2025年第一季度,网络安全战场硝烟四起,网络犯罪分子继续发起新的攻击并优化其攻击手段。本文对五大值得关注的恶意软件进行了概述和简要分析。

2025年初,攻击者开始利用一种被称为ClickFix的技术来传播 NetSupport 远程访问木马(RAT)。这种技术会将虚假的验证码页面注入被攻陷的网站,诱导用户执行恶意 PowerShell 命令,从而下载并运行 NetSupport RAT。一旦安装成功,该 RAT 会赋予攻击者对受害者系统的完全控制权,包括实时屏幕监控、文件操作以及任意命令执行。
NetSupport RAT 的主要技术特点
- 攻击者可以实时查看并控制受害者屏幕。
- 上传、下载、修改和删除受感染系统中的文件。
- 远程运行系统命令和 PowerShell 脚本。
- 捕获复制的文本,包括密码和敏感数据。
- 记录用户按键以窃取凭证。
- 启动、停止和修改系统进程和服务。
- 通过启动文件夹、注册表键或计划任务实现持久化。
- 使用进程注入和代码混淆技术逃避检测。
- 通过加密流量与攻击者保持隐秘通信。
当 NetSupport RAT 感染系统时,它会立即与命令和控制 (C2) 服务器建立连接,从而允许攻击者远程作受感染的机器。通过此连接,攻击者可以执行系统命令、部署其他恶意软件和修改系统设置。
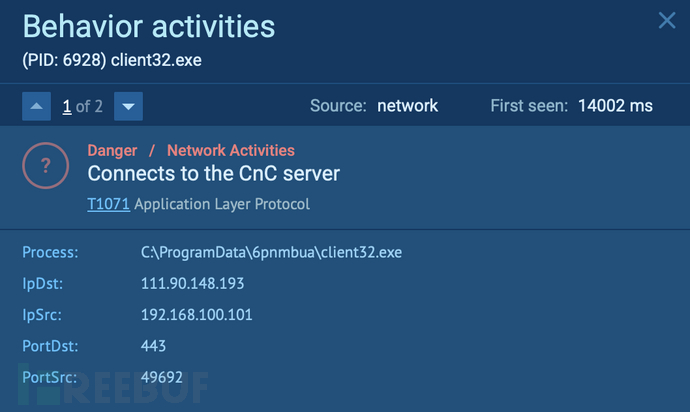
检测到的 CnC 连接
NetSupport RAT 还使用多种战术、技术和程序(TTP)来维持持久性、逃避检测并收集系统数据。关键的 TTP 包括:
- 持久性与执行:修改注册表启动项,通过 wscript.exe 执行脚本。
- 发现:读取计算机名称、检查系统语言并访问环境变量。
- 防御规避与 C2 通信:投放合法的 Windows 可执行文件,创建远程控制的互联网连接对象。
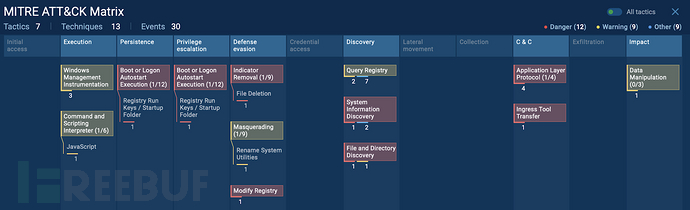
NetSupport RAT 使用的主要TTP
Lynx 勒索软件:瞄准多行业的加密攻击
Lynx ransomware as a service (RaaS) organization is known for its highly structured nature, providing a comprehensive affiliate program and strong encryption methods. Based on the foundation of early INC ransomware, Lynx has enhanced its capabilities and expanded its attack range, targeting different industries in multiple countries.
Lynx ransomware as a service (RaaS) organization is known for its highly structured nature, providing a comprehensive affiliate program and strong encryption methods. Based on the foundation of early INC ransomware, Lynx has enhanced its capabilities and expanded its attack range, targeting different industries in multiple countries.
