“According to fan爆料,at 2 a.m. on January 5th, X Station Company sent a phishing link to all employees via internal email, resulting in several colleagues being deceived, with the total amount defrauded being around 80,000 yuan. It took IT until 1 p.m. in the afternoon to delete all the phishing emails. There was no company-wide email notification, leading to continuous deception. There was no immediate notification to all employees in the case of consecutive deception. No company-wide email was sent, and no compensation was provided.”
From the pictures displayed in the attachment of the microblog content, the victim employees have established a 'Phishing Email Victim' group, and there are currently 72 people in the group. The response from the HR department of the relevant department that the deceived employees of X station consulted is to recommend that colleagues report the case themselves. Some employees in the group believe, 'Is the company not supposed to take subsequent responsibility if the email sent from the corporate email causes the staff to be deceived?' And some employees said, 'I didn't get the money back, but I can make a show of reporting the case, and it's better to say something.' 'But the company doesn't want to take any responsibility.'


I think this case has educational value, let's share it with everyone simply, and also put forward a question for ourselves, if we encounter such an attack, is our emergency response support model sufficient to achieve rapid response? We don't talk about the so-called emergency plan, we need something that can be implemented, can help SOC engineers to respond quickly, and quickly locate the specific steps proposal.
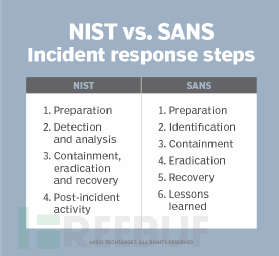
For the emergency response steps under the SCF (Security Control Framework) framework, I prefer the set of SANS, namely the PICERL process. For the phishing emails of X station, we try to deal with the emergency response process of the phishing emails through modeling.
Before modeling, it is necessary to propose some targeted questions first, and solve the problems around the question in order to have practical implementation significance:
- The user's email and password have been leaked, is the source of the leak from other phishing emails?
- X station uses Exchange Online, is MFA enabled for OWA login of the email?
- How to bypass SPF/DKIM/DMARC if it is sent from a third-party email? (Not within the scope of this case)
- With the presence of traditional characters in the email, how did the staff fall for it so easily? Have there been regular phishing email security awareness training sessions?
- Is there any possibility of optimizing the phishing email detection mechanism of X station?
- Is there a reporting channel for phishing emails in the emergency response of X station?
- The deletion of phishing emails by X station took about 11 hours, has there been any improvement in the foundation?
- Is there an emergency response shutdown mechanism implemented by X station for the outbreak of malicious events?
Identification, detection
- Other related alerts from the SIEM monitoring platform
- Notifications from email server platform viruses, sandbox alerts, including but not limited to HASH, IP, and domain
- Notification of phishing emails from users
Analysis, analysis
- Obtaining the email of the victim
- Obtaining the username of the victim
- Obtaining the hostname of the victim's host
- Obtaining the network connection information of the victim
- Obtaining the process information of the victim's host
- Obtaining the browsing records of the victim's browser
- Obtaining the domain credibility analysis of phishing emails
- Obtaining the credibility analysis of the attachment and URL of phishing emails
- Obtain the macro analysis of the phishing email
- Obtain the sandbox running status and screenshots of the phishing email
- Obtain suspiciously infected users, including recipients, forwards, replies, clicks, and related data
Containment, Control
- Close attack vectors, including but not limited to killing running processes, residual files, file handles, etc.
- Limit network connections, such as through firewalls or host HIDS, to restrict ports, such as retaining only 3389 ports for investigation and evidence collection
- Isolate hosts, which can be blocked by terminal control systems such as EDR
- Reset user password
- Reset user MFA
- Restart, shutdown, PE boot, etc.
Eradication, Elimination
- Ban the suspicious domain names provided by the phishing email
- Ban the suspicious links provided by the phishing email
- Ban the hash of the attachment provided by the phishing email
- Ban the C2 server IP addresses involved in phishing emails in the sandbox
- Disable user accounts
- Remotely delete relevant emails on the server that match the phishing email
- Submit phishing email related IOC to security suppliers
Recovery, Restoration
- Check the patch update status on the victim's host
- Check the antivirus and endpoint control system EDR status on the victim's host
- Use third-party antivirus programs to perform full system scans
- Restore Disabled User Accounts
- Restore Limited Network
- Reset Images
- User Security Awareness Training and Assessment
Lessons Learned, Reflection
- What exactly happened and when?
- How do staff and management perform when handling events?
- What information needs to be obtained as quickly as possible?
- Have any steps or recovery actions been taken that may hinder the spread?
- What different approaches will staff and management take when similar events occur next time?
- How can information sharing with other departments be improved? Is there a common phishing email reporting channel?
- What corrective measures can prevent similar events from occurring in the future?
- What precursors or indicators should be noted in the future to detect similar events?
- What additional tools or resources are needed to detect, analyze, and mitigate future events?
- Did it follow the prescribed standard procedures? Were they sufficient?
- Can the emergency response process be automated to enable faster handling and response to threats?
The specific implementation steps will not be elaborated here. Each enterprise has a unique security operation model, which requires different adaptation work to explore the best practices that are most suitable for the enterprise. Copying may lead to problems that cannot be progressed, but the SCF framework model has its merits. Different enterprises can also ask themselves questions based on such a framework, continuously adjust and optimize, and thus be able to discover, respond, and recover more efficiently and quickly.
评论已关闭