Preface
Recently, the author published an article titled '700 government and enterprise office systems suspected of having RDP risks', which mentioned that multiple OA systems such as *Butterfly and *Friend are suspected of having vulnerabilities that can penetrate the internal network and obtain 3389 permissions. At that time, it was warned that it could lead to ransomware or data leakage, and it should be addressed promptly. Unexpectedly, just a few days later, it was reported that *Friend OA was hit by a large-scale ransomware attack...
Therefore, the author delved into the analysis of the commonalities existing in these OA systems, in an attempt to find the attack methods or approaches used by the attacker.
01 Determine the target of the attack

Firstly, it is of course to find commonalities, aiming at the underlying development frameworks of these OA systems, but in vain, as they are not written in the same language nor share the same framework; later, the target was shifted to the systems installed with these OA systems, since the 3389 permission acquisition was mentioned, could it be an operating system vulnerability? But still, there was no result, as there were Windows 7, Windows Server 2003, 2008, etc., and no recent vulnerabilities were found that could directly lead to the penetration of 3389; the target moved to their suppliers, but again, they did not share the same supplier, some were self-developed, some were merged with other companies, and there were no commonalities.
The idea actually ends here. If readers have better ideas to detect the commonalities of multiple OA systems, they can leave a message below the article.
The author's method was to face the music again and send an email to the hacker to ask for a batch of test systems, of course, using a new email account to ask. In one of the system test screenshots sent by the hacker, the author saw a software icon that had never seen before.

After investigation, it was found that this software belongs to 'Xi'an Ruiyou Information Technology Information Co., Ltd.', a virtualization and cloud computing solution provider, with the product name 'Ruiyou Tianyi'. Further investigation found that this software is bundled with multiple OA systems, including the products mentioned by the hacker such as *Dian, *You, as well as medical, financial, logistics, and many other industries.


