
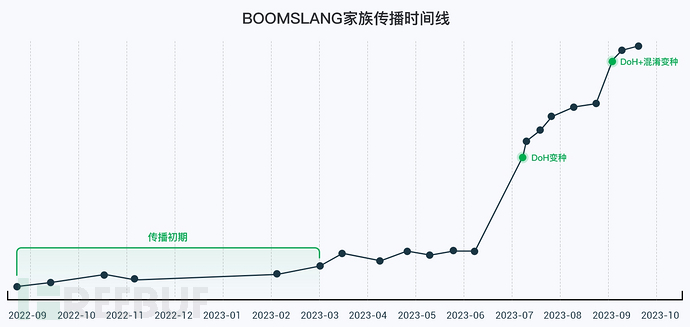
从我们获取的家族样本中进行溯源分析后,发现该家族最早始于 2022 年 9 月进行传播。由于当时疫情等外部因素的影响,该家族在 2022 年 9 月至 2023 年 3 月期间处于欺诈传播的初级阶段。然而,随着社会状况逐渐恢复,该家族开始大规模传播,并推出了多个不同业务类型的版本。值得注意的是,为了适应反欺诈措施,该家族在 2023 年 7 月首次进行了变种,引入了“Domain Over HTTPS(DoH)”技术。随后,在 2023 年 9 月,家族样本再次发生变种,增加了对现有自动化 App 安全检测手段的抵抗能力,具体采用了 NPManager 自带的 StringFrog 混淆技术,以规避基于字符串提取的安全检测。
DoH(DNS over HTTPS)是一种安全协议,用于通过 HTTPS 加密的连接进行 DNS 解析请求和响应。其主要目的是增加隐私和安全性,防止 DNS 请求被窃听或篡改。
Next, we will conduct an in-depth analysis of the original version of the family as well as the version introduced with DoH technology.
Sample overview
Sample identification
- MD5 Hash:
0a731ace7a01349d8c103ad5dc7fc230
Function and behavior
- Login interface: After the sample is started, a login interface is displayed, which requires inputting an invitation code for login.
- Chat interface: After logging in successfully, the user will enter a chat interface.
- Malicious activity: This sample mainly uses chat functions for fraud or other types of malicious behavior.
Analysis details
Sample basic analysis
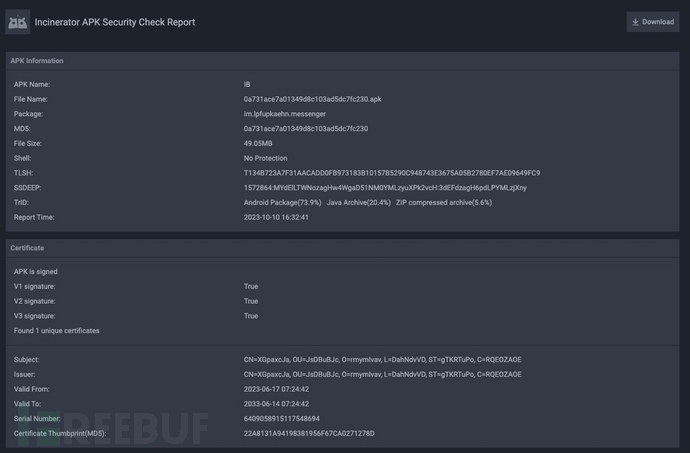
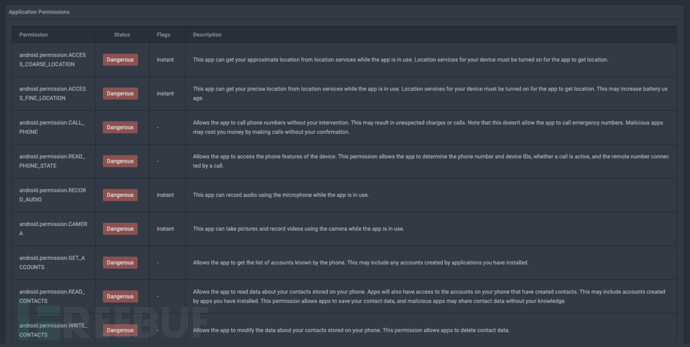
- Permission analysis: After opening the sample with the Incinerator tool, multiple high-risk permissions requested by the sample can be observed from the generated Report information.
