Zhang San reported that a machine is infected with a virus.........
1.Firstly used 360 to delete everything, and found that there are indeed these malicious programs.

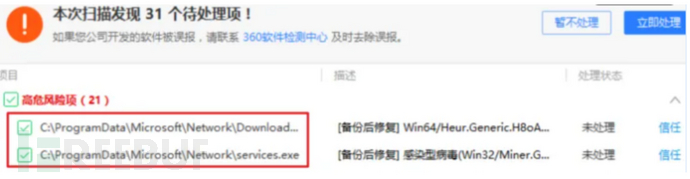
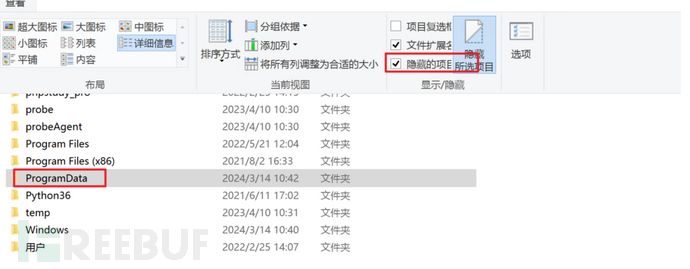
2.Didn't directly use 360 to kill it, wanted to take a look, found that the programdata path is hidden by the system, so cancel the hidden
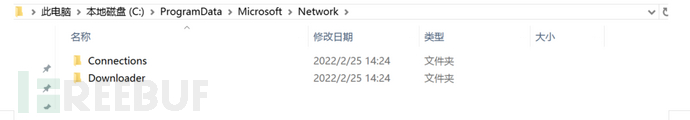
3.Got into the directory where the virus is located, but didn't find any malicious programs
4.After a series of operations, let's directly talk about the result, attrib command to cancel hidden, and then we could see the malicious files
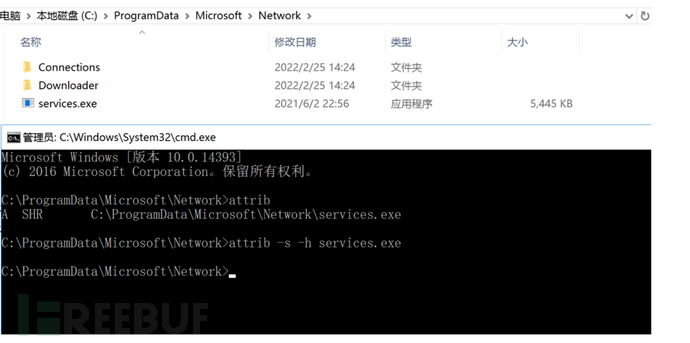
5.Wanted to delete directly, but couldn't delete and didn't show what was occupied
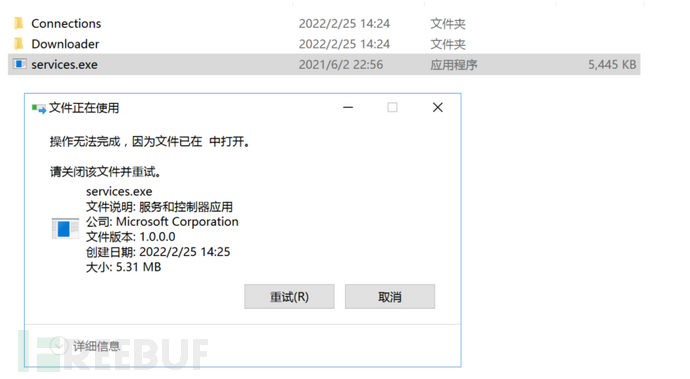
6.Looked at tasklist and found three programs
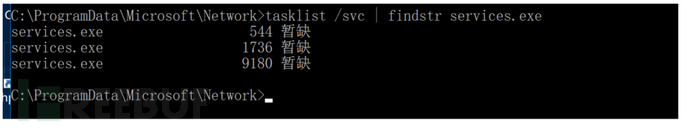
7.Delete everything all at once, but found that nothing could be deleted in the end......
