On October 31st, at the 10th KCon Security Conference, the security researchers Qin Shi, Lu Haoliang, and Wu Fan from the ByteDance Wuhe Lab brought the topic of '<>Your smart hardware has sold your information - A brief discussion on hardware supply chain security in office and educational scenariosThe topic, the speaker expanded on the security of IoT products in the supply chain circulation process during the conference, analyzing a large number of mainstream office and educational products on the market, finding that most leading manufacturers' products have design flaws, leading to the possibility of malicious code being implanted in the products, and then stealing business secrets and monitoring sensitive areas of the home. The speaker, focusing on common smart hardware, explained from multiple perspectives why serious defects still occurred under the preset protection mechanisms of IoT products, and how to improve business security awareness through the establishment of IoT security SDLC processes, to discover and repair such defects in advance, and ensure product security.
The current security status of IoT product supply chain
In the field of supply chain security, software supply chain attacks are easy to attract attention, while attacks on the hardware supply chain in the circulation process, such as the news exposed last year, where over 2,000 Jinli mobile phones were infected with malware, are very easily overlooked.
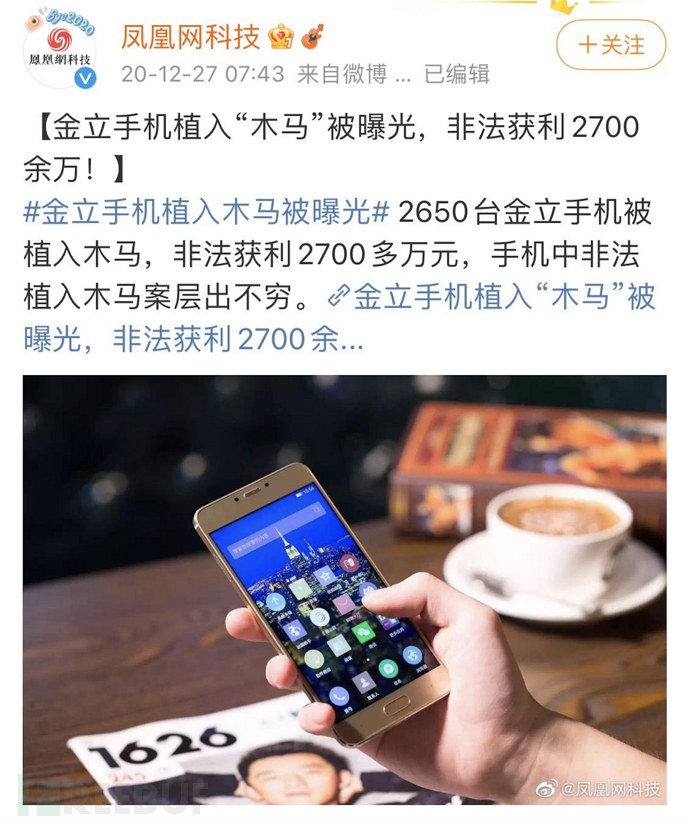
From phenomena to essence, both domestically and internationally, there are standard documents on supply chain security risk management guidelines in relevant specifications, which also mention the security threats of tampering and implanting in the hardware supply chain, as well as the integrity protection of the supply chain.

Looking at the mainstream desktop processors, servers, laptops, and operating system manufacturers in the industry, they have long implemented mechanisms such as secure boot and trusted computing.
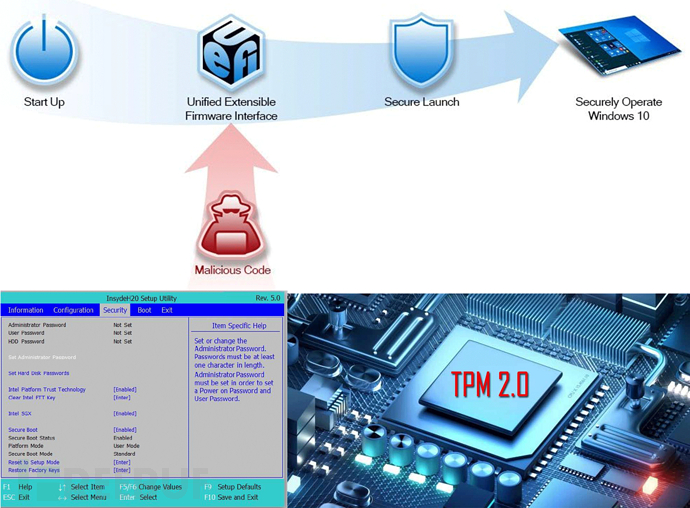
From the perspective of the underlying mobile processor manufacturers, companies such as Qualcomm and MTK, who are commonly used in IoT solutions, all provide complete SecureBoot and TEE implementation support.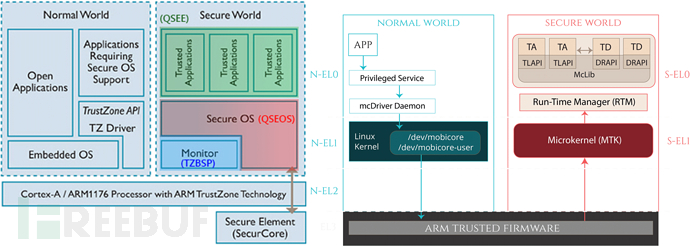
However, the actual situation at the IoT product end is not as optimistic. In the research of No Constant Laboratory, a total of 9 IoT products (with complete security boot support) from 5 leading manufacturers were found to have design defects, leading to the possibility that malicious code can be implanted in the supply chain circulation process.