- Dynamic detection results:
- Package name and subdirectory issues: Dynamic detection results show that in
im.lpfupkaehn.messengerPackage name undertgnetIn the subdirectory ofNetworkConfig.javaThere are obvious problems in the file.
- Package name and subdirectory issues: Dynamic detection results show that in
Next, we will analyze in detail im.lpfupkaehn.messengerThe specific performance and potential risks of package names.
Code similarity
File and directory structure
- tgnet subdirectory: In
im.lpfupkaehn.messengerThere is a clear corresponding directory undertgnetSubdirectory.
Source code comparison
- GitHub search results: After using the code in this directory for GitHub search, it was found that this part of the code is highly similar to the Telegram Android source code.
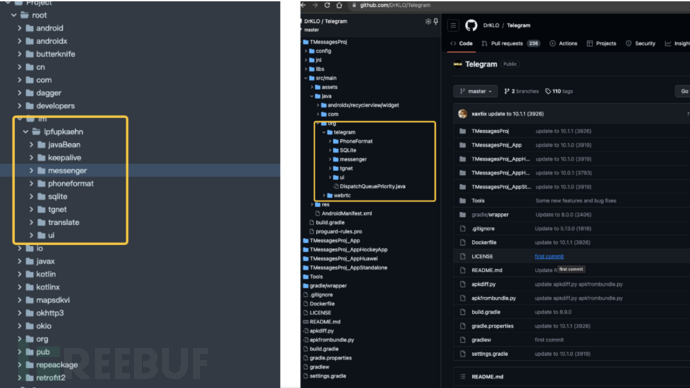
Code similarity comparison
im.lpfupkaehn.messengerWithorg.telegram.messenger
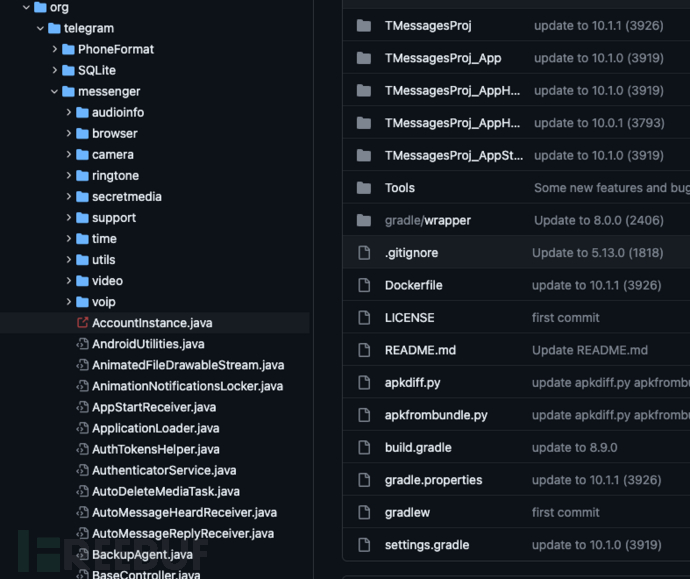
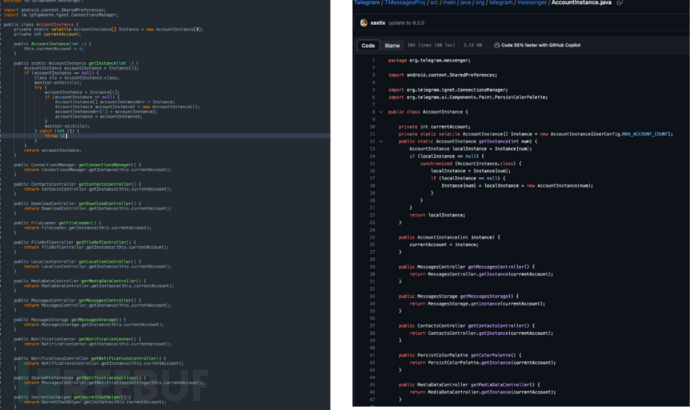
Multiple class files, such as AccountInstanceetc., after excluding the decompilation factors, it is displayed as 100% identical.
