Everyone knows that there is no free lunch in the world, but when people truly encounter a free lunch, it is difficult to resist the**temptation in their hearts. Recently, a group of 'fruit bloggers' has appeared on social platforms, mainly taking advantage of users' desire to get a bargain, and attracting users to join group chats by offering reasons such as 'promoting online stores and free distribution of fruit in abundance'. After that, taking advantage of people's desire to make easy money online, they诱导users to download a certain app and recharge to complete tasks, thus gradually luring users to recharge a large amount of money. Finally, they delay the refund and withdrawal to users for various reasons, and implement fraud.
A few days ago, while browsing microblogs, I found a group of bloggers using microblog to promote free fruit distribution. Out of curiosity, I followed one of the bloggers and entered a group chat as per his instructions. The group owner led users to download an APP called 'Farmer Chat' to do tasks and earn commissions under the disguise of the first benefit: free fruit distribution. At that time, I realized it was a scam and searched online, and indeed, many users had been deceived and defrauded of a large amount of money.
 Figure 1-1 Users defrauded of a large amount of money
Figure 1-1 Users defrauded of a large amount of money
First, scam process
Fruit bloggers promote free fruit distribution through microblog to attract users to consult, guide users to join the group chat, gain user trust, and then launch benefits in the group to induce users to download the APP to help the orchard do tasks and earn commissions. After users download the APP, they operate under the guidance of customer service. At first, completing a task can indeed return the principal and commission, but when users start to recharge more and more after tasting the sweetness, the other party delays or refuses to return the principal and commission for various reasons, and users are deceived. The scam process is shown in the figure below:
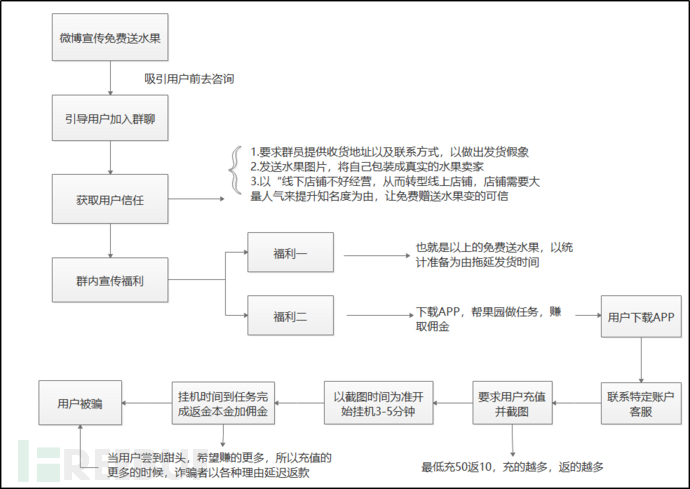 Figure 1-2 Scam implementation process diagram
Figure 1-2 Scam implementation process diagram
Second, scam tactics
2.1 Microblog advertising promotion, attract attention
Attract user attention through microblog promotion of free fruit distribution, and make users主动contact them.
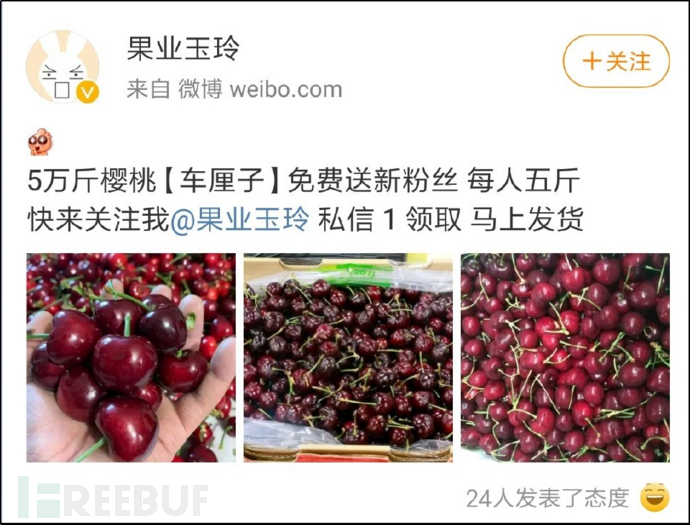 Figure 2-1 Microblog promotion
Figure 2-1 Microblog promotion
2.2 Join the group chat, induce to download APP
Use the pretext of 'Many people are applying, and it is to avoid registration errors' to guide users to join the group chat for unified user management.