The general use of the software is to map the 3389 port of the internal machine to the public network, convenient for employees not in the company to work remotely. The solution for the medical industry is as follows, and the rest is similar. Remote office employees only need to access the IP and port of Ruiyou Tianyi on the public network, enter the account and password, and they can directly log into the internal network machine of the company to work.
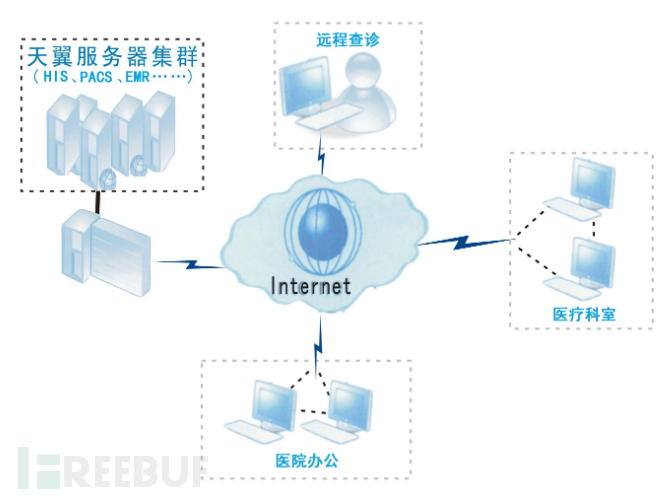
This seems to be a very practical and convenient feature, but the harm can be very great, because the author found that there are weak password situations in Ruiyou Tianyi's client. This is consistent with the situation mentioned in the preface that hackers can take over the 3389 remote desktop. Hackers might have entered from here! It's not some high-end 0day, but the most ordinary weak password; it's not some OA system vulnerability, but the middleware used for management has a problem. This is a decoy of the hacker, always leading the author to OA vulnerabilities, but did not expect that it actually has little to do with OA. Even if OA is updated to the latest version, not updating the Ruiyou Tianyi client is of no help.
02 Speculation and verification of attack process
After confirming that the target of the hacker attack is likely Ruiyou Tianyi software, a preliminary analysis of this software was conducted, and a rule that could be filtered was sorted out. Similar websites of Ruiyou Tianyi exposed on the public network on fofa and zoomeye were filtered. It was found that there are nearly 120,000 historical data in Ruiyou Tianyi websites in China, and as many as 30,000 in the past year. Although many have changed IPs and are inaccessible, not all are systems with weak passwords. However, there are still a lot of systems with risks.
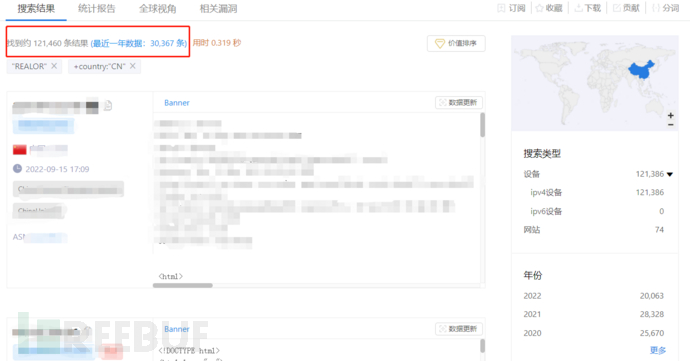
Visiting a few randomly, you can see the pages of versions 5, 6, and 7 of Ruiyou Tianyi. Versions 5 and 6 are similar, while version 7 is the new version.
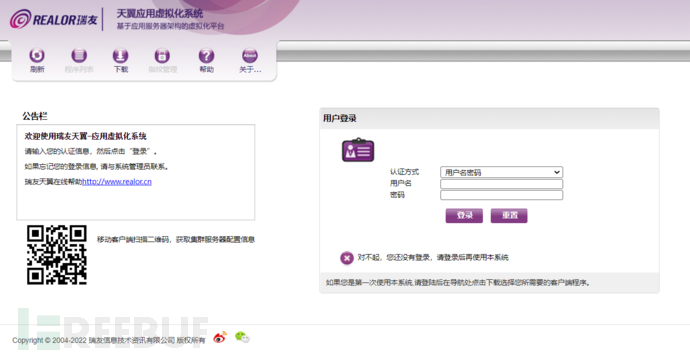
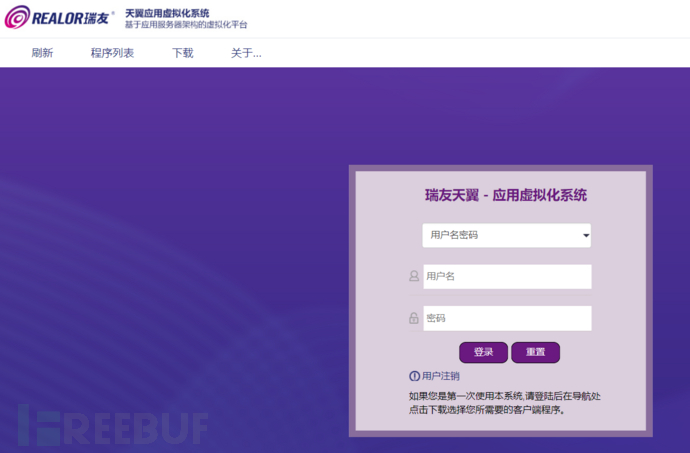
For pages below version 7, clicking 'About' can see which company this system belongs to.
After understanding which company this is, it was natural to try weak passwords in the login box. Since it was a manual test, only admin/admin and admin/123456 were tried. The following picture is the page after the password is correct.
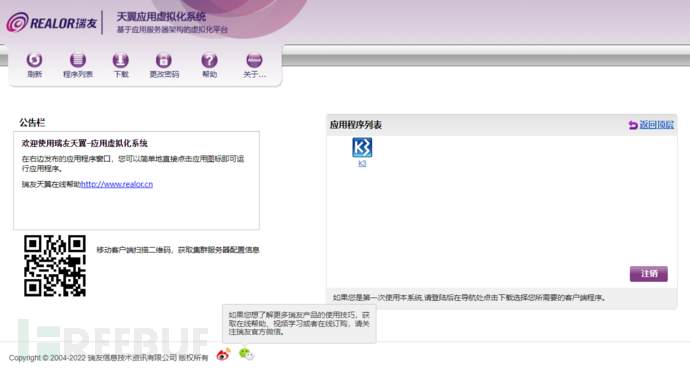
The author tested about 100 pages and found that 18 of them had weak password vulnerabilities such as admin/admin and admin/123456, while other weak password passwords were not attempted, accounting for 18%.
Click the icon of the OA system and find that it uses the RAP protocol javascript:openapp('RAP://xxxxxx'), not http or https protocol, which means it cannot be accessed further through the web. It is speculated that the client of RayoTianYi needs to be downloaded, and there is a download link for the client on the page. After successful download and opening, it is as follows, a small window.
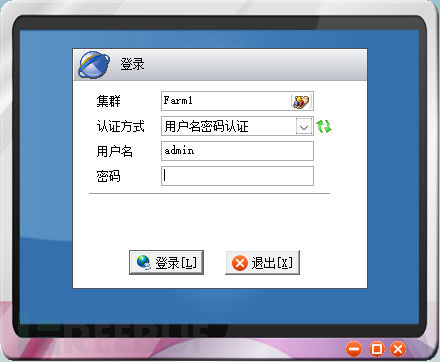
Fill in the IP and port just tested, and the username and password to log in, and enter the internal network machines of the company using that IP.
03 Analysis of Attack Steps
Since the hacker has provided a list of 490+ enterprises, it does not seem like it is copied one by one, as the cost of time for such attacks is too high. In the mentioned attack process, there is a step that can be viewed through 'About' to see the company name, and the hacker may have written a script through this interface to batch obtain company names and form a list. Therefore, the author speculates that the attacker's attack steps may be as follows:
1. Use the Internet of Things search engine to obtain the IP and port of the recently accessible RayoTianYi web server on the Internet.
2. Use tools to batch test the weak password login status of this batch of RayoTianYi login boxes, as there is no limit to the number of attempts, hackers can run a larger weak password dictionary, thus increasing the success rate of brute force attacks.
3. Record the websites that can be successfully logged in with weak passwords from the previous step, and use scripts to batch obtain the names of the companies or units corresponding to these websites, forming a list, which is the list that hackers post on dark web forums.
4. Download the RayoTianYi client for further attacks, penetrate the internal network, and perform data exfiltration or ransomware.
04 Postscript
Enterprises or departments using RayoTianYi should respond and prevent promptly, starting with changing weak passwords, updating to the latest version, or temporarily removing the device and using a more secure VPN for remote return to work.
Weak passwords have been a common topic of vulnerability, but they are still widely used for convenience, especially in some internal network systems. They believe that attackers cannot enter the internal network, so they can set passwords at will. However, they do not know that attackers can enter from elsewhere and horizontally penetrate, at which point, the harm of weak passwords will become very serious. The suggestions for weak password security prevention will not be elaborated here, as there are already many articles on the Internet that have explained it thoroughly. Here, I will share an article that can be read independently.
https://www.nington.com/blog-mfa/downloaddetail_113.shtml
A final announcement: Starting in October, this account will regularly update the attacker traceability topic, analyzing and decomposing from multiple perspectives that can trace attackers, such as IP tracing, metadata tracing (traffic, samples, logs, etc.), and tracing by attack methods. Please look forward to it!
评论已关闭