Code difference analysis
Main new part
In this sample, based on the Telegram Android source code, there are mainly three significant new additions:
Dependency libraries:
- Location: Mainly concentrated in
comin the directory. - Function and call: These libraries can basically be found by searching for their call locations and are mainly used to handle some smaller functions.
- Example:
com.alibaba.fastjsonThe library is mainly used to handle the protocol for updating user information.
- Location: Mainly concentrated in
UI directory differences:
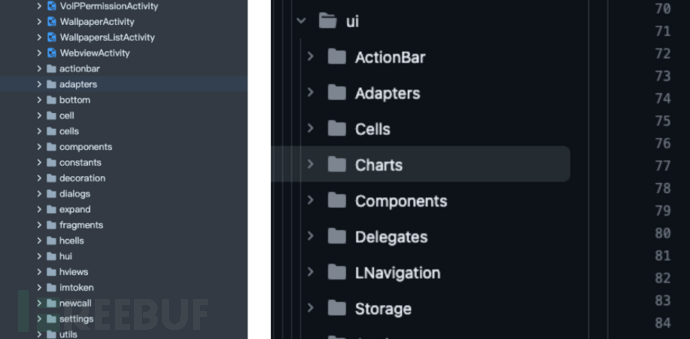
- Comparison:
im.lpfupkaehn.uiDirectory withorg.telegram.uiCompared to the directory, the former has several more directories. - Speculation: These newly added directories may be added to meet the needs of custom UI.
- Comparison:
tgnet directory differences:
- Comparison: In
im.lpfupkaehn.tgnetandorg.telegram.tgnet目录之间进行比较,发现前者多出几个文件。 - Comparing directories, it was found that the former had several more files.
- Comparison: In
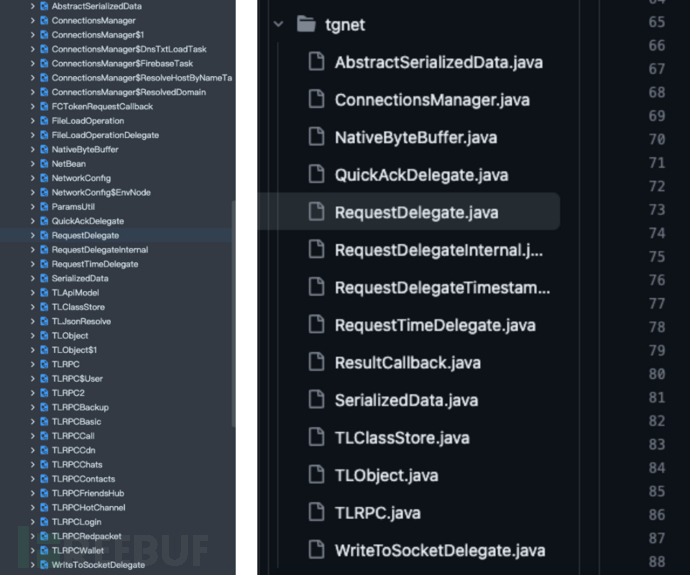
Speculation: These newly added files may be used to implement specific network communication or functions.
Detailed Analysis of Newly Added Class Files
In this family sample, it is particularly noteworthy that the following class files have been added:
Basic network and file operation classes:FCTokenRequestCallback: May be related to Token request.FileLoadOperation: File loading operation.FileLoadOperationDelegate: Proxy for file loading operations.NetBean: Network Configuration Bean.NetworkConfig: Network Configuration.ParamsUtil
: Parameter Tools.