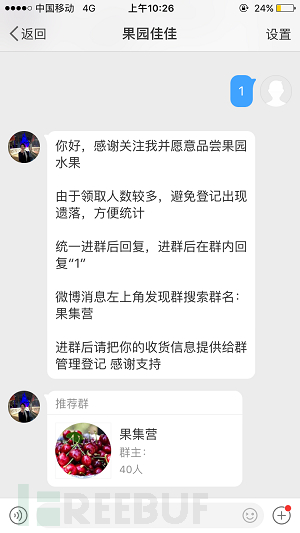 Figure 2-2 Guide users to enter the group chat
Figure 2-2 Guide users to enter the group chat
After entering the group, the group owner uses the following three methods to enhance the user's trust level:
Require group members to provide shipping address and contact information to create a false impression of shipment.
Send fruit pictures to package themselves as a real fruit seller.
Use the pretext of 'The offline store is not easy to operate, so it has transformed into an online store. The store needs a lot of popularity to improve its reputation, so it has launched a free fruit distribution activity' to make group members believe that the free fruit distribution is just their marketing strategy and not a scam.
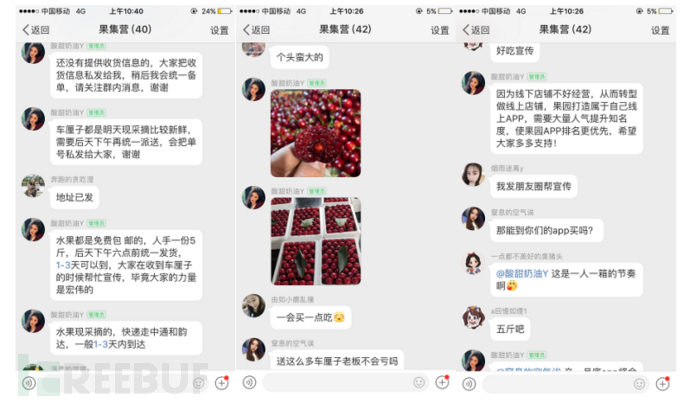 Figure 2-3 Gain user trust
Figure 2-3 Gain user trust
Once the trust of group members is gained, they can start to fish in troubled waters. The group owner began to distribute benefits within the group:
Benefit one: Free fruits are given away, and specific shipping time is given.
Benefit two: Use the pretext of 'The APP is about to be listed, help the orchard improve ranking and popularity' to guide group members to download the APP and earn commissions by doing tasks.
Provide APP download links, induce users to install, and the following two applications are scam APPs.
 Figure 2-4 Scam APP icon
Figure 2-4 Scam APP icon
Under the pretext of 'To prevent customers from randomly clicking and submitting, and not completing tasks, leading to no one doing them', users are required to first make a deposit and pay for the task themselves.
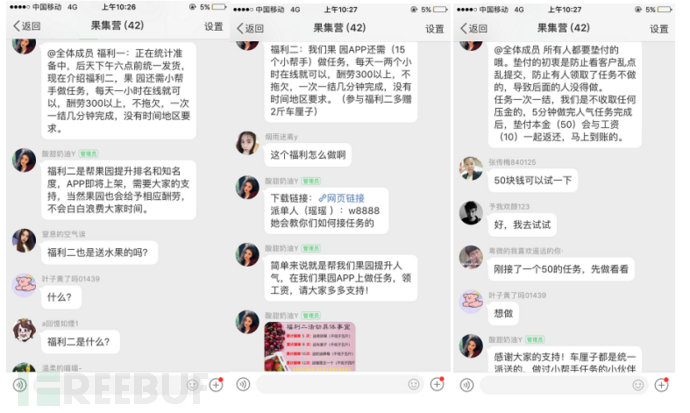 Figure 2-5 Inducing users to do tasks
Figure 2-5 Inducing users to do tasks
Many 'Tuo' were arranged in the group, and these people shared their successful refund screenshots in the group to make group members believe in the authenticity of the matter more, and make group members truly believe that simple minutes of hanging can earn commissions.