On the one hand, manufacturers generally believe that such implantation attacks require physical contact and are not as highly regarded as security vulnerabilities, and are not recognized.
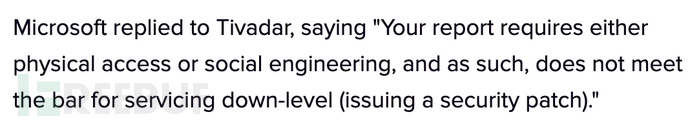
On the other hand, the complex supply chain network leads to a large number of time windows for supply chain implantation in the circulation process before the product reaches the customer. This ultimately causes the defects in the product design stage to be further amplified in the process of circulation.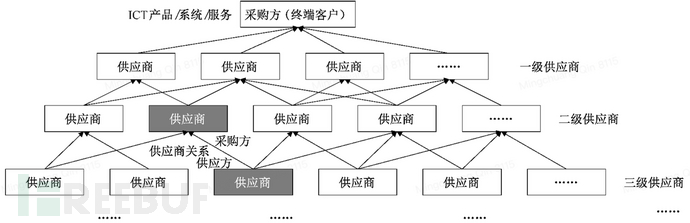
In the corporate office scenario, if smart boxes, smart TVs, conference terminals, and other devices are maliciously planted in the supply chain, it can lead to attackers stealing business secrets and causing irreparable losses to the enterprise.
Educational hardware without security protection, such as smart speakers, smart educational screens, and so on, may be cracked and changed to change the original design and usage of the product. Learning machines can become game machines or media for browsing bad information, and are more likely to be used for monitoring sensitive areas of the home.
2.Common protection mechanisms of smart hardware
Trust chain
The chip solutions of mainstream smart hardware currently provide complete SecureBoot, which provides a reliable protection mechanism. SecureBoot includes a complete set of integrity verification mechanisms, with the core idea being that before the boot code loads the next-level code at the current stage, the integrity of the loaded code is verified based on PKI.
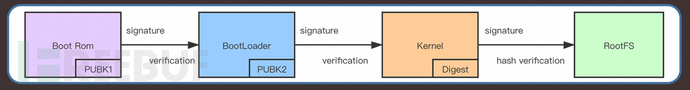
Trust root
All CPUs that support Secure Boot will have a small OTP storage, also known as FUSE or eFUSE, which works on the principle similar to a fuse in reality: information is written before the chip is shipped, and once written, it cannot be changed.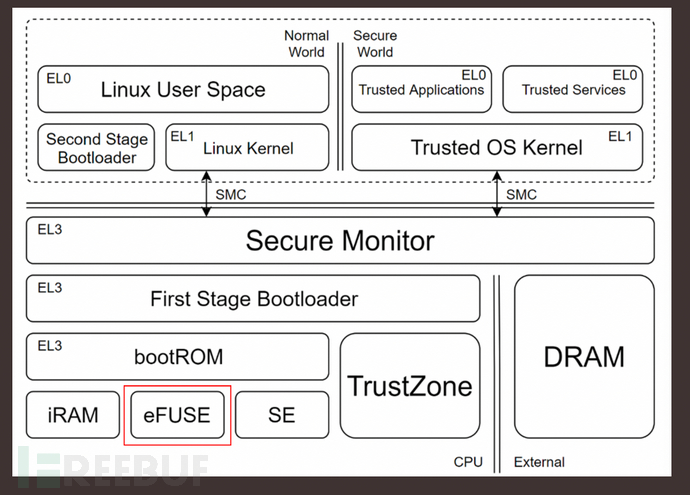
DM-Verity
DM-Verity is a sub-module of Device Mapper in the kernel subsystem, which is used to ensure the integrity of the device partitions. For small partitions, direct or indirect signing with the trust root is used. For larger partitions, such as the system partition, comparison and verification with the preset root hash are performed.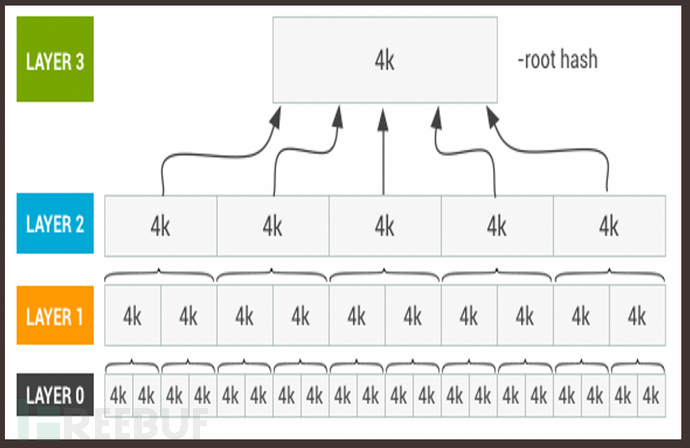
3. Implementation defects and bypassing integrity protection
The entire verification ring from the trust root to Boot Verify and then to DM Verity has the risk of being bypassed due to the implementation defects of manufacturers.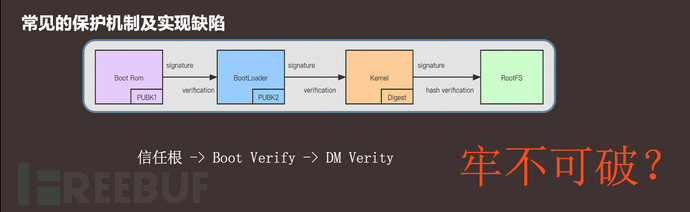
More than 90% of smart hardware on the market do not have secure boot enabled. Although the secure boot is not turned on, the protection mechanism from BootLoader downwards may be enabled, and the firmware needs to be obtained to analyze the protection logic. Mainstream chip solution manufacturers such as Qualcomm and MTK provide official Flash burning tools that can be used to obtain the firmware for analysis.
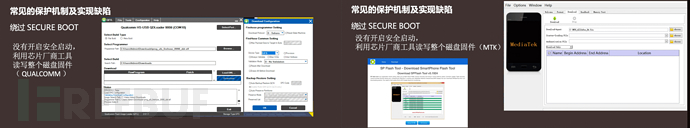
