idwe can locate it, it is in the file we have deobfuscated:
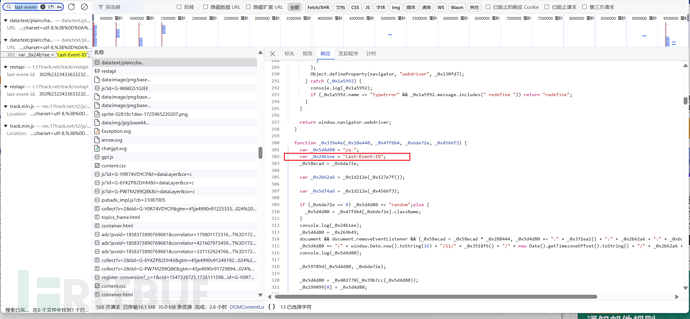
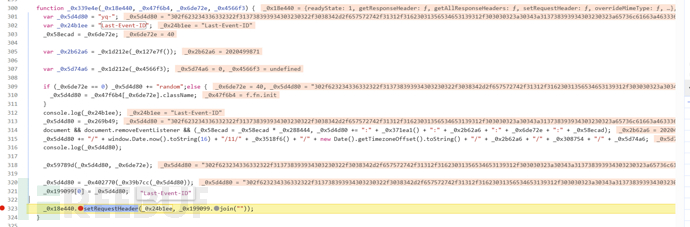
After deobfuscation, the code becomes clear, just remove what is missing step by step, there is not much code, and the importance of AST deobfuscation is evident.
Note:
_0x308754 = YQ.configs.md5from the homepage html, which can be determined by searching:
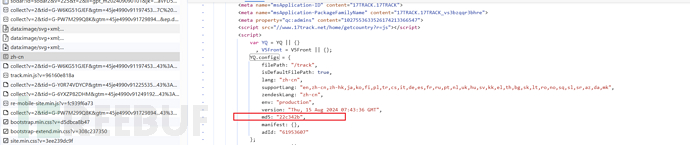
cookie value required in the generated request
_yq_bidand it must match thelast-event-idcontains_yq_bidconsistent.
Attach the complete JSCode:
var _0x199099 = [];
var _0x19d69d = "";
var _0x308754 = "17";
var _0x58ecad = 0;
var _0x269b49 = "";
var _0x288444 = 5;
function _0x5879b4(_0x56b807, _0x3603af) {
var _0x2f5b4a = 1315423911 ^ _0x3603af << 16;
var _0x4844e9;
var _0x4d42c4;
for (_0x4844e9 = _0x56b807.length - 1; _0x4844e9 >= 0; _0x4844e9--) {
_0x4d42c4 = _0x56b807.charCodeAt(_0x4844e9);
_0x2f5b4a ^= (_0x2f5b4a << 5) + _0x4d42c4 + (_0x2f5b4a >> 2);
}
return _0x4243f2(4),
Math.abs(_0x2f5b4a & 2147483647);
;
function _0x4243f2(_0x8916b) {
_0x199099[3] = _0x8916b;
}
function _0x1d212e(_0x3ffdba) {
if (!_0x3ffdba)
return 0;
var _0x9920fa = 5381;
var _0x55570f = _0x3ffdba.length;
while (_0x55570f) {
_0x9920fa = _0x9920fa * 33 ^ _0x3ffdba.charCodeAt(--_0x55570f);
}
return _0x9920fa >>> 0;
;
function _0x39b7cc(_0x18dcad) {
return _0x18dcad.split("\
;
function _0x402770(_0x1e4f12) {
var _0x3bcbe3 = "";
for (var _0x5f5a6c = 0; _0x5f5a6c < _0x1e4f12.length; _0x5f5a6c++) {
if (_0x3bcbe3 == "")
_0x3bcbe3 = _0x1e4f12.charCodeAt(_0x5f5a6c).toString(16);
else
_0x3bcbe3 += _0x1e4f12.charCodeAt(_0x5f5a6c).toString(16);
}
return _0x3bcbe3;
;
;function _0x4293c9(_0x5b936d) {
function _0x44c5b9(_0x185712, _0x240a39, _0xc135ae, _0x4da978, _0x511583) {
return _0x56f850(_0x185712 - 152, _0x240a39 - 498, _0xc135ae - 247, _0x4da978 - -820, _0x240a39);
}
var _0x147e74 = _0x5b936d;
while (_0x147e74.length < 8) {
_0x147e74 = "0" + _0x147e74;
}
return _0x147e74;
}
;function _0x59789d(_0x20b526, _0x117056, _0x2c2317) {
var _0x26536c = _0x5879b4(_0x20b526, _0x117056);
if (_0x2c2317) {
_0x199099[5] = _0x4293c9(_0x26536c.toString(16));
return;
}