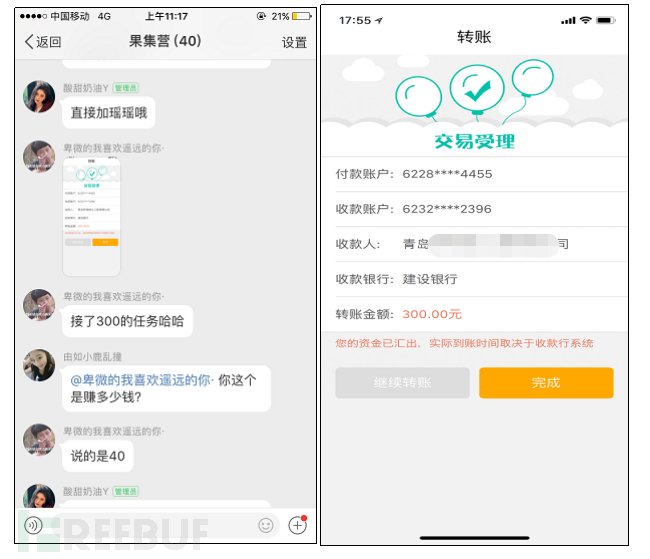
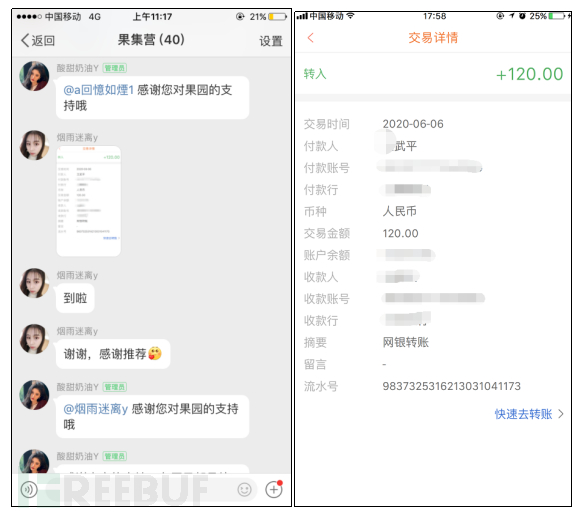 Figure 2-6 Sharing withdrawal screenshot by 'Tuo' in the group
Figure 2-6 Sharing withdrawal screenshot by 'Tuo' in the group
2.3 Recharge, hang up, refund and withdrawal
Group members use the App under the guidance of the group owner, contact customer service for specific accounts, and are guided by customer service to complete the next task operation.
 Figure 2-7 Contact Customer Service Steps
Figure 2-7 Contact Customer Service Steps
Task process: register as a member - recharge screenshot - hang up - refund and withdraw.
The task is very simple: after receiving the task, just hang up for 3-4 minutes to get a refund and withdraw the commission. The minimum recharge is 50, and the refund is 60, including a commission of 10 yuan. The more you recharge, the more you get back. After users get some sweet profits at the beginning, they will recharge more under the guidance of customer service. When the amount of recharge reaches a certain amount, the other party will refuse or delay the refund for various reasons. In the end, all your money will fall into the other party's pocket, and you will no longer be able to contact them.
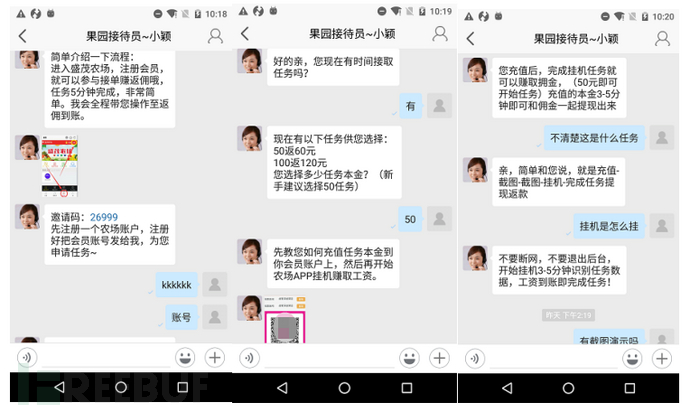 Figure 2-8 Task Process
Figure 2-8 Task Process
User registration, recharge, and hanging up are all completed on a **page within the application, showing that this fraudulent process is closely related to the network. On one hand, the other party wants to defraud users' money by doing tasks, and on the other hand, it induces users to recharge for online gambling. However, no matter which aspect, it is a deep trap.
