0x00 Preface
With the opening of the two-month-long network defense action, so far, many units have suffered from red team penetration attacks such as phishing, poisoning, and lateral movement. Last time we mentionedHow to Be an Excellent Blue Team Member (External Network Part)This article still refers to the ATT&CK model and actual cases to describe the execution, persistence, and privilege escalation modules, draw and analyze the attack techniques, find and defend against the threats brought by the internal network.
0x01 Execution
Analysis of Attack Techniques
In the execution phase, the main threats faced are two, namely, fileless Webshell (memory horse) and execution of entity malicious software. We will analyze the possible alarms from the network level and strike them accurately.
1. Traffic Mining

Different from the footprinting, penetration, and other attacks on the external network, the transmission at the execution level is mainly documents, programs, images, and scripts, with obvious alarm features. It is advisable to focus on finding upload ports and auditing uploaded files.
Analysis Indicators
1.1 Summary of Situation Awareness
Currently, most of the situation awareness on the market can be achieved through the assets and interfaces existing in traffic mapping systems, such as Weibu, DeepinServe Situation Awareness, Tianyan, and other products, which can audit files by sorting out the upload interfaces.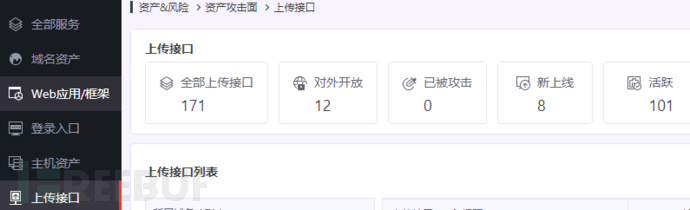
1.2 Traffic Packet Feature Search
If the function does not exist in the situation awareness, it can also be manually discovered and sorted according to the features. The following is a form of upload type:
POST /upload HTTP/1.1
Host: xxxx
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryxJoimunuCt1r2RmT
Accept: application/json, text/plain, */*
Connection: close
------WebKitFormBoundaryxJoimunuCt1r2RmT
Content-Disposition: form-data; name="file.exe"
50 4b (hexadecimal is used for demonstration convenience, and the actual traffic packet is ascii characters)
------WebKitFormBoundaryxJoimunuCt1r2RmT
By analyzing the form, searches can be performed for the upload ports through the following features
Content-Type: multipart/form-data;
------WebKitFormBoundary
name="file"
504b file headers (hexadecimal search)
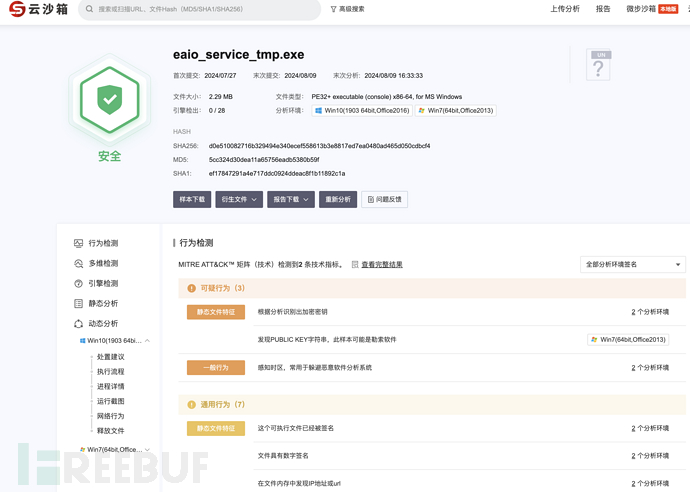
Sandbox Analysis
After obtaining suspected malicious files, the files should be packaged to avoid secondary infection. In the network defense environment, in addition to the deep analysis of virus files for special needs, the most commonly used method is to scan and kill attacks through sandboxes or virus scanners. Once suspicious behavior is detected, it can be directly blocked and intercepted to save manual time. The following are commonly used malicious software analysis websites:
VirSCAN: https://www.virscan.org
VirusTotal: https://www.virustotal.com
NoDistribute: http://nodistribute.com
Weibuyun Online Cloud Sandbox: https://s.threatbook.cn
Tencent Habo Analysis System: https://habo.qq.com
Qianxin Threat Intelligence Center: https://ti.qianxin.com
Great Sage Cloud Sandbox Detection System: https://mac-cloud.riskivy.com
2. Defense Techniques
Needle
评论已关闭