1. Affected versions
Recently, DeepinServeQianlimu Security Technology Centerinoperational worka new type ofransomwareESXiArgsThis ransomware began to appear on a large scale this February. As of the early morning of February 8, based on censys statistics,The global affected servers have2453 Taiwan, and about ten affected servers in China. Many national cybersecurity organizations have issued warnings about this.
VMwareOfficial vulnerability explanation and repair method reference:
http://www.vmware.com/security/advisories/VMSA-2021-0002.html
The affected versions: ESXi70U1c-17325551, ESXi670-202102401-SG, ESXi650-202102101-SG and earlier versions,Subsequent versions are not affected.
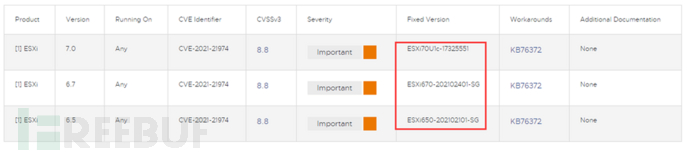
This time, ESxi 6.7 is the implementation object, 6.5 and 7.0 are the same
II. Solution (upgrade version)
ESXi7.0 version:Upgrade to ESXi70U1c-17325551 version and above
ESXi6.7 version:Upgrade to ESXi670-202102401-SG version and above
ESXi6.5 version:Upgrade to ESXi650-202102101-SG version and above
III. Query the current version (Vcenter view)
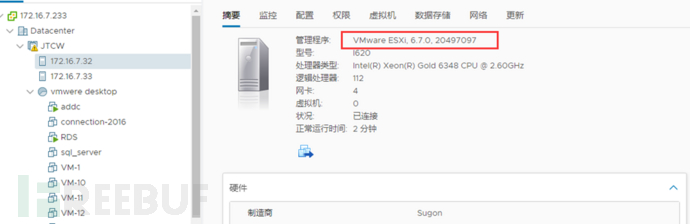
1. Log in to Vcenter to check, view the host summary
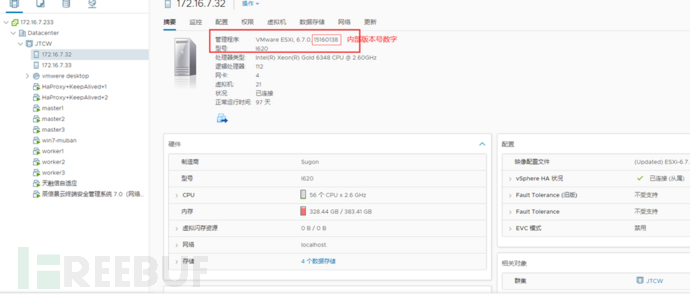
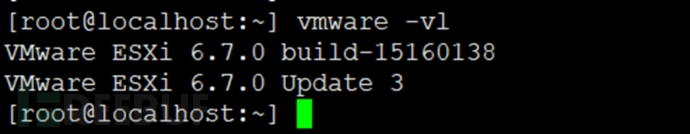
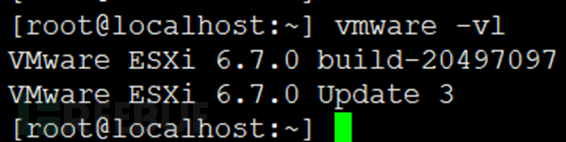
2. SSH remotely log in to the Esxi host to view
[root@localhost:~] vmware -vl
IV. Download patch package (any VMware account is enough)
ESXi7.0 version:Upgrade to ESXi70U1c-17325551 with a higher internal version number than 17325551, any one of them