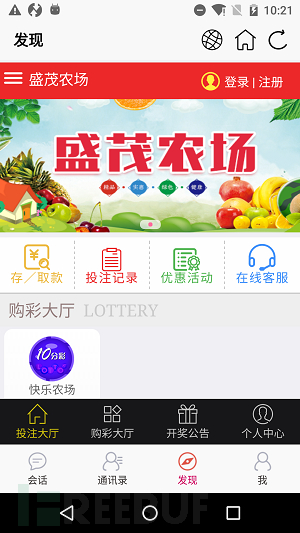 Figure 2-9 **Application in APP
Figure 2-9 **Application in APP
3. Analysis of Fraudulent APPs
Sample Information:
| Sample MD5 | 915528bbb74e710c6c9fe5bcac4e03f0 |
|---|---|
| Application Package Name | cn.kkim.nongchangliaoba |
| Signature Information | CN=c,OU=c,O=c,L=c,ST=c,C=CN |
 |
|
The main code is concentrated in the package named cn.lanhu.im, and the file structure is shown in the figure below.
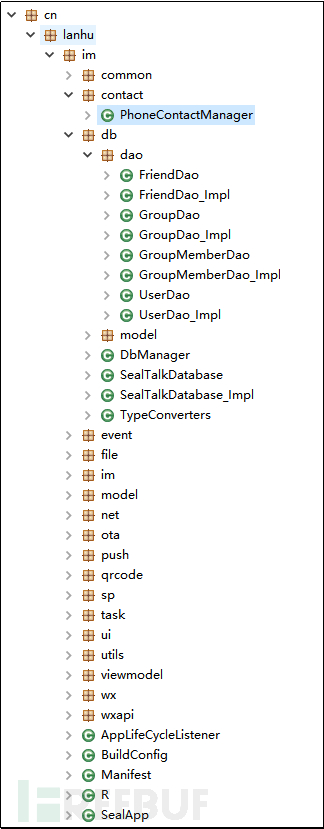 Figure 2-10 Application File Structure
Figure 2-10 Application File Structure
Among which, the following malicious code exists in the APP: getting contact information, taking photos, capturing screen shot information from the user's device, and recording during the process of clicking red envelopes.
(1) The application provides the business function of chatting with friends in the address book, which can add friends by searching for accounts.
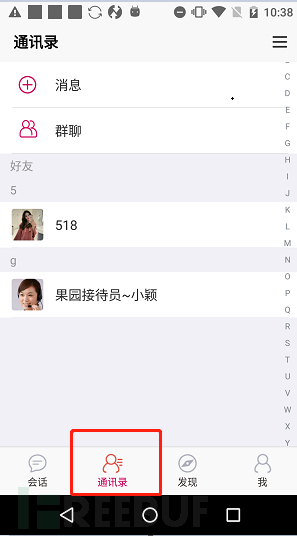 Figure 2-11 Address Book Function
Figure 2-11 Address Book Function
