In the ESF (v5.0) 'Enterprise Information Security Framework' proposed by IBM, security governance, risk management, and compliance are one of the layers, and they are at the top level, being the starting point for business-driven security. It mainly includes enterprise strategic and governance framework, comprehensive risk management framework, compliance management strategy, and so on. By assessing the company's business objectives and operational risks, the strategic and governance framework is determined, the comprehensive risk management framework is constructed, the compliance management and compliance strategies are defined, and finally, the information security management and internal control system are established. Therefore, compliance management is a part of the overall construction of enterprise information security.
In the overall design of enterprise information security architecture, compliance management is often indispensable at the bottom level during the definition of information security strategy. There is no squareness without rules, and compliance is both the red line and the bottom line for corporate security construction. However, in the process of a company achieving its business objectives, faced with the uncertainty (i.e., risk) brought by the operation of business systems, ensuring compliance does not guarantee peace of mind, and even cannot avoid compliance risks. Nevertheless, it can enable a company to avoid high penalties, reputational damage, or significant impact in legal or administrative defense.

This record does not describe the compliance management framework, but only selects some parts involving level protection or data security, discussing the practical operation of compliance, peering through the bamboo shoots and seeing a part of the sky.
Information security compliance risk
In the comprehensive risk governance of enterprises, compliance risks and information technology risks are often intertwined. In the process of building enterprise security, if there is a perception of emphasizing technology over regulations, it will leave many hidden dangers for the future development of the business. Enterprise information security risk belongs to a part of information technology risk. In terms of meeting compliance, for example, from the perspective of risk sources, it can be divided into external compliance and internal compliance.
External compliance mainly includes the following parts:
- National legal obligations (Cybersecurity Law, Data Security Law, Personal Information Protection Law, Cryptography Law, etc.)
- Regulatory and departmental regulations (Network Security Review Measures, Regulations on the Protection of Key Information Infrastructure, Measures for the Management of Level Protection, Methods for Identifying Illegal and Unauthorized Practices of APPs, Regulations on the Management of Credit Industry, Measures for the Management of Data Security, and other regulatory requirements)
- Basic requirements of industries or groups (ICP filing, level protection, password management, data classification and grading, risk assessment, etc.)
The main responsibility for internal compliance comes from the comprehensive risk management strategy implemented in the enterprise risk governance strategy under the company law and enterprise internal control specifications, including legal and regulatory risk management related to information security risk governance, information technology risk management, outsourcing risk management, supplier risk, etc., which are common in various management systems and basic specifications that focus on internal control. (For the sake of brevity, risk management will not be elaborated separately here.)
The guiding source of internal compliance management should start from establishing safety compliance requirements and building a standard list, sorting out detailed legal and regulatory clauses, and sorting out the sources of compliance risks.
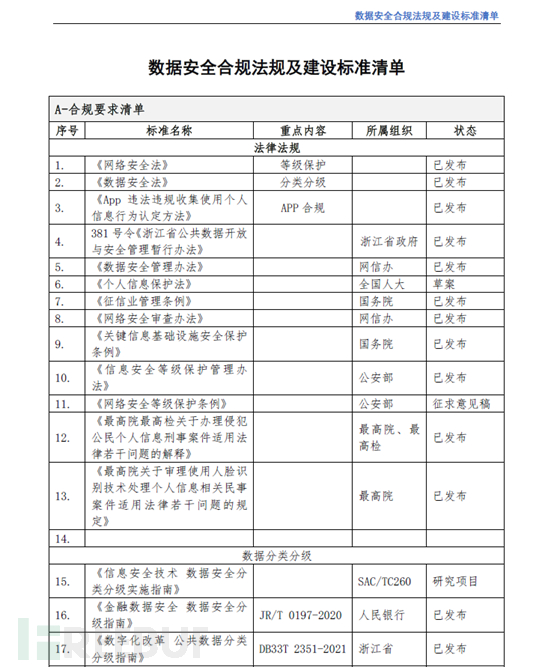
Security compliance system
The significance of the compliance management system
Currently, the construction of information security in the market is often difficult to unify systematically due to the dazzling variety of commercial product solutions or limited practical experience from '0 to 1'. Self-compliance inspection is an effective reference and measure to promote the systematic construction of information security systems. Because, information security compliance is a comprehensive and standardized system formulated by countless industry professionals and predecessors based on their extensive practical experience in their respective fields.
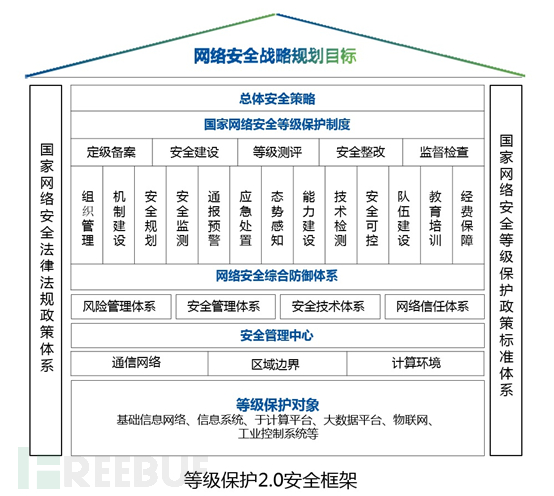
The level protection standard draws on the content of the BS7799 and ISO27001 information security management system, and has been improved in line with the development of China's informatization. In the new level protection standard for network security, it has determined a management strategy based on the principle of 'one center, multiple defenses', which has already become a comprehensive and systematic standard.