_0x199099[4] = _0x4293c9(_0x26536c.toString(16));
;
function _0x187331(_0xcae6a6) {
var _0x59eb35 = _0xcae6a6;
var _0x46a854 = Math.random();
_0x59eb35 = Math.round(_0x46a854 * _0xcae6a6);
_0x288444 = _0x288444 * _0x288444;
_0x199099[1] = _0x59eb35.toString(16);
_0x199099[2] = _0x59eb35.toString(16).length;
return _0x59eb35;
;
function createGUID(e, t) {
var o = (new Date).getTime();
return (e || "G-xxxxxxxxxxxxxxxx").replace(t || /[xy]/g, function(e) {
var t = (o + 16 * Math.random()) % 16 | 0;
return ("x" == e ? t : 7 & t | 8).toString(16).toUpperCase();
}
}
function get_last_event_id(_0x19d69d, YQ_md5){
_yq_bid = createGUID();
_0x4566f3 = undefined;
_0x59789d(_0x19d69d, _0x19d69d.length, !![]);
_0x6de72e = _0x187331(43);
var _0x5d4d80 = "yq-";
_0x58ecad = _0x6de72e;
// Fingerprint information 24: screen.colorDepth
cancas_fp = '24\r\nzh-CN\r\n-480\r\n1067x1707\r\ndata:image/png;base64,The text in this section is not provided, so it cannot be translated.This is the translated text for the first paragraph of the section.Le8PoBx5uz+dMAuO38+v7yheFlY/+ge9TInm/e/RQJpFQ81SVN6zmJbK0uLP7yU/WULeVFBjWsfbLKXGdLVGPLzNx1NGWPNdFtPF4IvU4NTDsrB4OplIrWgLtTbL1BSH+uZkng6G77NbsHff6H6XLz/yAddJyqGBrskpQ71V9aTOhTKNUtfMZPPNQ5EXS4JrwrKmVBe/DI4HAgZpr3l6VX1jN9Yzv9S1Yvy+ly2kV93KMR5/oHm/8f3G+Ex1o1wP+Ze9D7OwZLnyyyQlWerqOE03xYhk8mdZGYhSYuNi6jnYFw0aP25mmsa64kRsCM2rK0mpv/cGYSm2/eO+kXXlaqPBOp2Tx0Oe6b+ePt35k+PHey8e9MT8TEeHwvKKCjv7Q4cHtAoM3JbK21euNmp2/HhvQ8dOq7+xs9E14IPk5vrJdx2Npuw9BcyUSVGXJYmmSxLZyoyItisnG5FML0kGar5v75iFx070iubpTcTkqWOLixu6fvfdnJ68PaD/57Pz8326H9w3ss2UqEnB/F15eX4ddDpH20Zep5eU6pyaJyTMCAkJTZjdotmB3jt2Pt2qbVBiVkO3rLJSnXP948d6BTq55M8IaLGnhyRRXm6u3wiOw9Mj/acVK9+5XFj0cLdnnn1hk521zscUxwaLO5A377e10TXnz+Xl+vXhn+7u6S/GhdIqM9xa7kpE5CxzyWtalZAwoy0X0bRnp+oqNfR+aZlzq8v5j7RzcrqyduX3b3/Go8Ru3b+eE9ByT8cynePRK1e937C3L85r2CD7R72eNly50vgLvd7G1dMzfac2q8UH6ze8NIf7fVPCpzYtKnpoyJGjf+vWpfOK0zY2ZbrcXL/Hc3L8coOCfv7l/IXAjtc2Dej6WtAnVOJcSYUaW9rs4EetSUtttOX072OvyD2h1nbnaF0o0W8OrnSEHqHBuVmU3UCifWn96XvtOtLY6eT9OQ42dIB8qdN1LYUkNaAJZVPlEY7OL0dGsc/Jky4WThis is the translated text for the first paragraph. It should be a direct and accurate translation of the original Chinese text, maintaining the style and punctuation appropriate