Data is becoming increasingly important.
On December 19, 2022,Opinions of the CPC Central Committee and the State Council on Establishing a Basic System for Data and Giving Full Play to the Role of Data ElementsBuilding a basic system for data property rights, circulation and trading, income distribution, and security governance, and put forward 20 policy measures.

On February 27, 2023, the CPC Central Committee and the State Council issuedOverall Layout Plan for the Construction of Digital ChinaIt proposes to accelerate the construction of a digital China.
On March 7, 2023, according to the proposal submitted by the State Council on the reform of the State Council institutions for consideration and deliberation by the State Council,Establishing a national data bureau。
With the continuous emphasis of the state on data and the deepening of data utilization, the risks of data leakage and abuse are becoming increasingly prominent. Ensuring data security is becoming the most urgent and fundamental security issue in the digital economy era.
What is data security?
Article 3 of the 'Data Security Law of the People's Republic of China' defines data security as follows:By taking necessary measures, ensure that data is in a state of effective protection and legal use, as well as the ability to ensure a continuous state of security.
Data security includesThe planning, establishment, and implementation of security strategies and processes provide proper authentication, authorization, access, and design for data and information assets.Although the detailed situation of data security varies from industry to industry and country to country, the goal of data security practices is the same, that is, to protect information assets according to privacy and confidentiality regulations, contract agreements, and business requirements.
The importance of enterprise data security
Data is the lifeline of an enterprise。
IfFinancial dataOnce lost, all plans and transactions may be shelved due to the unclear factors of financial data loss, causing direct losses to the enterprise.
Talent, as an important support for an enterprise, is the foundation for its continuous development, and also an embodiment of core competitiveness. IfHuman resources dataThe consequences can be imagined if lost or leaked.
R&D capability as one of the core competitiveness of enterprises, what it embodiesData such as intellectual property and patentsThey are important wealth for enterprises.

With the expansion of business fields and the rapid expansion of scale, related data security risks also arise, such as viruses, worms, spam, spyware, rogue software, data interception, sniffing, eavesdropping,肆意泛滥, internal secret leakage, etc., all of which threaten enterprise data security at any time.
Therefore, strengthening data security construction, allowing enterprises to be in the best state in market competition, can help enterprises establish a solid foundation for data and go further.
How to build a solid foundation for enterprise data security?
International consulting firm Gartner points out:Data security governance is not just a set of product-level solutions combined with tools, but a complete chain that runs through the entire organizational structure from decision-making to technical layers, from management systems to tool support.
Currently, many data security manufacturers solve customers' problems and needs in a single aspect by providing a single-function solution, which cannot build an integrated security protection capability for the entire lifecycle of data for customers.
The ZTESoft data security solution is centered on data, focusing on the entire lifecycle of data, fromOrganizational construction, system processes, technical tools, and personnel capabilitiesFour capability dimensions for enterprises to build a data security protection system, forming a closed-loop sustainable data security management, monitoring, and operation capability.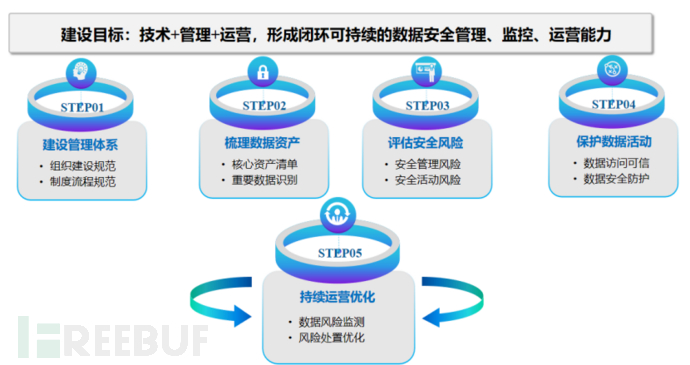
First stage: Build a management system
Through the construction of a data security management system, form data security organizational responsibilities, norms, work processes, and establishData security management mechanism。
Second stage: Sort out data assets
Through the work of data asset inventory, clarify the scope of work and information basis for data security governance, classify according to classification and grading standards and management systems,Output the core asset list。
Third stage: Evaluate security risks
Based on national, industry and other relevant data security technology and management standards, from the perspective of risk management,Analyze the importance of data assets。
Determine key evaluation objects, identify various application scenarios involved in the evaluation objects, evaluate the threats and the possibility of security incidents caused by the exploitation of vulnerabilities in the application scenarios of data assets, analyze and calculate the risk value of data assets, and combine with the actual situation of the organization, to give reasonable data asset risk disposal suggestions.
Fourth stage: Protect data activities
AdoptingZero trust access mechanismAnd refine access control for access behavior, realize unified authorization management of personnel on data states such as 'available and visible, available and invisible, and unavailable and invisible', prevent lateral attacks by malicious users,While achieving the circulation of data elements, protect the core data of enterprises and personal privacy data。
Fifth stage: Continuous operation optimization
Providing systematic and normalized data security operation services to assistBuilding a 7*24-hour all-around security operation system。
By continuously optimizing data security strategies, updating data security specifications, and proposing rectification suggestions for the handling methods of occurred data security incidents and subsequent risks, we achieveFrom institutional guidance and strategy formulation, to event identification and risk management, and then back to optimizing and improving systems and strategies.The operation closed loop.
评论已关闭