Meeting the compliance requirements of the level protection means that the information security management standards behind it need to be introduced. However, the introduction of new perspective management system standards will inevitably conflict with the current enterprise information security framework (or management processes that have been established by convention), but it does not mean that the existing management system needs to be broken. Instead, it can be mutually learned and integrated.
Utilize the management system thought of compliance requirements, correct and supplement the existing management and technical measures, and then adjust and integrate them into the existing system, discard the dregs and keep the essence, and give full play to the effective promotion of the compliance management system to the original enterprise security framework.
The attitude conveyed by compliance
- Ability demonstration: fully demonstrate the company's ability to ensure information security or governance capabilities in a certain aspect, such as data security protection,
- Trustworthy: demonstrate the company's trustworthiness in information security by meeting compliance requirements and providing customers with reliable solutions,
- Information security transparency: gain the trust of customer organizations through the transparency of public white papers, regulatory reports, and information security compliance management,
Focus points of security compliance
Three reasons to persuade the boss to comply with regulations
- Legal risk

- Cost of non-compliance
The penalty intensity for regulatory compliance requirements in China is increasing, including fines not exceeding 10% of annual turnover, business delisting, announcements, and deadline for rectification, and on-site counseling.Public information of Zhejiang Province's administrative penalty resultsIn search of 'cybersecurity' related violations of the obligation to protect cybersecurity and violations of the Regulations on the Administration of Cybersecurity Protection, there were more than 1,200 penalty results in 2021.
- Bringing profit and business operation security to the company
A transparent and comprehensive compliance implementation plan, a certification certificate proving compliance capability, not only can avoid the risk of application delisting and deadline for rectification under regulatory compliance requirements, ensuring business operation. At the same time, it makes information security become one of the attributes of the product or solution itself, wins customer information, and promotes the business operation of the company.
- Implementation plan and cost for compliance needs
A well-implemented implementation plan for compliance work and optimal cost control can enable the boss to better support your compliance management plan (this is a gift).
Incongruous suggestions
1. Left shift of security compliance
Fully understand compliance design and basic requirements, conduct requirement analysis, establish a compliance requirement list, translate laws and regulations or compliance standards, and organize them into technical construction measures or rectification measures that are easy for technical personnel to understand. Add compliance rectification to architecture review work, list it in business system requirement analysis and development process, effectively rely on product managers to join security requirements, provide solutions for R&D personnel, and perfectly integrate into business processes.
2. Understanding compliance awareness
Fully utilize every opportunity to promote and popularize compliance risk, including internal compliance training, architecture and requirement review meetings, and comprehensive risk management strategies. By interpreting the company's strategic needs for compliance, together with the risk compliance department, transform the compliance requirements of information security into a part of comprehensive risk management.
Transform compliance security requirements into special working group requirements, utilizing the effective role of product departments and risk compliance departments to avoid direct conflicts with the research and development department, and better promote compliance management.
3. Self-assessment ability of compliance maturity
Based on compliance management experience, organize detailed self-assessment checklists for self-evaluation, which can not only discover gaps but also effectively identify prominent risk issues at the current stage, enriching the compliance management plan.
4. Third-party endorsement
Compared with other technical and management measures, authoritative compliance certification certificates are relatively easy to implement, clearer, and more likely to be useful.
5. Information security transparency
The transparency of information security compliance is an effective proof of compliance adherence and security capabilities. Certification certificates, compliance management plans, privacy terms, data protection agreements, data transparency reports, risk assessment reports, etc.
Challenges of compliance management
Commonly held misconceptions about equal protection compliance
1. The most important principle of enterprise safety construction is the 'synchronous planning and construction' of the system and security. However, at present, most enterprises do not consider legal compliance as an equally important requirement at the stage of IT architecture design or enterprise information security framework design. Professional technical personnel with experience in legal compliance management and technical practice are still lacking in most enterprises. In terms of compliance management, it is often implemented by personnel with single-side experience in legal affairs, internal audit management, or security operation and maintenance, etc. Even situations such as the lack of security management personnel participating in the ISO27001 certification process occur. Due to the lack of comprehensive safety and compliance management experience of personnel themselves, the system of compliance management has not been integrated into the construction of enterprise safety management. As a result, the level of enterprise compliance management construction is low, and there is often the concept of 'spending money to get a certification'.
2. For example, in the level protection compliance market, it is not excluded that some testing and certification institutions, taking the qualifications recommended by level protection certification institutions as their own, or the market cake is relatively large, and their own project scheduling is relatively tight, they cannot carry out level protection testing work in the whole process of testing projects. The publicity and training of enterprises' level protection work is almost non-existent, the project implementation is rushed, often only three or four days on-site testing, and the beginning and end are rushed, the mode and flow are intensified, and it is impossible to understand the enterprise's network and business architecture. The technical level of on-site testing personnel and the quality of testing are both low. They follow the evaluation guidance manual blindly, and it is impossible to assess the applicability of clauses to specific network business environments. The judgment is too rigid, and the risk mitigation and risk assessment of existing measures are inaccurate.
3. Management system relies entirely on compilation
4. The reference value of rectification suggestions to enterprises is relatively low. In terms of technical measures or management processes, the difficulty of rectifying the current situation is great. Enterprises lack safety management awareness and compliance awareness. In addition, there is a natural psychological confrontation between the testing party and the tested party, which leads to the rectification and reinforcement suggestions being in name only.
5. The understanding of equal protection compliance by enterprises is limited to 'spending money to get a certificate' and 'buying equipment'.
Only fragments of words, summarizing and deducing, cognitive limitations, cannot be fully trusted. Subsequent thinking continues on how to implement effective compliance self-assessment.
评论已关闭