ESXi6.7 version:Upgrade to ESXi670-202102401-SG with a higher internal version number than 202102401, any one of them
ESXi6.5 version:Upgrade to ESXi650-202102101-SG with a higher internal version number than 202102101, any one of them
Download address: Any account is sufficient
https://customerconnect.vmware.com/cn/patch
V. Install patches
5.1 Note
1,Note: For Esxi clusters containing VSAN clusters, you can choose to ensure accessibility (other replicas running) when entering maintenance mode; The Esxi cluster without VSAN cluster needs to migrate the virtual machines aboveOr enter maintenance mode to trigger automatic migration (Change the host to change the shared storage ), The Vcenter needs to be upgraded last, and the host needs to be restarted during the upgrade process;
5.2 Query the internal version number
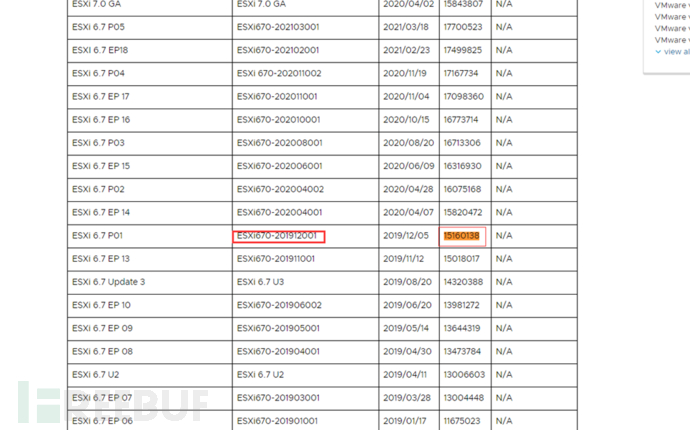
2. Take VMware ESXi 6.7.0 build-15160138 as an example, with an internal version number of 15160138
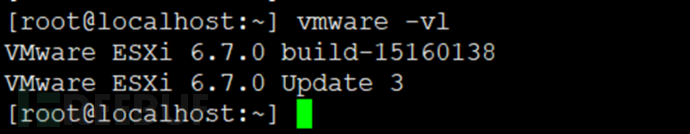
5.3 Query the internal version number corresponding to the Esxi major version (compare with the affected version)
The affected versions: ESXi70U1c-17325551, ESXi670-202102401-SG, ESXi650-202102101-SG and earlier versions,
Query the Esxi version corresponding to the internal version number, here you need to check, according to the internal version number, query the corresponding Esxi version, compare it after querying with the affected version that needs to be patched
Query URL:
https://kb.vmware.com/s/article/2143832?lang=zh_cn
Query the version correspondence: Internal version number 15160138, corresponding Esxi version is ESXI670-201912001 less thanESXi670-202102401-SGIt belongs to the affected version and a patch needs to be downloaded to fix it