The App has the function of getting contact information, which is currently not actually called. It is speculated that the developer originally intended to provide the business function of adding friends from the contact list. However, since the registration of user accounts does not require the provision of a mobile phone number, this function was not realized.
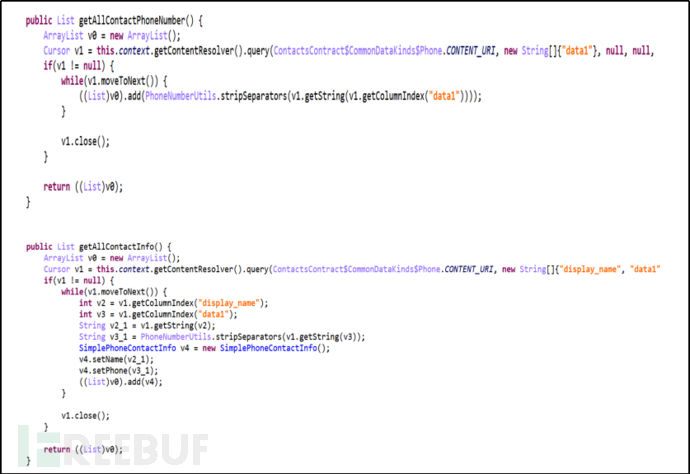 Figure 2-12 Get Contact Information
Figure 2-12 Get Contact Information
(2) Take photos:
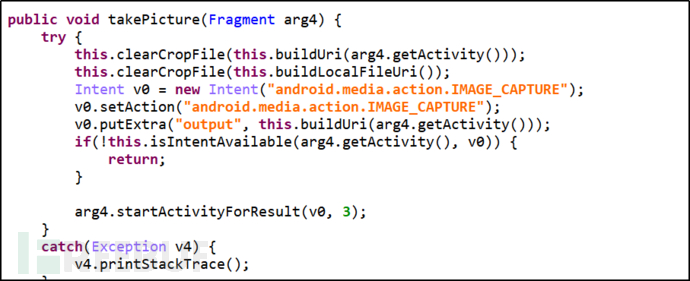 Figure 2-13 Take Photos
Figure 2-13 Take Photos
(3) Capture screen shot information from the user's device:
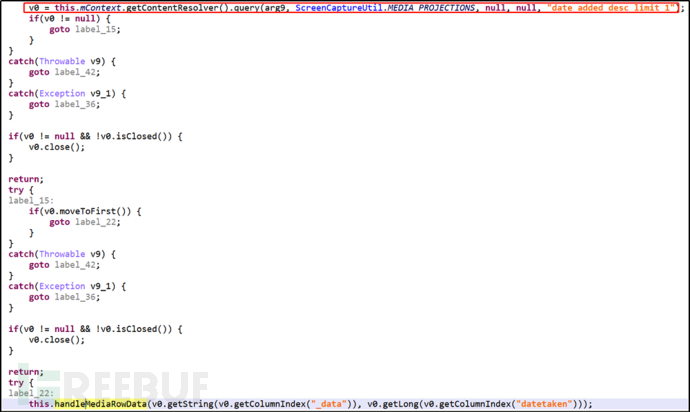 Figure 2-14 Capture Screen Shot
Figure 2-14 Capture Screen Shot
(4) Recording during the process of clicking red envelopes:
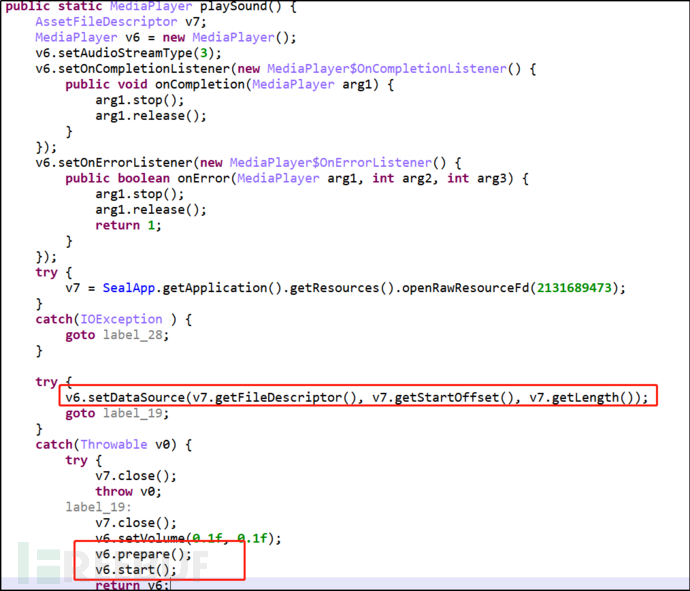 Figure 2-15 Recording
Figure 2-15 Recording
(5) In addition, the application has also integrated **websites, where users recharge, hang up, and complete tasks on the **website page.
 Figure 2-16 **Page
Figure 2-16 **Page
In recent years, **websites and APPs have been popular. On the Heng'an Jiaxin App全景态势与案件情报溯源挖掘平台, we can search out tens of thousands of **APPs just by matching some simple rules. On the surface, the network appears to be a way of online gambling, but in essence, it is a process of fraud using psychological tactics.