To encourage participation, Lynx provides its affiliate companies with an 80% share of the ransomware profit. The organization maintains a leak site where stolen data is published if the victim fails to pay the ransom.
Main attack events of Lynx
In the first quarter of 2025, Lynx encrypted the system of a leading Australian truck dealer and a US law firm specializing in corporate and securities law, stealing a large amount of sensitive data and threatening the victims to pay a ransom.
Main technical characteristics of Lynx ransomware
- Encrypt all files by default, including local drives, network shares, and removable media
- Configurable through RaaS to target specific file types, folders, or extensions
- Steal sensitive data before encryption, including documents, credentials, and financial information
- Transmit stolen data through HTTPS or custom encrypted channels
- Delete shadow copies and disable Windows restore function to prevent restoration
- Close applications that may prevent encryption
- Extract stored passwords using credential dump technology
- Communicate anonymously through the Tor network and maintain a connection with the C2 server
- Detect virtual machine and sandbox environments, and change behavior to evade analysis
- Running in memory to avoid writing files to the disk
The behavior of Lynx Ransomware can be directly observed in the following controlled environment. After successful infection, the desktop background is replaced with a ransom message, and the attacker leaves a note warning that all data has been stolen and encrypted. The victim is instructed to download Tor to contact them.
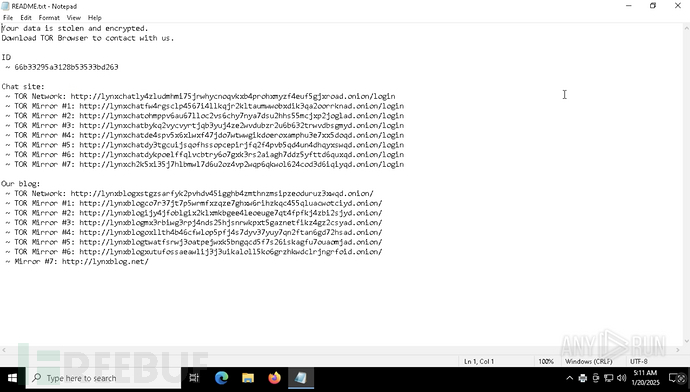 Ransomware message left by the attacker
Ransomware message left by the attacker
Some files have also been renamed and their extensions appended. For example, C:\Users\admin\Desktop\academicroad.rtf becomes C:\Users\admin\Desktop\academicroad.rtf.LYNX.
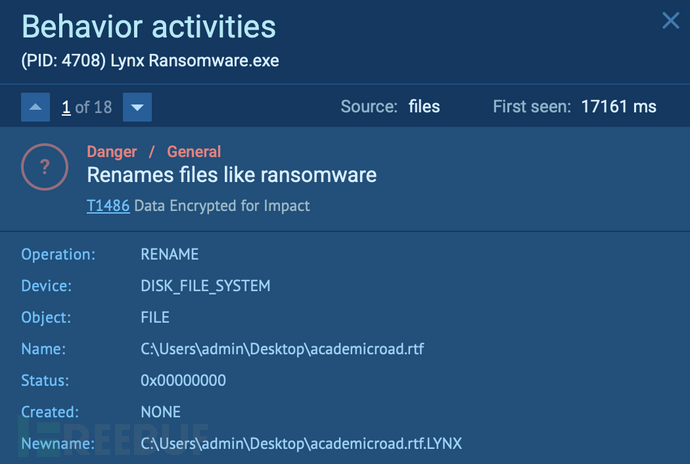 Files renamed using .lynx detected
Files renamed using .lynx detected
Dozens of files in the entire system have been modified in this way, further confirming their encryption process. These are only a small part of the many destructive actions that Lynx performs on the infected system.
AsyncRAT: Using Python to load and TryCloudflare tunnel
In early 2025, cybersecurity researchers discovered a complex malware operation that deployed AsyncRAT, a remote access trojan known for its efficient asynchronous communication capabilities.