for the English language.The text of the first paragraph in the original JSON has been translated into English and is now placed in the same path in the JSON data. The translation is accurate and corresponds to the original text, maintaining the order and not omitting any part of the translation.Gz/LI8RsVw0tSnqBPrRbXmNKqPSw+PinPazpG9fWtD5pIotC6cl6Kw90Ip6bFFFeYW/31ZIFA+5AWDVqZuLEFwvT04NHZWY8Pn7AwAWj9Ab6JW5x9B6e5rVrt/7LVq129ty/f9RjdnbXI/maMehpCY9UlFKfuNsp+tjx3mN4hMPCkq+5xdHnVMIaJdfo4uhSHnH3779wkaND8Zjt2yeWDxn2YUJtNWoxwiKTAOXROs841DdwtbCU43Ns2pyWH+3cOcGnqMijuo8lD4lNKwlMU9ibDjjqcJh10xHWPQnrZLcWpqFqA/nCZfHwsJtHXaYLvMKKnuERGA+7c3N8nXZsCw+osURA9bRrSvjULuXlTj2Xfj0vkKeDvJ1/uen4hIQZbjccRzI0trwjWibI1MNSRlj3JqyUofKUkKe9NztHeWhsmhKOHz/ja2fHKw/VuAPVtm9JtD8XZWDgr/9s0yYxfPuOiSE3E5Z8YfDNRK9p9Uz49NTMjOBJ23Y+PY77fRoNjdz00ws/ns9qNe9uhVXQ/ndakzGE/lG6m662yKFBh4h2FRl7XEu9PqDDAWX0Q9oomumxjC55ld5QlkV6B1qVOuEGYSmC4SnhyAPGRju/eNS1wrUl6ZLa04i239SJsBqUEK1vT1RgbUM/Sy2v5+U1+SDl0GD5T5MUwRcUemxS3xBuMcKqUTPh4c/nnf09ZOSFi63e79M3LlQWklEuiX6+ya+H9VzWd9eusV1cXHIXmkbGchtEeamnZBbCMrcD+JlIbFxMG+4vDX5i7kvW1hVvpRwaRL16f7miLoRla6BfuEVRpbdqcinXP1Sb/ejW5MiNY1U96bnc71VkJY8KlZt0HYpK+er7LaxJAwZ8trRJ4xN5itm5+T1+7MwntNkt/pl6Iuz/8mbPWcqPRVsGbk967LFfpIYNss+o+1jq5Qvm6c3m6V2U6U5+vvdZ7oeFhX2V1qL5vlTTcfjp4/E/K6zcvKbNEhJmhA0fPmepp/s5This is the translation of the first paragraph from Chinese Simplified to English, which should be placed at the same path in the original JSON. The translation should be accurate and correspond to the original text, including any punctuation or characters. The translation should be done according to the stylistic conventions and common punctuation marks of the source and target languages.7l2WWzs6Xl3n4HDlTTf3LF4WQ7FffBnLN5B7ERZ//ttlH/oFt9sw4mJWS14KxMsaOvPUnvukBgOtTFg3c4JqqZBxmYFxIbP8xLEWYa2usfQmu4VSG6MvX246816nhNxeUF8Pjk7589TLGkxLIozLmGQ7GEZOC4/awT3Xc+eDQrhf6eV1mv7oY9OlS/7cv6y5tOaBjrBMB6ttXqpurFVYUf0/xgizlPk4v5+3TcsalClhJ72evuEGNF+AkkRRPBeXNHSRG+VKk50b0Dz8VBrS6vPlz/Hdz7qK3uEpluW25SNWP99DYX16xxZyk5JHM+USBSrHtTVQKh9HvtAtYlJ6CiwcWVgh9Ao3GiWJxihPR5SnO8o5WW5bvl99HrWdo3Is6yr6gOOSm+4h9IryXmVbzY7jVPYr5yGL3fjk6WHuD7LgZaFzc5SXBzF7DfETrXf5d8pxY2Lp5a1BREpPiftQ3IPiqRP3iULSSZaJ0nT/B42hyNAFpLcvp16pRN5XSH