: Telegram Backend Communication Expansion (TL Series):TLApiModel: API Model.TLRPCZ: May be related to RPC communication.TLRPCBackup: Backup Related.TLRPCBasic: Basic RPC Function.TLRPCCall: Call Function.TLRPCCdn: CDN Related.: Chat Related.TLRPCContacts: Contact Related.TLRPCFriendsHub: Friends Center.TLRPCHotChannel: Hot Channels.TLRPCLogin: Login Related.TLRPCRedpacket: Red Packet Function.TLRPCWallet: Wallet Function.
These newly added class files mainly involve many aspects such as network operations, file processing, and communication with the Telegram backend. This further highlights the customization and expansion of this family sample compared to the original Telegram code.
Network Behavior Analysis Report
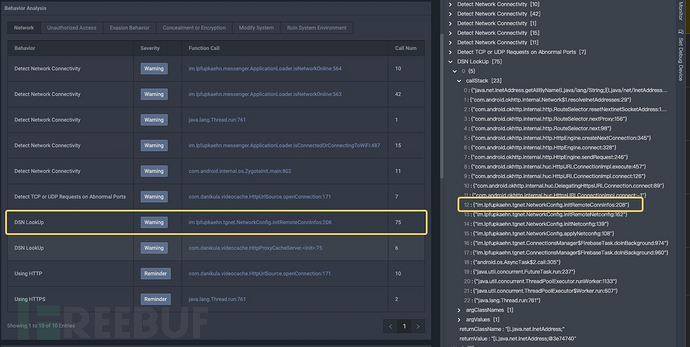
Main Focus:NetworkConfig.java
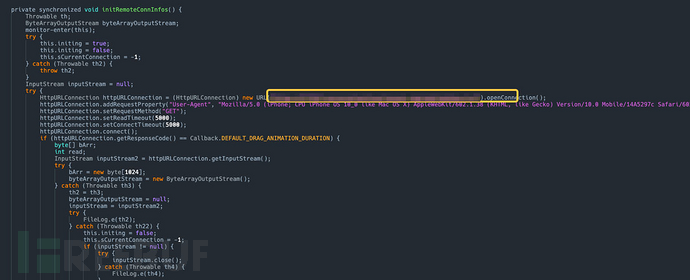
Based on the results of automated analysisNetworkConfig.javaThere are obvious problems in the file code, so this analysis will focus on this file.
- Network Configuration Update Mechanism
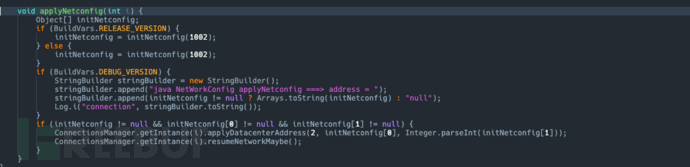
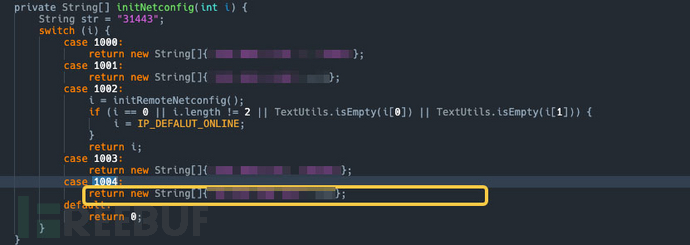
Environmental differentiation: The code differentiates between online and intranet environments. Only the one marked as 1002 is the online environment, which requires updating the network configuration.