This operation stands out for its use of Python-based payloads and the exploitation of TryCloudflare tunnels to enhance stealthiness and persistence.
The attack begins with a phishing email containing a Dropbox URL. When the recipient clicks on the link, they download a ZIP archive containing an Internet shortcut (URL) file. In turn, this file retrieves a Windows shortcut (LNK) file through TryCloudflare URL. Executing the LNK file triggers a series of scripts, PowerShell, JavaScript, and batch scripts that download and execute Python payloads.
This payload is responsible for deploying multiple malware series, including AsyncRAT, Venom RAT, and XWorm.
Technical Features of AsyncRAT
- Enables attackers to execute commands, monitor user activities, and manage files on the infected system.
- Capable of stealing sensitive information, including credentials and personal data.
- Employing techniques to maintain long-term access, such as modifying system registries and exploiting startup folders.
- Using obfuscation and encryption to evade detection by security solutions.
AsyncRAT connects to masterpoldo02[.]kozow[.]COM through port 7575, allowing remote attackers to control the infected machine. Blocking this domain and monitoring traffic to this port helps prevent infections.
Additionally, AsyncRAT installs itself in %AppData% to blend in with legitimate applications and uses a mutex (AsyncMutex_alosh) to prevent multiple instances from running.
 Analysis of malicious configurations in a controlled environment
Analysis of malicious configurations in a controlled environment
The malware also uses AES encryption with hardcoded keys and salts, making it difficult for security tools to analyze its communication.
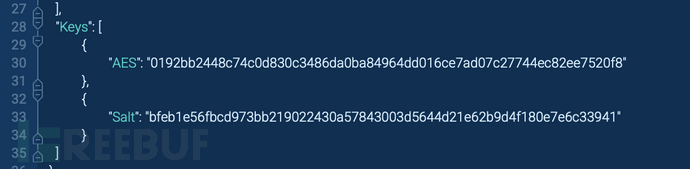 AES encryption used by AsyncRAT
AES encryption used by AsyncRAT
Lumma Stealer: Based on GitHub Distribution
In early 2025, cybersecurity experts discovered a complex operation involving the information-stealing malware Lumma Stealer.
The attacker uses GitHub's release infrastructure to distribute this malicious software, taking advantage of the platform's credibility to bypass security measures. After execution, Lumma Stealer will initiate other malicious activities, including downloading and running other threats such as SectopRAT, Vidar, Cobeacon, and other variants of Lumma Stealer.
Technical Features of Lumma Stealer
- Distributed via GitHub versions, taking advantage of trusted infrastructure to evade security detection.
- It steals browser credentials, cookies, cryptocurrency wallets, and system information.
- The stolen data is sent to a remote server to achieve real-time leakage.
- Can download and execute other malware, including SectopRAT, Vidar, and Cobeacon.
- Maintains access privileges through registry modifications and startup items.
- It can be detected by network-based security monitoring tools, revealing malicious communication patterns.
When executed, the malware connects to its command and control server, thus leaking sensitive data. The analysis also revealed the triggering of specific Suricata rules.
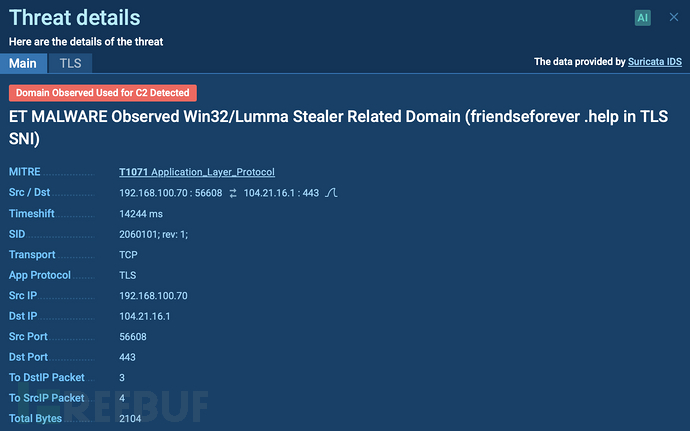 Suricata rules triggered by Lumma Stealer
Suricata rules triggered by Lumma Stealer
The analysis also revealed how Lumma steals credentials from web browsers and leaks personal data.