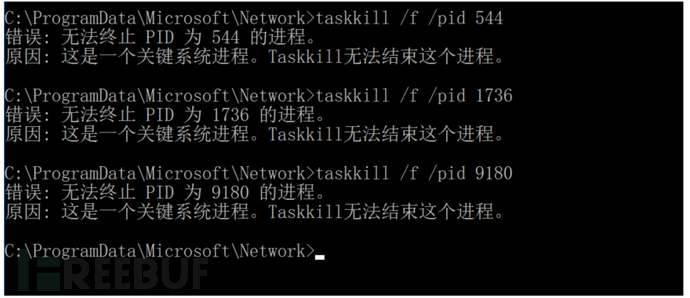
8.Cannot see in the task manager either
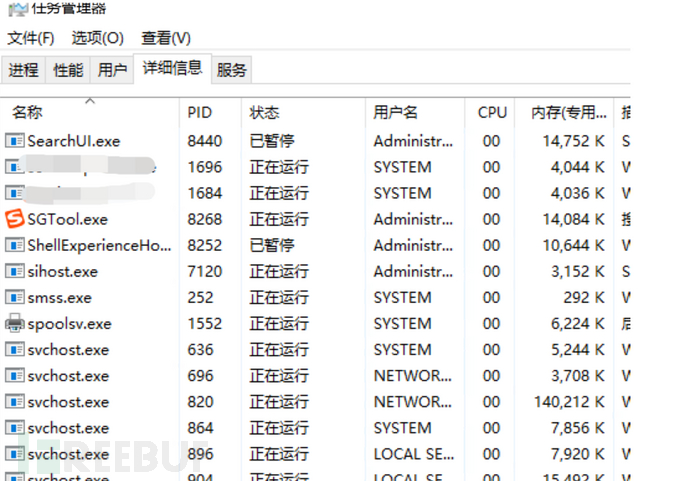
9.Vulcan剑出鞘了,找到两个恶意进程,directly end the process tree
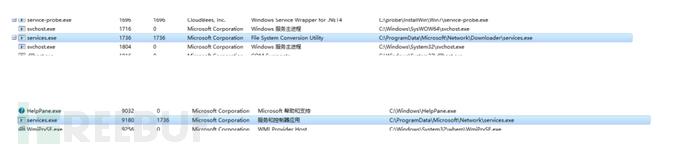
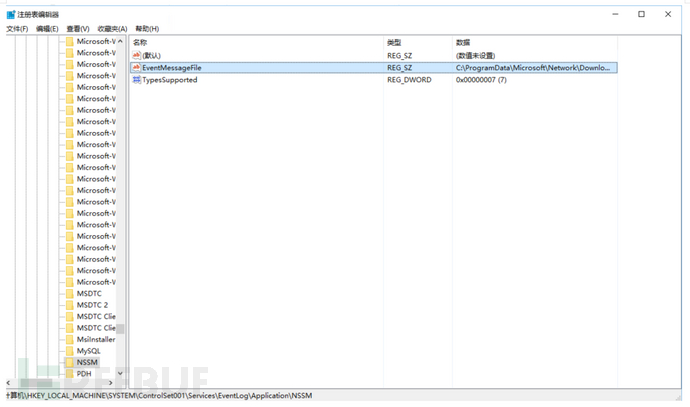
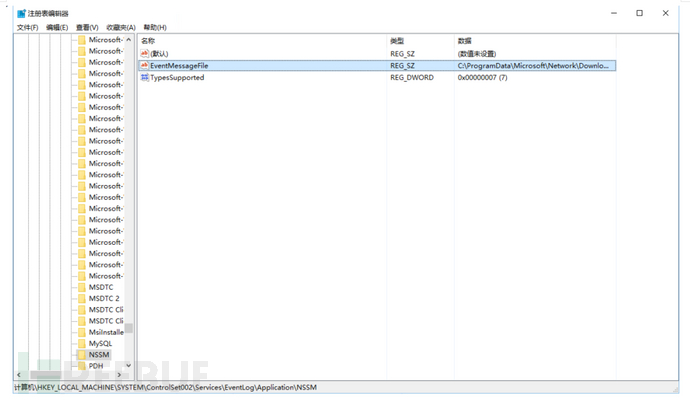
10.Delete services.exe and it's comfortable.....