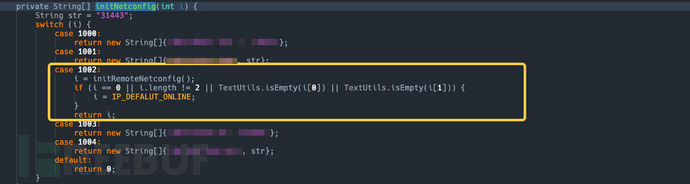
- There are two key functions here
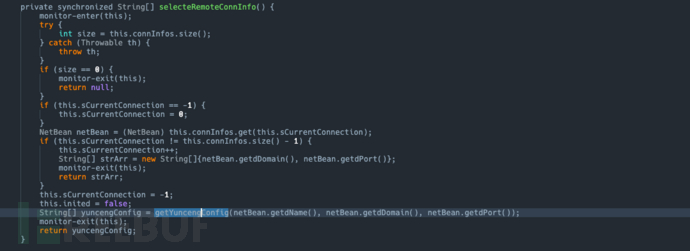
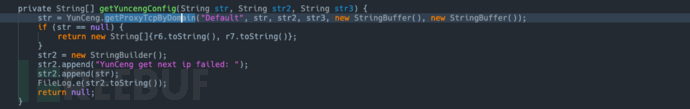
initRemoteConnInfosandselecteRemoteConnInfo
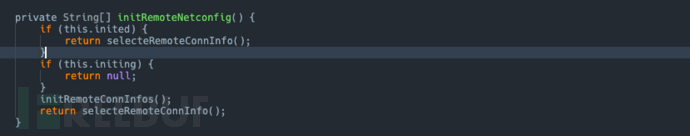
Key Function Analysis:initRemoteConnInfos: Mainly responsible for https://*************.***-**********.********.***/************.***Obtain the target IP and port information.
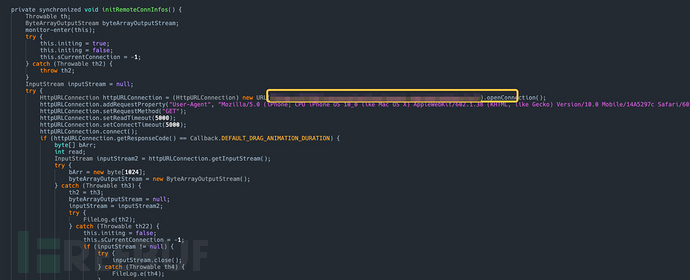
selecteRemoteConnInfo: Using Ali Game Shield to convert the target IP and port into a proxy IP and port to achieve the purpose of hiding the actual IP and port.
Ali Game Shield logic
- Function introduction: Ali Game Shield provides an elastic security network immune to DDoS/CC attacks. Specifically, it generates a dynamically changing proxy IP and port based on the target IP and port provided.
- Challenges and impacts: For network behavior analysis and malicious program network request interception, the elastic security network of Ali Game Shield constitutes a serious challenge. Because the proxy IP and port can change continuously, this greatly increases the difficulty of network tracking and interception.
This sample uses complex network configurations and third-party security services (Ali Game Shield) to hide its actual network behavior, thereby increasing the difficulty of analysis and tracking. These features further prove the high professionalism and concealment of the malicious sample.
YunCeng.getProxyTcpByDomainThe decompiled code is as follows:
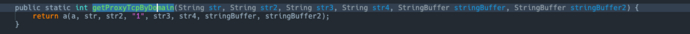
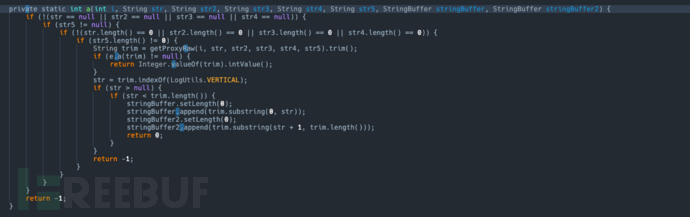
According to the older version of the document on the official website of Ali Game Shield,getProxyTcpByDomainThe first four parameters of the function are as follows:
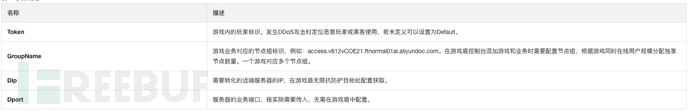 function's last two parameters are used to return the proxy IP and port corresponding to the input target IP and port.
function's last two parameters are used to return the proxy IP and port corresponding to the input target IP and port.
After further analysis of the above code, we found that the returned proxy data is eventually passed to ConnectsManager.