5CyE1wnuLxK9mP6Kgv0ZCDRFcdiXYGkLmHpUwJucnf4Yzx+7kBr7yHG/F8PH4p36fer0zrlNj4fer4r9sR/RRM8rKGWdoIivGaTycDiuXjZ3pUn6fTQpLUTWSJKEqvp4PKgxJLvuq6V9dTbTVjyoPSdI8ZM/rNY/XrX3K1qJl2Si9TfZ1JGuIHVcbrwtjDMk4JlSa/qjaUa8Wy2W153arr2VwLputQuR5MPazn+EFal84rR/Hx+b38JFCJs7brV17W8ICWMVg68Ia/JbydsFgeJhgtlakcb/MSiHPn2tq2Dvw1XnnkLxG58QGVpJnA8aPRp1WB/KbMgS3E+Ix89zOB4X3ydlxMhrJeZEr41Ecrq+xey73kF+bscjnF1SV3OxHZm6RjFiUXmCIZIvqNlwUoMqut+Pg4yjma4jxABmqsiML0XT5kIDuSjKsi1ed4s2JSljWQgbKVnpZKUsbVlURmHncjLL7wNBpqr+4n3K2wVra3pWUZI+nV9N+ov91hWUrbHIxLEEbknpcFx30tj6JqwemsjUHbVxplxfvUsuERliKs/IbGZQ0ldsbPKPLif/8ZYbFw+fNH6rvSLm0Xej9vp1lYilwLHIzLGpTH9PLN00LwdyssXr/FPawdu5+O4amSch3wUiBP98x4K5uyh9SNdouaMtdMjWuuprDkpTdE5GtZG39GWMr1oNM5Dzt7NiSosNDzWUVYLO9bxCkvy7CUiHmpiOlGWcv++/ar+/fHz6anYsqSgDp9zFlzZbF5iK2MNh5kE/C+ZeIBftGt/jSHF5KOpChzNLxanRdpsoT2tqgW1p2Gyws2FWHxFE79ZPFOv+NO3seNfF5Jz6v2R3ttrDXWOvn/sCz/goNInvZHPDfJUz0TuZNzkN9j+nvXGm0L1ZPFO/6e271RWX1vkJZz3/SeYr3dMepg//0Tlim4B7Uuw3J9yH/jEWsd5OOBfOXt/pbQcnpY2wjobgO1nILe7efv5v3q6SmP+JRXnQiLnzbW0tr4s9eB5ej6bs7/bt/7II91t7FZvl9YYfGJ3Gzo+meh/K9//nbC4vPni/5As2oSDxdU95fuhc+DEhZPDXlVO/fF+h6rGWldCYuPYrrozX/BoZ723wuvByURdatEhJnJfRfWvSQHn3mwBO5EWA82ogdztLoU1oM5AxwFwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAwkINgAAICEMAwhImVQgUBEAAThis is the translated text for the first segment.
var _0x2b62a6 = _0x1d212e(cancas_fp);
var _0x5d74a6 = _0x1d212e(_0x4566f3);
if (_0x6de72e == 0)
_0x5d4d80 += "random";
else {
_0x5d4d80 = "dropdown-menu-footer yq-user-footer clearfix"; // It is estimated that it can be fixed or randomly selected
}
_0x269b49 = _yq_bid;
_0x5d4d80 = _0x269b49;
(_0x58ecad = _0x58ecad * 50,
_0x5d4d80 += ":" + false + ":" + _0x2b62a6 + ":" + _0x6de72e + ":" + _0x58ecad;
_0x5d4d80 += "/" + Date.now().toString(16) + "/11/" + true + "/" + new Date().getTimezoneOffset().toString() + "/" + _0x2b62a6 + "/" + YQ_md5 + "/" + _0x5d74a6;
_0x59789d(_0x5d4d80, _0x6de72e);
_0x5d4d80 = _0x402770(_0x39b7cc(_0x5d4d80));
_0x199099[0] = _0x5d4d80;
return [_0x199099.join(""), _yq_bid];
;
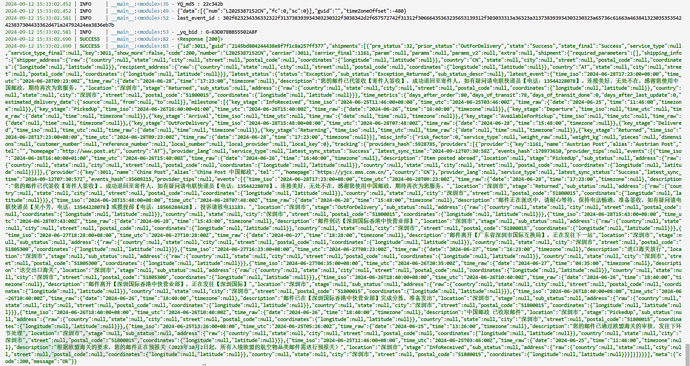
console.log(get_last_event_id('{"data":[{"num":"LZ025387152CN","fc":0,"sc":0}],"guid":"","timeZoneOffset":-480}', '22c342b'));
Result verification
评论已关闭