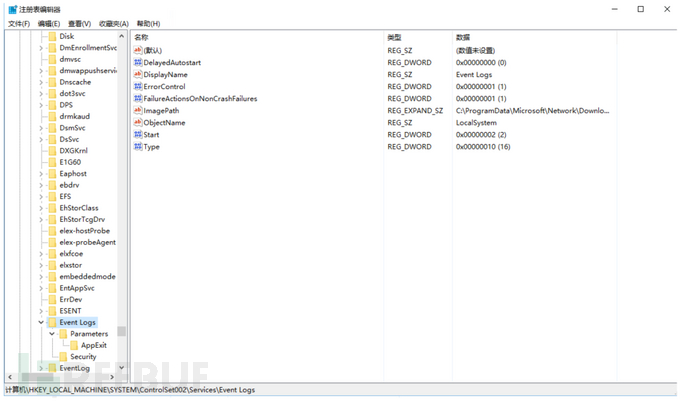
11.Look at the registry to see if there are any permissions maintained, and delete everything all at once.
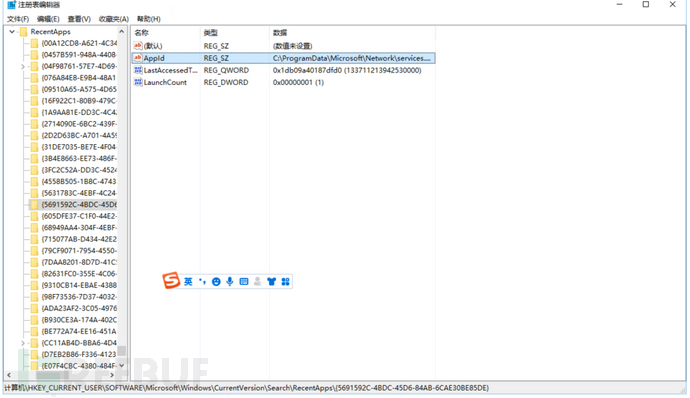
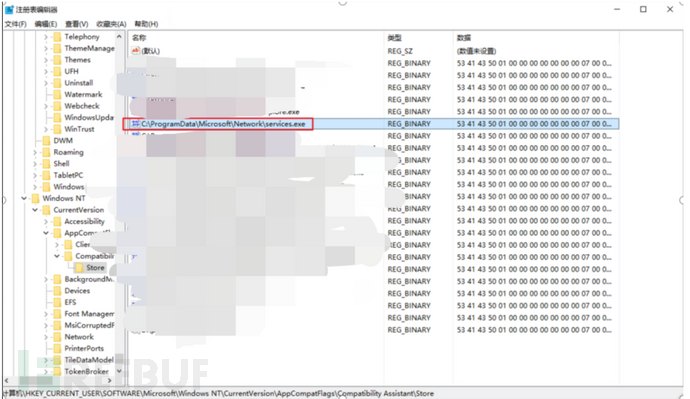
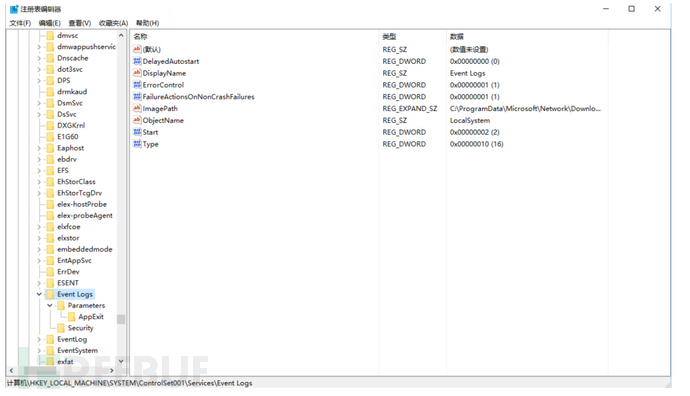
Follow the Cybersecurity Medicine Water Brother to fight the target field (emergency response)
Emergency response of the Windows system from the perspective of permission maintenance
II. Emergency Response Case (a customer in the education industry of a certain district)
Emergency Response: Analysis of Remote Software Logs
评论已关闭