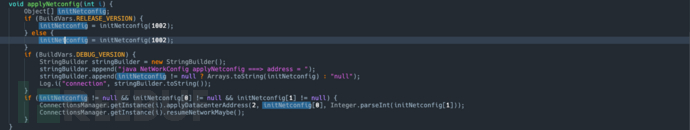
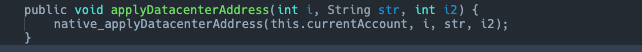
We noticed that this is a nativefunction. Under normal circumstances, we need to perform reverse engineering analysis.soto obtain the corresponding code. However, since we have mentioned earlier that this sample code has a high similarity with Telegram Android, we decided to directly refer to the source code of Telegram Android for analysis.
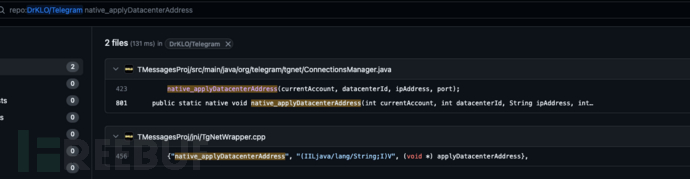
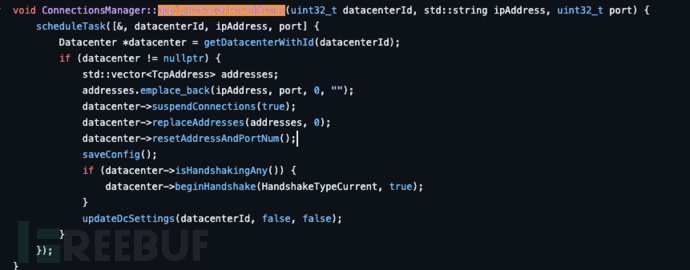
In this step, the returned IP address and port number are set to the datacenter object of ConnectManager, and the handshake process is then reinitiated to establish a new connection. This operation achieves the server switching of network communication between the sample and the cloud. Up to this point, the malicious sample has successfully established a new communication channel with the remote server through a new IP and port.
Interception methods:
After detailed analysis, we have completed the review of the main network request evasion interception behavior of the sample. The sample cleverly uses anti-DDoS services, effectively avoiding traditional protection methods based on fixed IP request interception by constantly changing the IP address and port of the requests.
To comprehensively block the network requests of this sample, it is necessary to combine static and dynamic analysis to find out how the sample utilizes the Ali Game Shield service and intercept relevant network communication channels accordingly. The specific interception strategy can focus on the following three aspects:
- Intercept the sample by requesting the target IP address and port from Ali Game Shield.
- If the first interception strategy has not been successfully executed, then it is also necessary to intercept the default IP and port preset in the sample. Specifically, all requests pointing to
****.**.********.***network requests.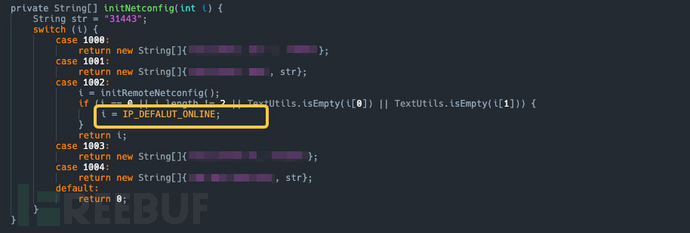
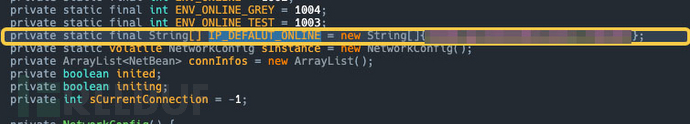 During the灰度测试阶段, if the first two interception strategies have not been successful, then attention should be paid to the third default IP address preset in the sample, namely
During the灰度测试阶段, if the first two interception strategies have not been successful, then attention should be paid to the third default IP address preset in the sample, namely **.***.***.***. All network requests pointing to this IP should also be intercepted.