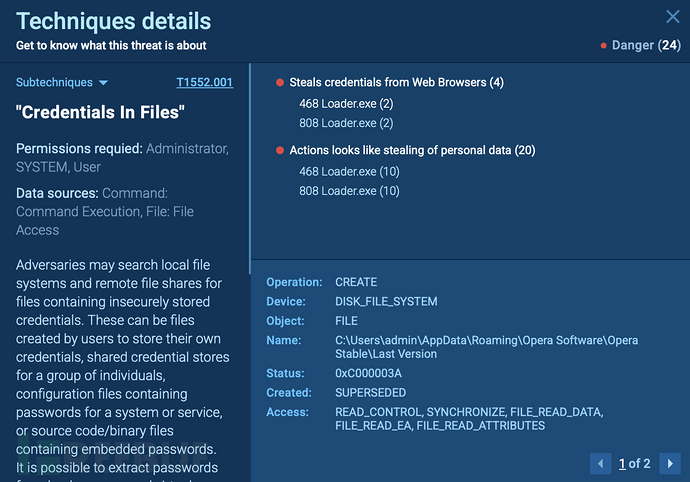 Lumma Stealer Steals Credentials and Personal Data
Lumma Stealer Steals Credentials and Personal Data
InvisibleFerret: A Silent Threat Hiding in Fake Job Opportunities
In a wave of social engineering attacks, cybercriminals have been using InvisibleFerret (a stealthy malware based on Python) to undermine unsuspecting victims.
This malware disguises itself as legitimate software during the fake job interview process and has been actively used in fake interview campaigns, with attackers posing as recruiters to deceive professionals into downloading malicious tools.
Technical Features of InvisibleFerret
- The malware uses chaotic and obfuscated Python scripts, making analysis and detection challenging.
- InvisibleFerret actively searches for and leaks sensitive information, including source code, cryptocurrency wallets, and personal files.
- It is usually provided as an auxiliary payload by another malware named BeaverTail.BeaverTailIt is an obfuscated information stealing program and loader based on JavaScript.
- The malware establishes persistence on the infected system to ensure continuous access and control.
A key element of the InvisibleFerret attack is the deployment of BeaverTail, a malicious NPM module that provides a portable Python environment (p.zip) to execute malware.
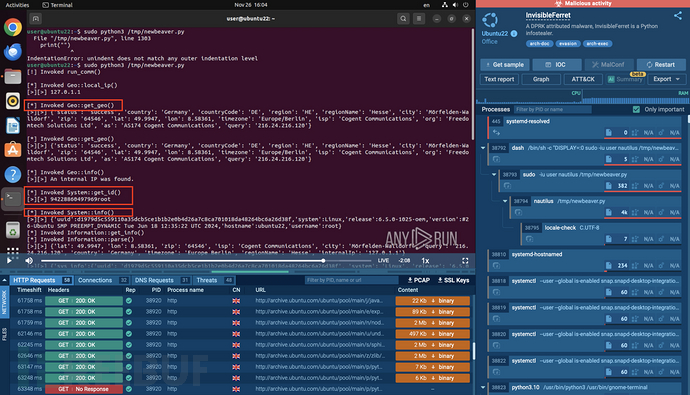 Analyze the leaked information of InvisibleFerret
Analyze the leaked information of InvisibleFerret
As the first stage of a multi-layer attack chain, BeaverTail sets up InvisibleFerret, a stealthy backdoor with advanced obfuscation and persistence mechanisms, making detection difficult.
Reference Source:
评论已关闭