 Figure 2-17 Platform Mining **APP
Figure 2-17 Platform Mining **APP
4. Traceability of Intelligence Information
The traceability of intelligence information is shown in the following source brain map:
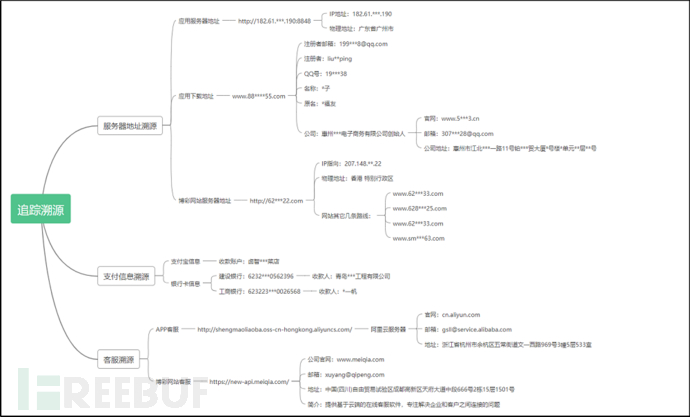 Figure 2-18 Source Brain Map
Figure 2-18 Source Brain Map
4.1 Tracing the Source of the Server Address
(1) Application Server Address:http://182.61.***.190:8848
-
IP address: 182.61.***.190
-
Physical address: Guangdong Province, Guangzhou City
-
The last time the domain pointed was on June 6, 2020
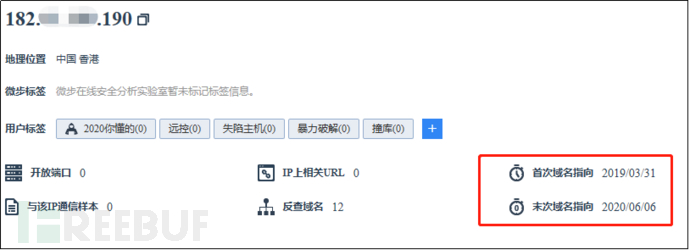 Figure 2-19 Domain Pointing
Figure 2-19 Domain Pointing
The following information was obtained by IP reverse lookup of the domain name:
| Domain Name | |
|---|---|
| www.c***g.cn | www.xm***oin.com |
| www.d***bo.cn | www.cc***ing.net |
| www.88***055.com | www.jl***d.net |
(2) Tracing the Source of the Application Download Address:www.88***055.com
Among which, the server address obtained through IP reverse lookup iswww.88***055.com is the download address of the APP, at this time the APP has changed from 'Farmer Chat' to 'Shengmao Fruit Chat', only the name of the application has been changed, and the code is indeed the same set.
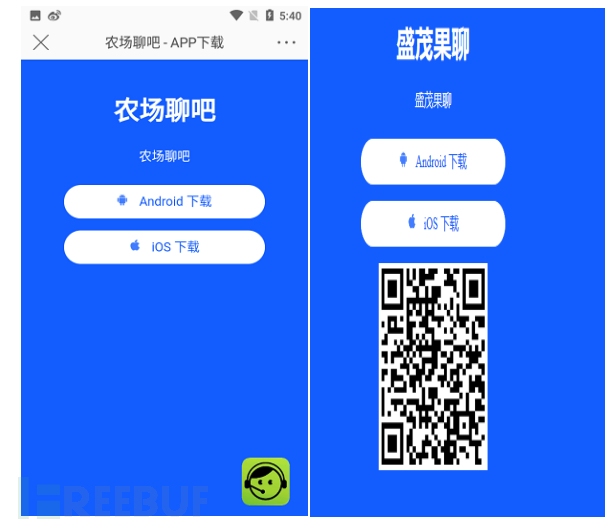 Figure 2-20 APP Download Page
Figure 2-20 APP Download Page
Download address:www.88Domain registration information of ***055.com:
Registrant email: 19***38@qq.com
Registrant: liu***ping
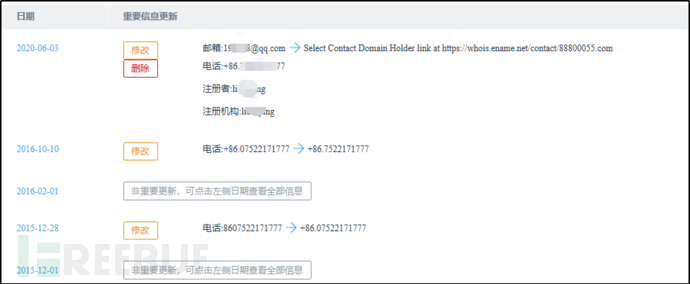 Figure 2-21 Domain Registration Information
Figure 2-21 Domain Registration Information
By searching the registrant's email, we found the QQ information of the registrant:
Nickname: *Fu
QQ number: 19***38
By checking his QQ space, we learned about his ***:
Anonymous: *Zi
Original name: *Fu You
Identity: Founder of Huizhou **** E-commerce Co., Ltd.
The founder, *Zi, is a self-media person, a micro-commerce big shot, engaged in micro-commerce industry training for 2 years, and is also a part-time lecturer of Tsinghua and Peking Universities.
