Let's discuss the security of Bluetooth. Internationally, there are two guiding standards for Bluetooth security, NIST 800-121-R1 and IEEE 802.15.1. NIST 800-121-R1 provides a detailed introduction to a complete Bluetooth security workflow, including authentication and authorization of the sender's identity, confidentiality of information during transmission, and access authorization levels to the information, etc. IEEE 802.15.1 focuses more on the research of Bluetooth security standards. In this chapter, the author refers to these two international standard protocols to introduce the operation process and security principles of Bluetooth.
0x1 Bluetooth Security Mode
Bluetooth devices have a total of four standardized access security modes. Security Mode 1 (Insecure); Security Mode 2 (Security Enforcement at Service Level); Security Mode 3 (Link-Level Enforcement Security); Security Mode 4 (Security Enforcement at Service Level, with Key Pairing Strategy). Different security modes determine the available service security level.

Devices operating under security mode 1 are considered insecure. In this mode, the security features (authentication and encryption) are never started, making the device and connection vulnerable to attacks. In fact, Bluetooth devices in this mode are indiscriminate towards enemies and do not employ any mechanism to prevent other Bluetooth devices from establishing connections. If a remote device initiates pairing, authentication, or encryption requests, the security mode 1 device will accept the request without any authentication.
Security mode 2 is a service-level mandatory security mode, where the security process can be initiated after the link is established but before the logical channel is established. In this mode, the local security manager controls access to specific services. Access control and interfaces with other protocols and device users are maintained by a separate centralized security manager. This strategy can define different security policies and trust levels for applications running in parallel with different security requirements to limit access, and can grant access to certain services without providing access to other services.
Security mode 3 provides the best security. It is a link-level mandatory security mode, where Bluetooth devices initiate the security process before the link is completely established. Bluetooth devices operating under security mode 3 authorize and authenticate all connections for the device. Therefore, even service discovery cannot be performed before authentication, encryption, and authorization. Once the device has been authenticated, service-level authorization is usually not executed by security mode 3 devices. When an authenticated remote device uses Bluetooth services without knowing the owner of the local device, service-level authorization should be executed to prevent abuse of authentication.
Security mode 4 uses the secure simple pairing strategy (Secure Simple Pairing, SSP), where the elliptic curve (Elliptic Curve Diffie-Hellman, ECDH) key agreement protocol replaces the outdated key agreement protocol during the generation of link keys.
0x2 Bluetooth trust mode
In addition to the above security modes, the trust methods of Bluetooth devices are divided into two levels: trusted and untrusted. The description is as follows:
1. Trusted: The device has established a fixed relationship with another device, and access to all services is unrestricted.
2. Untrusted: Although the device has passed authentication successfully, it can only access a set of restricted services.
0x3 Device discoverability
The discoverable mode of Bluetooth devices also affects the device's security. Devices in discoverable mode are more susceptible to attacks. Device names, categories, service lists, and technical information can be obtained within a range of about 10 meters. In addition, each Bluetooth device has a 48-bit unique identification code called BD_ADDR. This address is similar to the MAC address, and the BD_ADDR is the address allocated by the manufacturer for the hardware, used as a unique device identifier.
0x4 Bluetooth Security Services
When two devices attempt to connect for the first time, authentication is required to establish a trusted relationship. Based on the BD_ADDR address and a link key, authentication is performed in a challenge/response manner. Once the link is established, it will be saved for future pairing. In older Bluetooth versions (v2.0 and earlier), the first Bluetooth connection used a common PIN code. The PIN code is shared by both devices and consists of 4 to 16 characters. The PIN code is specifically used for link key generation (Figure 1). In some cases, once the PIN code is set, it cannot be changed. It is also important that if two devices have the same PIN code, they cannot communicate or pair. The newer versions of Bluetooth (v2.1 and above) use SSP for pairing, which uses public key cryptography instead of PIN. The protocol is shown in Figure 2.
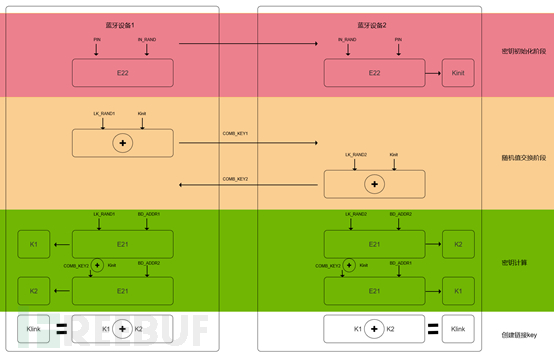
Figure 1: Process of Generating Link Key from PIN Code
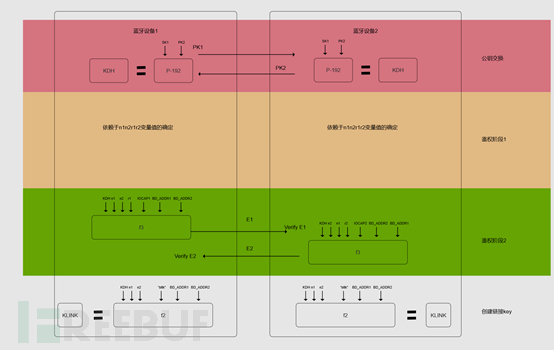
Figure 2: Link Key Establishment of SSP
Firstly, determine whether the device has been authorized as a trusted device before. If the device database lists it as a trusted device, then grant access permissions to the local service. If the device is not listed as a trusted device, it must be re-authenticated before it can be authorized.
The encryption of Bluetooth mainly uses the E0 encryption algorithm. The link key and the device's BD_ADDR are used to generate the key stream, which is combined with plaintext to achieve data encryption. Nowadays, through the attack attempts on the E0 algorithm, it has been proven that the stream encryption protection scheme is easily attacked. We will explain this in the next episode.
0x5 Other security features
Bluetooth technology has some built-in security protection features. They include:
1. Adaptive frequency hopping: Bluetooth uses FHSS (Frequency Hopping Spread Spectrum) to ensure robustness against interference. It hops 1600 times per second across all 79.1 channels in the 2.4GHz band. If any interference is detected on a frequency, then immediately switch to another frequency to send information after one six-hundredth of a second.
2. E0 encryption algorithm: The key length of the password is generally 128 bits, using stream encryption.
3. Invisibility: This will prevent the device from responding to scanning attempts. The 48-bit BD_ADDR address of the device will also be hidden.
4. Pairing: Communication can only be established after the devices are paired.
In the next episode, we will share in detail the main intrusion methods and principles of Bluetooth. We will discuss popular Bluetooth attack methods, threat classification, and threat vectors. Stay tuned.
Author: Li Quan, please forward with attribution.
评论已关闭