
Android-PIN-Bruteforce requires a USB OTG cable to connect the locked phone to the Nethunter device, which simulates a keyboard and automatically tries to input the PIN code, then continuously performs brute-force attempts.
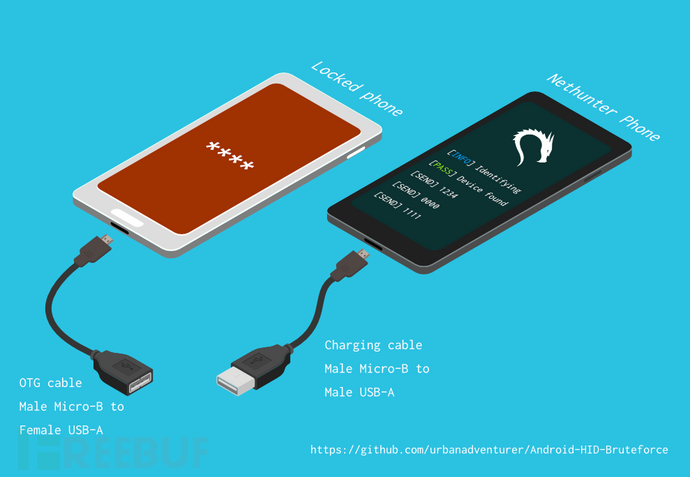
[Nethunter phone] <--> [USB cable] <--> [USB OTG adapter] <--> [locked Android phone]
The USB HID mini tool driver can provide USB HID simulation functionality, which will allow the Android Nethunter device to simulate a keyboard in a locked Android phone, just like directly connecting a physical keyboard to a locked screen phone.
For the Samsung S5, trying all possible 4-digit PIN codes requires approximately 16.6 hours, but it may not be necessary to take so long if an optimized PIN code list is used.
设备要求
一台锁定的Android手机
一台Nethunter手机(或者任意支持HID内核的已Root的Android设备)
USB OTG线缆/适配器
标准充电线
功能介绍
爆破1-10位任意长度的PIN码;
使用配置文件以支持不同的手机;
针对3、4、5、6位PIN码提供了优化后的PIN码列表;
绕过手机弹窗,包括低电量警告;
检测手机何时拔下插头或关机,并在重试时每5秒等待一次;
每尝试X个PIN码后可配置N秒延迟;
日志记录
执行脚本
如果你将脚本安装到了/sdcard/路径下,你就可以通过下列命令执行Android-PIN-Bruteforce了:
bash https://www.freebuf.com/articles/endpoint/android-pin-bruteforce
注意,Android会使用noexec标签挂载/sdcard,你可以可以使用mount命令进行验证。
工具使用
Android-PIN-Bruteforce (0.1) is used to unlock an Android phone (or device) by bruteforcing the lockscreen PIN. Find more information at: https://github.com/urbanadventurer/Android-PIN-Bruteforce Commands: crack Begin cracking PINs resume Resume from a chosen PIN rewind Crack PINs in reverse from a chosen PIN diag Display diagnostic information version Display version information and exit Options: -f, --from PIN Resume from this PIN -a, --attempts Starting from NUM incorrect attempts -m, --mask REGEX Use a mask for known digits in the PIN -t, --type TYPE Select PIN or PATTERN cracking -l, --length NUM Crack PINs of NUM length -c, --config FILE Specify configuration file to load -p, --pinlist FILE Specify a custom PIN list -d, --dry-run Dry run for testing. Doesn't send any keys. -v, --verbose Output verbose logs Usage: android-pin-bruteforce <command> [options]
PIN code list
By default, the tool uses an optimized PIN code list, and users can also choose to use a custom PIN code list.
Cracking PIN codes of different lengths
At this time, you can use the --length command line option.
The following command can crack a 3-digit PIN:
https://www.freebuf.com/articles/endpoint/android-pin-bruteforce crack --length 3
The following command can crack a 6-digit PIN:
https://www.freebuf.com/articles/endpoint/android-pin-bruteforce crack --length 6
Mask cracking
We can use regular expressions to specify the password to crack:
https://www.freebuf.com/articles/endpoint/android-pin-bruteforce crack --mask "...[45]" --dry-run
Project Address
Android-PIN-Bruteforce:https://github.com/urbanadventurer/Android-PIN-Bruteforce
Expanding the Android attack surface: Analysis of React Native Android applications
How to Use Yaazhini to Scan Security Vulnerabilities in Android APK API
How to use CiLocks to bypass the lock screen function of Android
In-depth analysis of the security risks and shutdown posture in SEAndroid
Android penetration testing 12: IDA dynamic debugging so
Incremental installation and Android V4 signature introduction
How to use GeoWiFi and search for WiFi geographic coordinates through BSSID and SSID
评论已关闭