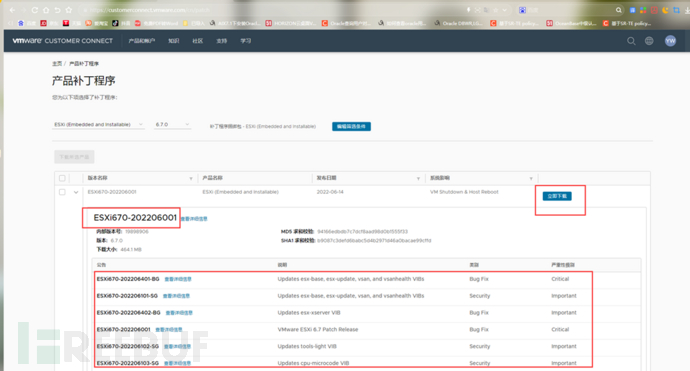
5.4 Download patches
https://customerconnect.vmware.com/cn/patch
3. Use the Vmware registered account to log in to the patch download address, and then select the corresponding version for download according to the version
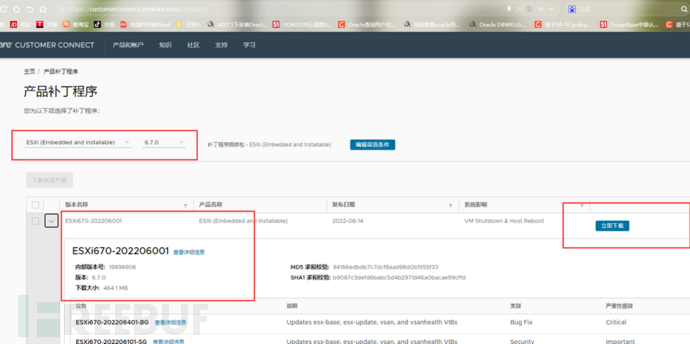
5.5 Upload and install patches
5.6 Enable SSH and Esxi Shell on the Esxi host
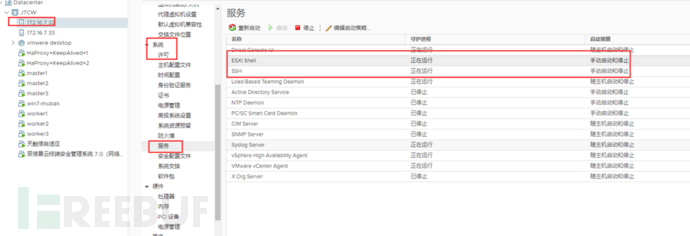
5.7 Upload patches
Two methods:
1. Log in to the Esxi host individually, then upload through the browser (recommended, fast,)Place it in local storage,Local hard disk)
2. Upload through SSH or SFTP (used this time)
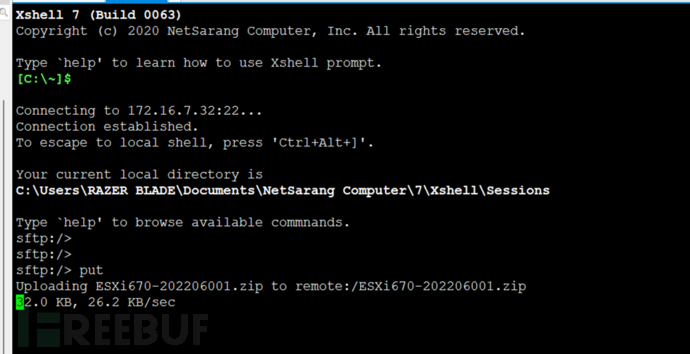
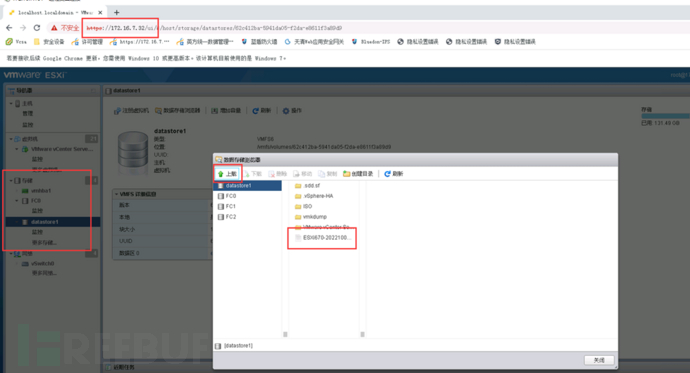
5.8 Install patches
[root@localhost:~] cd /vmfs/volumes/datastore1/
[root@localhost:/vmfs/volumes/62c412ba-5941da05-f2da-e8611f3a89d9] ls ESXi670-202210001.zip ISO VMware vCenter Server Appliance vmkdump
When the Esxi host enters maintenance mode, or before or during the process, the running virtual machines will be changed to a different running location
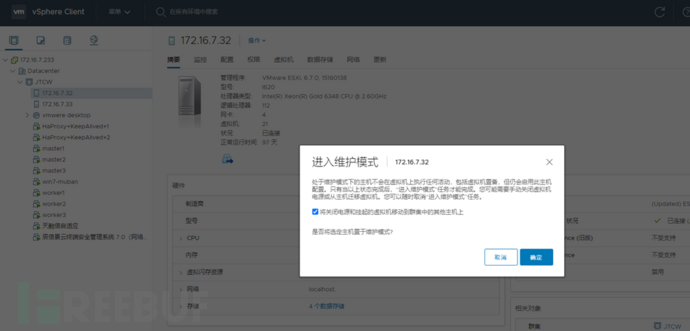
[root@localhost:/vmfs/volumes/62c412ba-5941da05-f2da-e8611f3a89d9]esxcli software vib update -d /vmfs/volumes/datastore1/ESXi670-202210001.zip
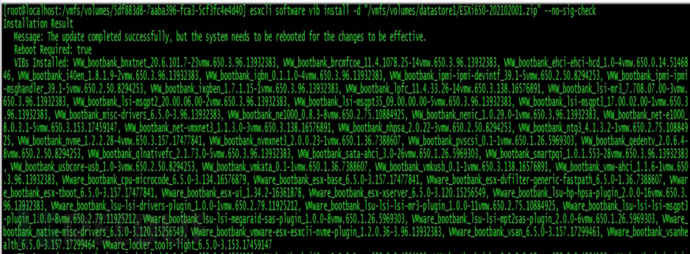
After installation, input Reboot to restart and check if the ESXi version has been updated
The ESXi host exits maintenance mode, followed by the upgrade of other Esxi versions in order
评论已关闭