These network requests are cleverly hidden deep in the code and require a comprehensive application of dynamic and static analysis methods to accurately identify them, which undoubtedly adds additional challenges and workload to security countermeasures.
Family variant analysis
During the continuous tracking of such malicious APPs, we found a new variant with an MD5 hash value of 61eea96bae6e53b6806d974cf35877df. This new sample has made a significant change: it no longer relies on Ali Game Shield but has turned to using Qiniu Cloud's DoH (DNS over HTTPS) service. The specific usage method is as follows:
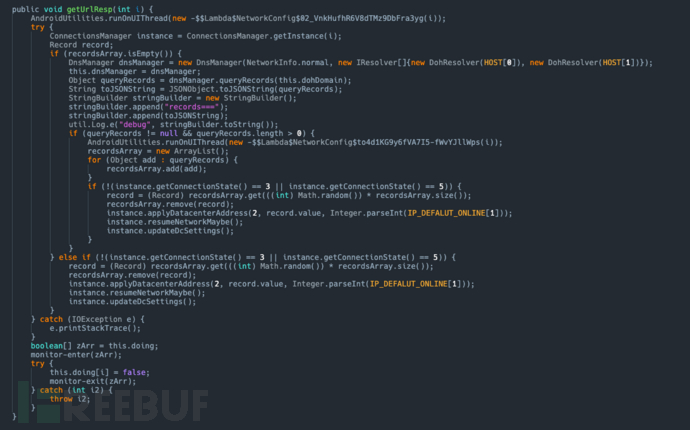

In this new variant, the attacker configures the address in the HOST to be the dnsServer of Qiniu Cloud's DnsManager. Then, the DnsManager is responsible for DNS queries. This change not only indicates that the attacker is gradually familiarizing themselves with and exploiting more advanced network services but also increases the complexity of analyzing and intercepting their behavior.
In this situation, the sample dynamically changes IP addresses through its own controlled dnsserver. This setting allows attackers to use tools similar to Ali Game Shield in the backend to randomly return different proxy IP addresses, thereby hiding the real IP address. If the DNS query fails, the sample will revert to the preset IP and port, further increasing the complexity of counter-analysis. This multi-layered network behavior strategy not only increases the difficulty of analysis work but also creates additional challenges for effective interception.
Summary
In the comprehensive analysis of this malicious sample, we can see that the sample exhibits complex and stealthy behavior characteristics at multiple levels:
The sample extensively borrowed source code from Telegram Android and made numerous customizations and additions, which increased the complexity of analysis.
Network behavior:
- Early versions mainly used Ali Game Shield for dynamic IP and port switching to avoid network interception.
- The new variant has switched to using the Qiniu Cloud's DoH service, further enhancing its stealthiness.
Combination of dynamic and static analysis: Since the sample uses various methods to conceal its network behavior and code structure, both dynamic and static analysis need to be used simultaneously to fully understand its behavior patterns.
Countermeasures: Effective interception of this sample requires a detailed analysis of all communication paths and dependencies used, and interception should be targeted at these specific paths and libraries.
Update and evolution: This sample has a high update frequency and diversity, requiring continuous attention to its variants and updates.
In summary, this malicious sample demonstrates a high degree of complexity and stealthiness, requiring a comprehensive analysis of various methods and continuous tracking of its changes to develop effective protective measures.
