
PasteMonitor tool allows us to perform the following two major tasks (for educational purposes only):
1. Download the newly released public Paste every day:
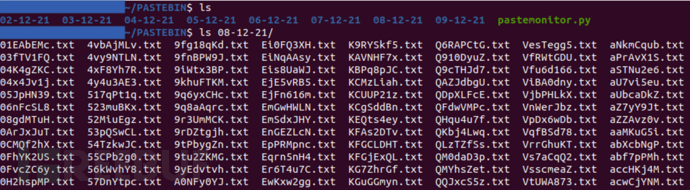
The average number of Paste released daily is 1000-3000, with file type as '.txt'.
2. Automatically send email notifications
We can set up a dictionary file, and when PasteMonitor crawls content that matches the keywords in the dictionary, the tool will send an email notification to the user:
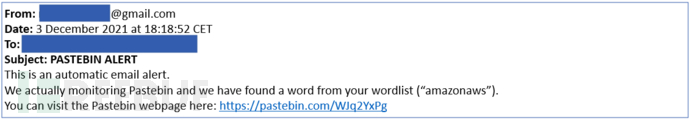
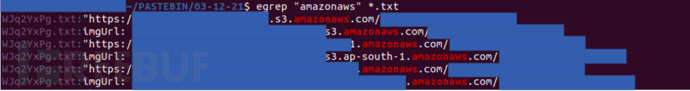
If the target Paste cannot be accessed directly, we can also find the Paste content (the Paste ID in the figure below is 'WJq2YxPg') on our computer or server through the Paste ID:
Tool preparation
Before starting to use PasteMonitor, we need to prepare the following contents:
1. Obtain onePastebin Pro account
2. In the "Account&Whitelist IPEnter your computer/server's IP address in the "
3. Activate the email account and authorize third-party applications to access
4. EnableTwo-factor authentication feature
Next, write the following content into 'pastemonitor.py':
1. Electronic mail credentials (email address and password)
2. Email notification recipient (recipient)
Dictionary file
In the 'wordlist.txt' file provided by the project, we can add the required keywords line by line.
Tool download
Researchers can use the following command to clone the source code of this project locally:
git clone https://github.com/pixelbubble/PasteMonitor.git
Tool dependency installation
pip3 install -r requirements.txt
Tool usage
The use of this tool is also very simple, after configuring the relevant parameter options, simply run the following command directly:
python3 pastemonitor.py
License Agreement
The development and release of this project followMITOpen Source License Agreement.
Project address
PasteMonitor:【GitHub Gateway】
Reference materials
https://pastebin.com/doc_scraping_api
https://myaccount.google.com/u/2/signinoptions/two-step-verification
https://myaccount.google.com/u/2/apppasswords
https://ljmocic.medium.com/send-an-email-using-python-and-gmail-4ebc980eae9b
评论已关闭