Introduction
The Avaddon ransomware is called one of the top ten most popular ransomware in the world in 2020 by the author, it first appeared in June 2020 and began to be sold on an underground hacker forum in Russia. The ransomware is written in C++ language and uses RSA-2048 and AES-256 encryption algorithms to encrypt files. The ransomware has various transmission methods, mainly through spam email attachments, JS/PowerShell malicious scripts, and fileless technologies in the early stage, with excellent stealth capabilities. Later, it spread through the Phorpiex botnet, and it was also found that the ransomware spread through spam emails attached with Excel 4.0 macro malicious code.
The encrypted files of the latest variant of the Avaddon ransomware, as shown below:

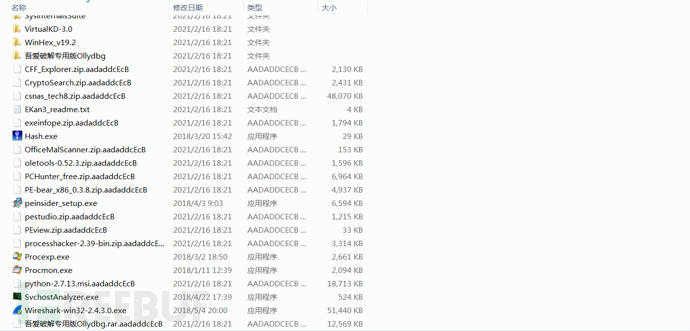
Content of the ransom note file, as shown below:
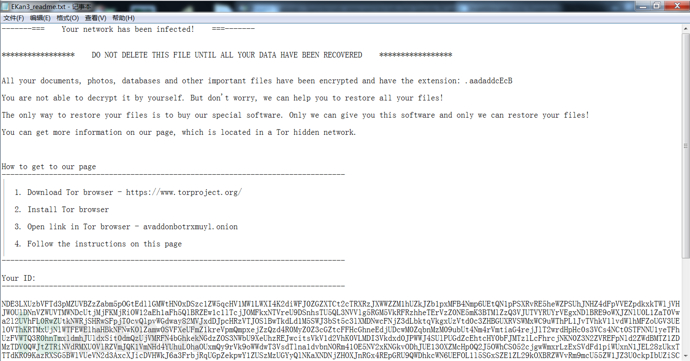 Open the ransomware decryption website via avaddonbotrxmuyl.onion, as shown below:
Open the ransomware decryption website via avaddonbotrxmuyl.onion, as shown below:
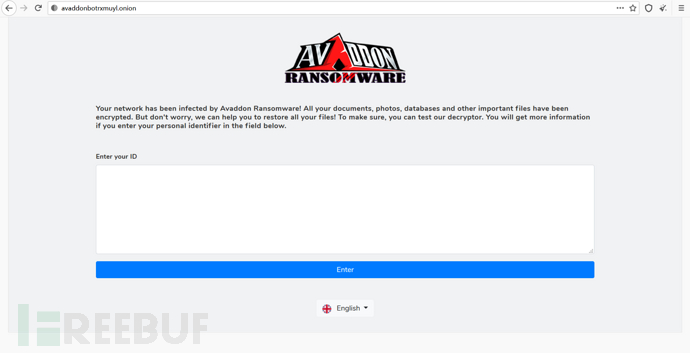 Enter the user ID data as shown below:
Enter the user ID data as shown below:
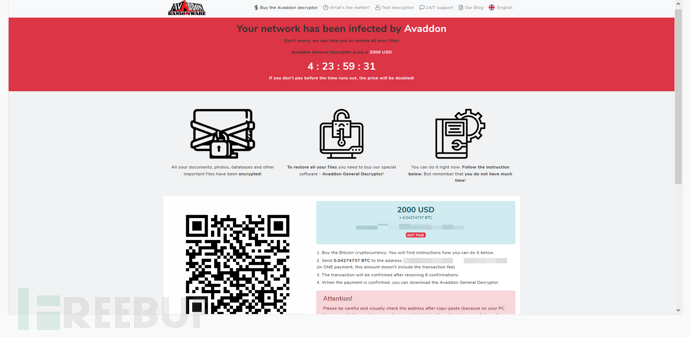
Decryption tool
Foreign security researchers have released a decryption tool for the Avaddon ransomware, the source code address of the decryption tool is:
I downloaded the decryption tool for the Avaddon ransomware from https://github.com/JavierYuste/AvaddonDecryptor, tested it with a virus sample of the Avaddon ransomware, and found that it can indeed decrypt Avaddon ransomware. The decryption steps are as follows:
1. Open the ProcExp tool as an administrator, find the Avaddon ransomware process, suspend the process, and note down the PID of the process, as shown below:
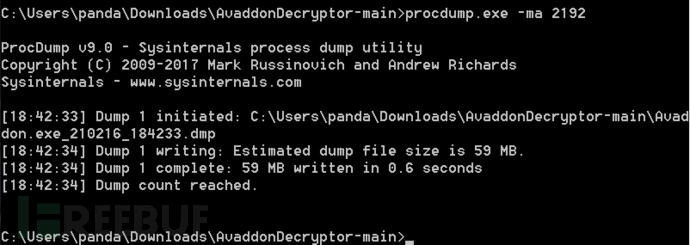
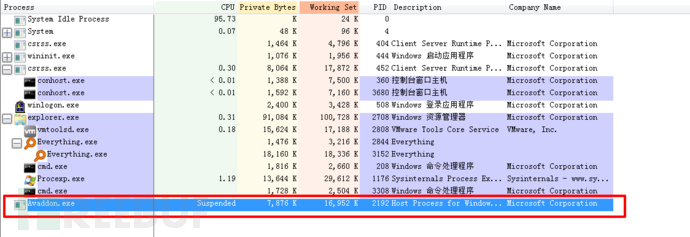 2. Open cmd as an administrator and use the procdump tool to dump the memory data of the Avaddon ransomware process, as shown below:
2. Open cmd as an administrator and use the procdump tool to dump the memory data of the Avaddon ransomware process, as shown below:
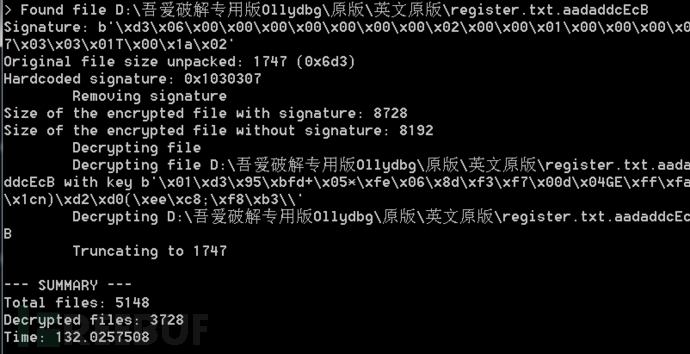
 3. Open cmd as an administrator and run the following decryption command, calling the decryption script main.py, as shown below:
3. Open cmd as an administrator and run the following decryption command, calling the decryption script main.py, as shown below:
![]() 4. After decryption, as shown below:
4. After decryption, as shown below:
Decryption Principle
The author has deeply studied the source code of this ransomware decryption tool, and its principle is to use brute force cracking to search for decryption keys from memory, and then decrypt the files using the keys found. The detailed process is as follows:
1. Brute force search for matching key data in the DUMP file, as shown below:
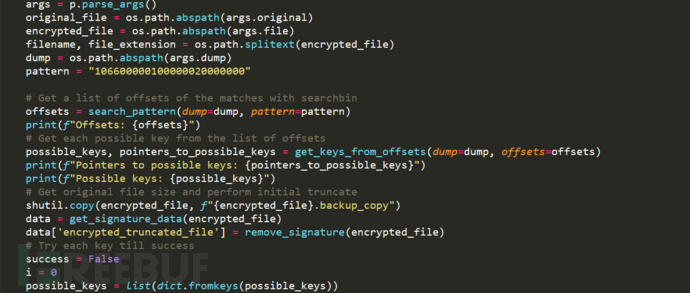 2. Decrypt the file found by searching for the key and compare it with the original file. If the match is successful, it means that the decryption key has been found, as shown below:
2. Decrypt the file found by searching for the key and compare it with the original file. If the match is successful, it means that the decryption key has been found, as shown below:
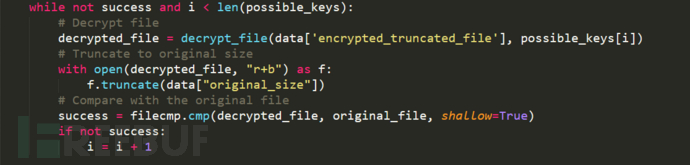
3. Then decrypt the file using the key found above, as shown below:
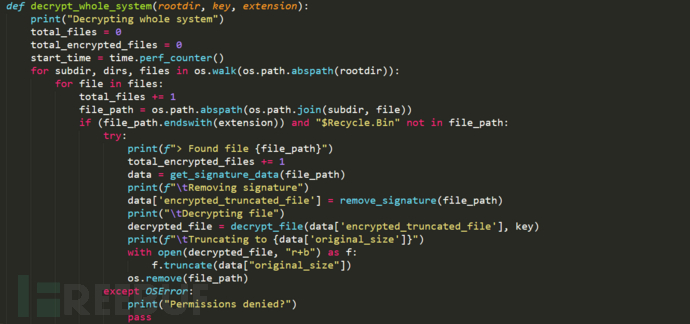
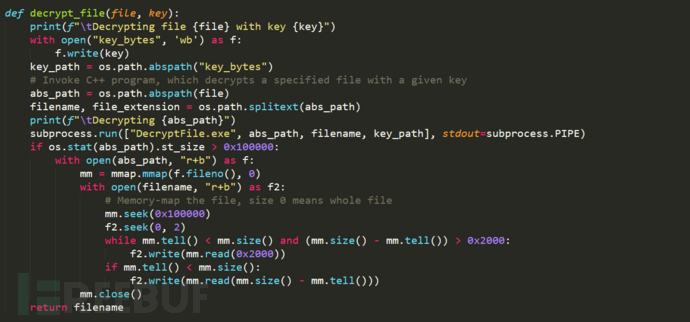
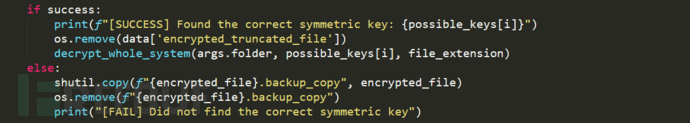 4. The function to decrypt the entire system file is as follows:
4. The function to decrypt the entire system file is as follows:
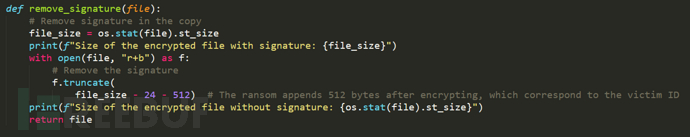
 5. Remove the last 24 bytes + 512 bytes of feature data, as shown below:
5. Remove the last 24 bytes + 512 bytes of feature data, as shown below:
 6. Use the decryption key to call the Decrypt.exe decryption file program to decrypt the file, as shown below:
6. Use the decryption key to call the Decrypt.exe decryption file program to decrypt the file, as shown below:
 The decryption method of this ransomware is basically the same as that of the previous LooCipher ransomware decryption tool, which is to search for possible keys in the DUMP file through brute force search and then decrypt the files using the AES algorithm.
The decryption method of this ransomware is basically the same as that of the previous LooCipher ransomware decryption tool, which is to search for possible keys in the DUMP file through brute force search and then decrypt the files using the AES algorithm.
Summary
Most mainstream ransomware is currently unbreakable. After being infected with ransomware, some enterprises choose to pay ransom to ransomware hacker organizations to decrypt important data and ensure the normal operation of their business. Reports indicate that ransomware hacker organizations earned at least $3.5 billion in ransom in 2020, a 311% increase from 2019. The huge profits from ransomware in 2020 have led more hacker organizations to use ransomware for attacks. In the past, most ransomware was spread through methods such as RDP brute force. Now, most ransomware starts to use various types of malicious software for propagation. Therefore, after an enterprise is infected with any popular malware, hacker organizations may use these popular malware to spread ransomware, and there is a possibility of being infected with ransomware. Data shows that ransomware will become more popular in 2021 and will be more targeted. Due to the huge profits from ransomware, ransomware attacks will remain one of the biggest cybersecurity threats facing enterprises in the coming years. The methods of ransomware attacks will also become more and more diverse, and the attack methods will become more and more complex.
Burpy + frida to implement automatic encryption and decryption on Burp
Burpsuite combined with mitmproxy to achieve encryption and decryption of data
How to decrypt the encrypted data of the mini-program without conducting an audit
1. Use BurpCrypto for爆破 with parameters of prefix + AES encryption
DEScrypt: A hash collision security research tool based on CPU
CenoCipher: a powerful and easy-to-use encryption and steganography tool
评论已关闭