IoC
Hash:
0a731ace7a01349d8c103ad5dc7fc230
c0c2c778f447c8e8e007f23fc9884270
f911559ca31a67644839fb3441b4353a
90a214d758e139e7604d2a0ffeea636d
07adcaaba76313bb403e272af0b410fb
cc77e56537f42e9f9929414e0c6ee5fa
3500969225597c6ef74bbcd430db639b
9e2430fbf9fda9d88c64fa21be0397be
cad71847f3d233392858241108379ba9
4c0ef460d9002529e5c4246a01b4bb3b
61ad63ee3527a0386728d7b7fd7327c1
f5e0cb000781595282b08c0c13aa2ccd
aa9b9fa34ecccd73586a75a5c2b472da
1ee643ce7569b8badef4893a06a65529
83769c54646c9b7fb4395e2bd2bbd8ca
340795cd070438dbab4224b39de2bb32
c5381d9b17d4d870f4187bd92fffc4f1
34db2c2aa456d943c0cee500895b6ebb
903a976b8469ffc51f865064c1c99134
e51e972cab85b126aa714367a6b3580d
0e8f47f6fd85f87ec856b8338cb1a58e
5c901f89a693a81a60da1f0314fc8c00
8bf147393b4349e6d30855f5a1994122
0724e81bab5c781229d8a412b078a470
84bad8f49ab890c25ccd33b751d875a1
dbce0d16142d5492ff7c3304ee24c118
cda08dd3ba29229da293efb299a0071b
7870d55613d69067f432bcfced6b9395
e01a68ff450ca8e9e8a148060503aa4d
a248ce6f396c27ebc7f5a660e367eae8
c80a11363e216d7e32e17fa044672369
79bcd908766033491409c62015488049
55e3dfe425fb5372542909a63ed007e5
5bb38f2601937a538d068047dc32937b
a1b5de8df8741deb655c84d3dad536fd
C&C:
47.104.243.76:31537
183.230.11.65:55555
42.193.237.57:30003
175.178.152.90:30003
139.199.224.36:30003
111.230.69.193:30003
36.255.220.245
https://ff119f.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://axvsag103sdvsbd.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://126sand.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://bw36file.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://bw1cloudfile1.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://ff115f.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://bw5file1.oss-cn-hangzhou.aliyuncs.com/andrioddunv.txt
https://80xbdfs.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://bw89file.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://6oiue.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://ma36twegt.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://6fdhgbtreh.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://fdasfewmm26dsafdas.oss-ap-southeast-1.aliyuncs.com/andrioddunv.txt
https://gg81fnew.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://ev10mgmt.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://26qewsdz.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://file100fg.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://jbsa111.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://cxvsdf121gfhe.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://wb25f.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://abhjbw115jks.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://bhjasd183.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://bw39file.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://if90f.oss-accelerate.aliyuncs.com/andrioddunv.txt
https://8.212.47.67/dns-query
https://8.212.102.80/dns-query
https://8.212.1.70/dns-query
https://8.212.101.76/dns-query
https://47.57.138.89/dns-query
https://47.57.2.128/dns-query
Smile.isk5uz.com
Maomi.gz.bw36diannew.com
abab.gz.bibi115s.com
Pulo.gz.bw6nmddk.com
Qiaojiar.gz.bw111uam.com
guo.gz.awwb90.com
ttt.gz.iudjd119.com
Facai.gz.bw26f.com
Sichunge.bj1.mumrsn8i.com
nqo5.hz.sjdnbw81.com
deadf.gz.wknbw25.com
Lvcha.gz.bw183khgftdfgh.com
Wngd.gz.bw121ffu.com
Gsnm.gz.bw115dsvwerfoijsd.com
Xecm.gz.bw6st.com
Huachuanghulian.gz.bw16wcnmader.com
Qingyimianmian.gz.bw39top.com
Zzh.gz.bw126zzhyyds.com
wrty4.gz.az25ru.com
roklw.gz.skmw100.com
Ommm.gz.bw103hgycgi.com
Edko.gz.bw36a.com
Aelo.gz.bw112uuuuuuu.com
Dandan.gz.bw26yidingyaotingzhu.com
Original link:Lian Security
Disable SSL Pinning (ssl_pinning_plugin)
How to use large language models (LLMs) to automatically detect BOLA vulnerabilities
How to conduct offensive and defensive exercise risk assessment for AI systems: Red Teaming Handbook
facebook hire through hacker cup(Facebook Hacker Cup)
Analysis of Agent Tesla's new infection chain
Analysis of the Agent Tesla spyware disguised as a screen saver program
Build an information security visualization platform by yourself (Part Two) Missle Map
hiring a hacker form with terms and conditions dos(Terms of use)
评论已关闭