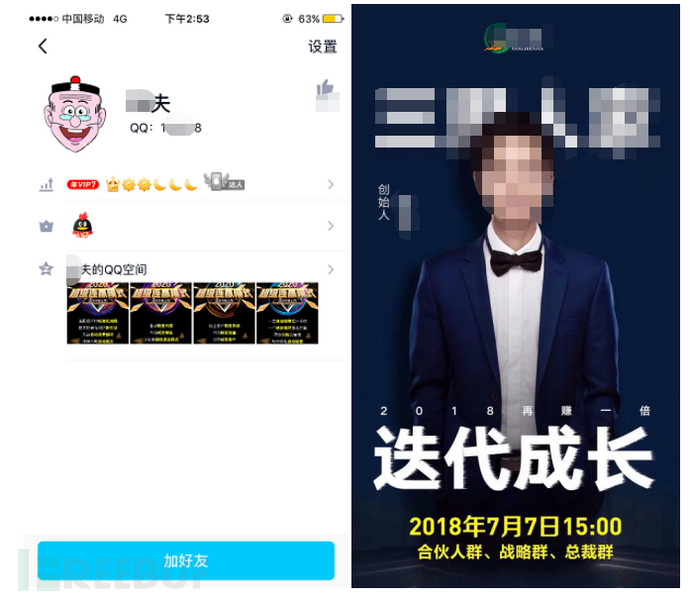 Figure 2-22 QQ Information
Figure 2-22 QQ Information
We have found the corporate information of Huizhou **** E-commerce Co., Ltd.:
Official website:www.5**3.cn
Email:307**328@qq.com
Company address: No. 11, Platinum Mansion, Building * of No. 1 Road, Jiangbei District, Huizhou City
The company was established on April 23, 2015, mainly engaged in e-commerce.
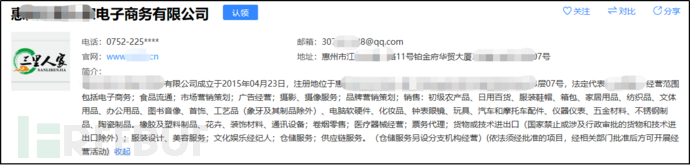 Figure 2-23 Corporate Information
Figure 2-23 Corporate Information
(2) **Website Server Address:http://62***22.com
IP pointing to: 207.148.***.22, Physical address: Hong Kong Special Administrative Region.
Through IP reverse lookup, several other routes of the website were found, but none of these routes are registered.
| Domain Name | IP Address | Location |
|---|---|---|
| www.62***33.com | 207.148.***.22 | Hong Kong |
| www.62***25.com | 207.148.***.22 | Hong Kong |
| www.62***33.com | 207.148.***.22 | Hong Kong |
| www.s***863.com | 207.148.***.22 | Hong Kong |
4.2 Tracing Payment Information
(1) Alipay Information
During the chat with customer service, the following Alipay payment code was obtained:
Payment account: Lu Zhi***Cai Shop.
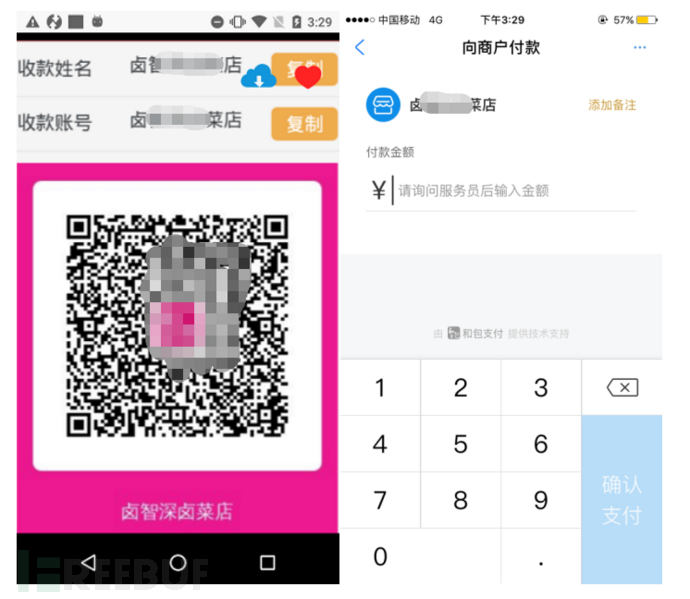 Figure 2-24 Alipay information
Figure 2-24 Alipay information
(II) *** information
The following *** information was obtained: some *** information was blurred.