Through firmware analysis, we found that the Boot Verify and DM-Verity parts of multiple devices have implementation flaws that can bypass the integrity verification of the Boot stage and the DM-Verity stage.
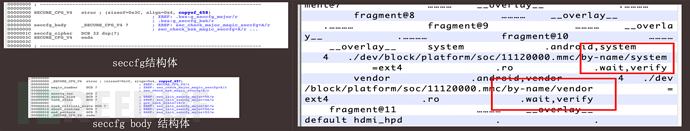
By bypassing multiple stages of integrity verification, arbitrary modifications can be made to the ROM, such as disabling system security options like SELinux and implanting Trojan backdoors.
4. Summary
How to avoid such defects to protect the security of the hardware supply chain? The following figure shows the current situation of some manufacturers. Based on such a situation, manufacturers need to enhance their security awareness and consider security features in the basic cost of products.
Some manufacturers have adopted the following protection schemes, but a perfect protection mechanism also needs to be secure at its root.

With the evolution of the hardware project lifecycle, the cost of defect repair in hardware products at different stages increases geometrically. Some vulnerabilities can no longer be repaired after sale, unless a recall is made. Therefore, it is necessary to intervene early in the design and development process of hardware products. Security design can be considered at the project initiation stage by establishing an IoT product SDLC process, considering secureboot function design, and avoiding supply chain implant attacks on products.
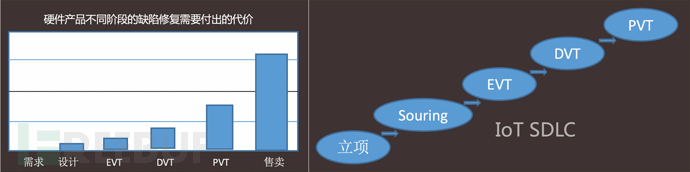
For the IoT SDLC, the Wuheng Lab has designed a complete process with good implementation results. Here is a brief introduction: at the project initiation stage, security requirements are introduced; during the supplier sourcing stage, the security capabilities of suppliers are audited; in the EVT (Engineering Verification Test) engineering verification test stage, the DVT (Design Verification Test) design verification test stage, and the PVT (Production/Process Verification Test) production/process verification test stage, each stage has a round of security testing, and all vulnerabilities must be repaired before the PVT stage. Vendors can customize an IoT SDLC process suitable for their own implementation based on their company's hardware project lifecycle management process.
Five、About Wuheng Lab:
The Wuheng Lab is a professional offensive and defensive research lab composed of senior security researchers from ByteDance. The lab members have strong practical offensive and defensive capabilities. By means of penetration testing, business blue team exercises, vulnerability discovery, black industry打击, emergency response to vulnerabilities, and APT emergency response, the company's basic security, data security, and business security levels are continuously improved, and the impact of security incidents on business and the company is minimized. At the same time, the company and various products provide regular penetration testing services and produce penetration testing reports. We strive to ensure the safety of ByteDance users when using their products and services.
The Wuheng Lab is currently recruiting, welcome to submit your resume.

评论已关闭