| *** number | Bank of deposit | Payee |
|---|---|---|
| 6232512390****396 | China Construction Bank | Qingdao Meng**** Engineering Co., Ltd. |
| 6232236520000****568 | Industrial and Commercial Bank of China | *Yifan |
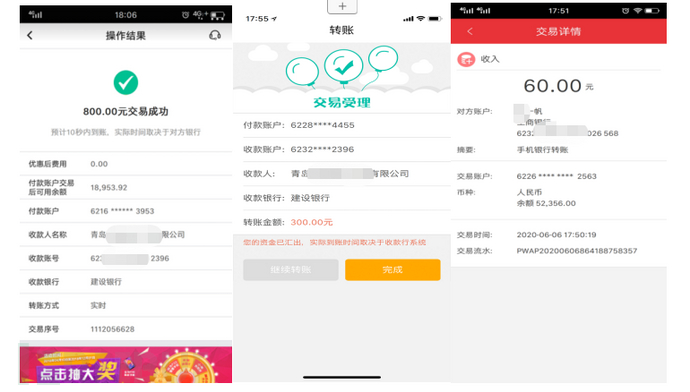
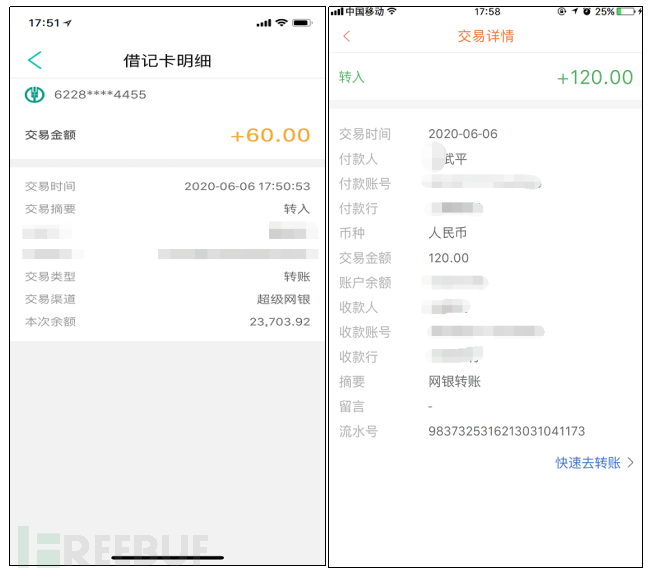 Figure 2-25 *** information
Figure 2-25 *** information
From the recent release of the “The inexpensive 'cradle' of black and gray industries — scoring platformsThe report tells us that the information provided, such as the *** and payment QR code information, may not be their own information, but ordinary user information obtained through scoring platforms.
4.3 Customer traceability
(I) APP customer service
Server address:http://shengmaoliaoba.oss-cn-hongkong.aliyuncs.com/.
The customer service uses cloud servers provided by Alibaba Cloud:
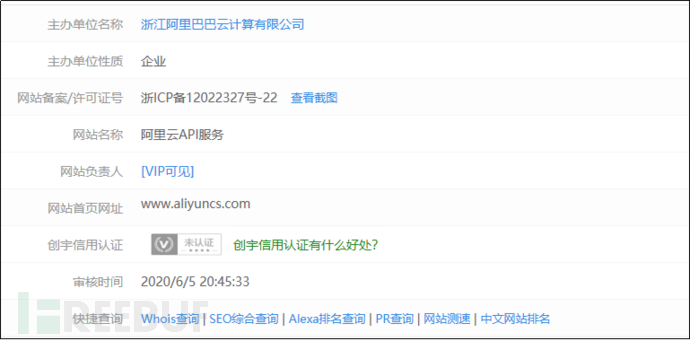 Figure 2-26 Domain name registration information
Figure 2-26 Domain name registration information
(II) **Website customer service
Server address:https://new-api.meiqia.com/.
The website accessed within the application uses cloud customer service provided by Chengdu Meiqia Network Technology Co., Ltd.
 Figure 2-27 Domain name registration information
Figure 2-27 Domain name registration information
5. Summary
At the end of the day, this is a new variant of part-time刷单scam, **inducing recharge scam. The secret to the scammer's repeated success is that they take advantage of people's love for small benefits and their relaxation of vigilance after a little sweetness, engaging with the victim step by step to gain their trust, and finally making a clean sweep. Therefore, everyone should firmly believe that there is really no free lunch in the world, and that manna from heaven will not fall. Not to be greedy for small benefits and to always raise their vigilance is the only way to avoid becoming an easy victim of fraud.
评论已关闭